Introduction: The Evolving Threat Landscape
As cryptocurrency adoption continues its upward trajectory in 2025, the methods employed by malicious actors to defraud digital asset holders have grown increasingly sophisticated. Among the most significant and persistent threats is the proliferation of fake crypto wallets. These are not rudimentary scams; they are often cleverly designed malicious applications and elaborate phishing schemes aimed at a singular goal: stealing your cryptocurrency. This report provides an in-depth understanding of these fraudulent wallets, offers real-world examples and visual aids to help identify them, and outlines crucial steps to safeguard your digital assets.
Understanding the Mechanics of Fake Crypto Wallets
Fake crypto wallets are deceptive tools, whether in the form of software applications or fraudulent websites, that expertly mimic the appearance and functionality of legitimate cryptocurrency wallet services. Their core purpose is to deceive users into divulging critical information or granting unauthorized access. The primary mechanisms through which they operate include:
- Seed Phrase Theft: Designed to trick users into entering their private seed phrase (also known as a recovery phrase), giving scammers full access to the associated wallet and its funds.
- Transaction Hijacking: Intercepting and altering transaction data, redirecting cryptocurrency transfers to wallets controlled by the attackers.
- Clipboard Monitoring: Surreptitiously monitoring the user’s clipboard activity to capture copied wallet addresses or private keys, which are then replaced with the scammer’s address during a transaction.
- Direct Fund Drainage: Gaining sufficient permissions or information to directly access and drain cryptocurrency balances from the user’s legitimate wallet.
Real-World Examples and Visual Identification
Understanding how these scams manifest in reality is key to avoiding them.
1. Phishing Emails Impersonating Wallet Providers
A common tactic involves sending emails that appear to originate from reputable cryptocurrency exchanges or wallet providers.
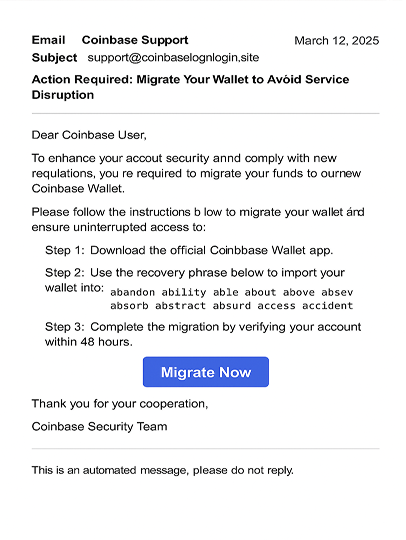
- Scenario (March 2025): Users reported receiving emails seemingly from “Coinbase.” These emails created a sense of urgency, prompting users to “migrate their funds” to a purported new, more secure wallet. Crucially, these emails often provided a 12-word recovery phrase and instructed users to import it into their existing Coinbase Wallet. The design, language, and branding elements were meticulously crafted to mirror authentic Coinbase communications, making them highly deceptive.
- Tech Insight: These phishing campaigns rely on several deceptive elements:
- Convincing Branding: Use of official logos, colour schemes, and typography.
- Legitimate-Looking Domains: Employing domain names that closely resemble official ones (e.g., coinbaselogin.site instead of coinbase.com).
- Professional Language: Using correct grammar and a formal tone to inspire trust.
- Sample Image: Fake Phishing Email Example A typical fake email might have a subject line like: “Action Required: Migrate Your Wallet to Avoid Service Disruption.” The body of the email would urge immediate action, often featuring a prominent button labelled “[Migrate Now]” that links to a malicious website designed to steal credentials or seed phrases.
2. Malicious Mobile Apps Resembling Popular Wallets
Cybersecurity researchers consistently identify fake crypto wallet applications, even on official app stores, that impersonate well-known and trusted wallets.
- Scenario: Malicious apps have been found mimicking popular wallets such as Jaxx Liberty or Coinbase Wallet. Once installed, these apps often request an unusually broad range of permissions (e.g., access to SMS messages, camera, and contacts) that are not necessary for legitimate wallet functionality. Their primary aim is to steal users’ seed phrases or other sensitive data entered into the fake app.
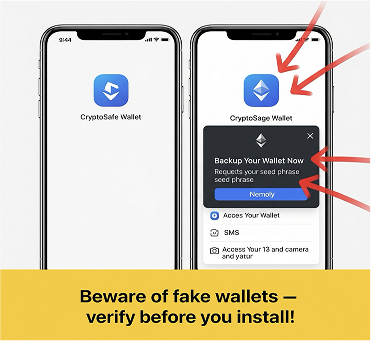
- Visual Example: Spotting a Fake Wallet App Imagine comparing two wallet apps on a mobile phone screen:
- Legitimate App: Features a distinct blue icon, clearly labelled “CryptoSafe Wallet.” It operates smoothly and requests only essential permissions.
- Fake App: Displays a nearly identical blue icon but with a slight name variation, such as “CryptoSage Wallet.” Upon opening, this fake app might immediately display a pop-up: “Backup Your Wallet Now!” aggressively prompting the user to enter their seed phrase. Arrows or visual cues could highlight the fake app’s excessive permission requests (e.g., for SMS and camera access) during its installation or first run, which are red flags. A warning banner at the bottom might read: “Beware of fake wallets — verify developer and reviews before you install!”
Comprehensive Guide to Protecting Yourself
Vigilance and adherence to best practices are paramount in protecting your digital assets from fake crypto wallet scams.
- Download from Official Sources Only:
- Action: Exclusively install wallet applications from official app stores (Google Play Store, Apple App Store) or directly from the verified, official websites of the wallet developers.
- Rationale: Official platforms have vetting processes, reducing (though not eliminating) the risk of malicious apps.
- Verify App Authenticity Thoroughly:
- Action: Before downloading any wallet app, meticulously check the developer’s information. Look for a history of reputable apps, a professional website, and clear contact information. Read user reviews critically, looking for patterns of suspicious behaviour or complaints. Pay attention to the number of downloads and the overall rating, but be aware that these can sometimes be manipulated.
- Rationale: Scammers often create fake developer profiles or use names very similar to legitimate ones. Due diligence here is crucial.
- Exercise Extreme Caution with Emails and Messages:
- Action: Never click on unsolicited links or download attachments in emails, SMS messages, or direct messages on social media, especially if they pertain to your cryptocurrency accounts or wallets. Be wary of messages creating a false sense of urgency.
- Rationale: These are primary vectors for phishing attacks designed to lead you to fake login pages or malicious software downloads.
- Guard Your Seed Phrase Religiously:
- Action: Your seed phrase (or recovery phrase) is the master key to your cryptocurrency. NEVER share it with anyone, under any circumstances. NEVER enter it on any website or application unless you are 100% certain it is the legitimate wallet recovery process on your own trusted device. Be suspicious of any platform or person requesting it.
- Rationale: Anyone who has your seed phrase has complete control over your crypto assets.
- Enable and Utilize Two-Factor Authentication (2FA):
- Action: Wherever possible, enable 2FA (preferably using authenticator apps like Google Authenticator rather than SMS-based 2FA which is less secure) for your crypto exchange accounts and any online services connected to your finances.
- Rationale: 2FA adds a critical layer of security, requiring a second form of verification beyond just your password, making it significantly harder for attackers to gain unauthorized access even if they obtain your login credentials.
- Bookmark Official Sites:
- Action: Access your crypto exchange accounts and web wallets by typing the official URL directly into your browser or using pre-saved bookmarks. Avoid using search engines to find these sites each time, as they can sometimes display links to phishing sites.
- Rationale: This prevents you from accidentally navigating to imposter websites.
Reporting Suspected Scams: Taking Action
If you encounter a fake crypto wallet, a phishing attempt, or unfortunately fall victim to such a scam, reporting it is crucial. This helps authorities track and combat these fraudulent activities and can prevent others from being victimized.
- FTC (Federal Trade Commission): Report general online fraud at https://reportfraud.ftc.gov
- CFTC (Commodity Futures Trading Commission): For fraud related to commodity futures, including some cryptocurrencies, file a complaint at https://www.cftc.gov/complaint
- SEC (U.S. Securities and Exchange Commission): If the scam involves securities (some digital assets may be classified as such), report it via the SEC’s TCR (Tips, Complaints, and Referrals) portal: https://www.sec.gov/tcr
- Internet Crime Complaint Centre (IC3): A partnership between the FBI and the National White Collar Crime Centre, for reporting any cybercrime: https://www.ic3.gov/Home/FileComplaint
- You’re Local Police Department: Report the crime locally, providing them with all relevant details, screenshots, and transaction IDs, and communication records. This is especially important for potential fund recovery efforts, though often challenging.
- To the Platform/App Store: Report malicious apps to Google Play Store or Apple App Store. Report phishing websites to browser vendors (Google Safe Browsing).
Staying Informed: The Power of Continuous Learning
The cryptocurrency landscape and the tactics used by scammers are constantly evolving.
- Follow Reputable Sources: Stay updated by following trusted cybersecurity news outlets, official blogs of wallet providers and exchanges, and respected figures in the crypto security community.
- Engage with Communities: Participate in (or at least monitor) reputable online cryptocurrency forums and communities where users often share information about emerging threats and security best practices.
- Educate yourself and others: The more you understand about potential threats, the better equipped you’ll be to avoid them. Share your knowledge with friends and family involved in cryptocurrency to help create a safer environment for everyone.
Conclusion: Vigilance as Your Best Defence
Fake crypto wallets represent a serious and adaptable threat within the digital asset ecosystem. However, by understanding their operational methods, learning to recognize the warning signs, and consistently applying robust security practices, users can significantly mitigate their risk. Staying vigilant, continuously educating oneself, and promptly reporting suspicious activities are the cornerstones of protecting your valuable cryptocurrency holdings in 2025 and beyond.