Introduction
In the ever-evolving landscape of cybersecurity threats, computer worms remain among the most insidious forms of malware. Unlike viruses, worms do not require user interaction to spread—they exploit vulnerabilities and move stealthily across networks.
This report investigates a specific worm, Worm.WIN32.Canbis, analyzing its behavior, infection strategy, and potential impact through static and dynamic inspection. The findings highlight how easily this worm replicates and evades detection, offering important insights for malware analysts and cybersecurity professionals.
Worm.WIN32.Canbis is a type of worm which is a malicious software.
A computer worm is a type of malware whose primary function is to self-replicate and infect other computers while remaining active on infected systems.
A computer worm duplicates itself to spread to uninfected computers. It often does this by exploiting parts of an operating system that are automatic and invisible to the user.
Typically, a user only notices a worm when its uncontrolled replication consumes system resources and slows or halts other tasks.
Computer worms often rely on vulnerabilities in networking protocols, such as File Transfer Protocol, to propagate. After a computer worm loads and begins running on a newly infected system, it will typically follow its prime directive: to remain active on an infected system for as long as possible and spread to as many other vulnerable systems as possible.
What is the execution flow of this malware?
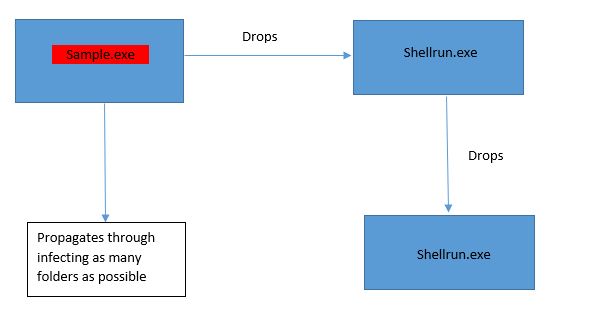
What is the propagation strategy used by this worm?
The worm follows a predictable yet dangerous loop:
- Sample.exe is executed.
- It drops shellrun.exe in SysWOW64.
- Shellrun.exe infects folders and replicates itself.
- The original file is then deleted to avoid detection.
This loop ensures the worm spreads widely and remains hidden from unsuspecting users.
What is the file info?
File name: 58d55ec4704abf99e7399488d279cefc.bin.exe
MD5: 58d55ec4704abf99e7399488d279cefc
SHA-1: 115e17a268e4273963d600382cb45d9cacdced90
SHA-256: 963efa12cafa59dc07e00f0e937968a3761b3b3267f22c165842a09012645dbe
Imphash: dd7fe15a2b88e6524b745ee379d33216
Size: 6,975 KB
Compiler: Borland Delphi
What can static analysis reveal about this malware?
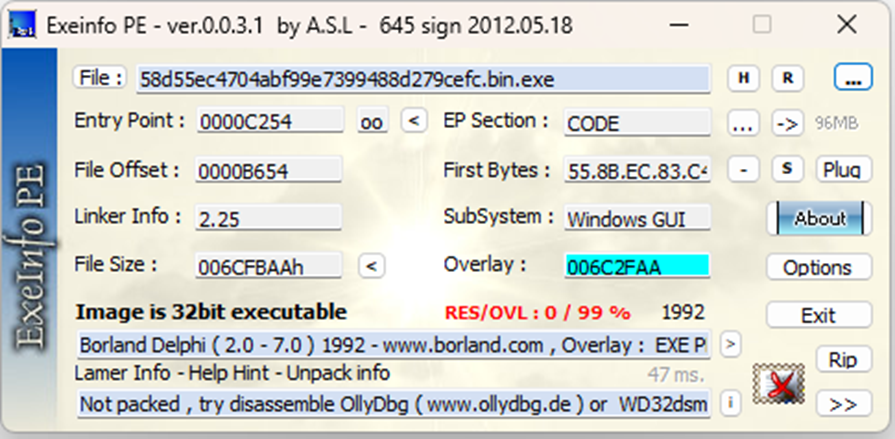
Static analysis tells us that the sample has an overlay value as 0x006C2FAA. This overlay part can contain some malicious code.
What does dynamic analysis reveal about the malware’s behavior?
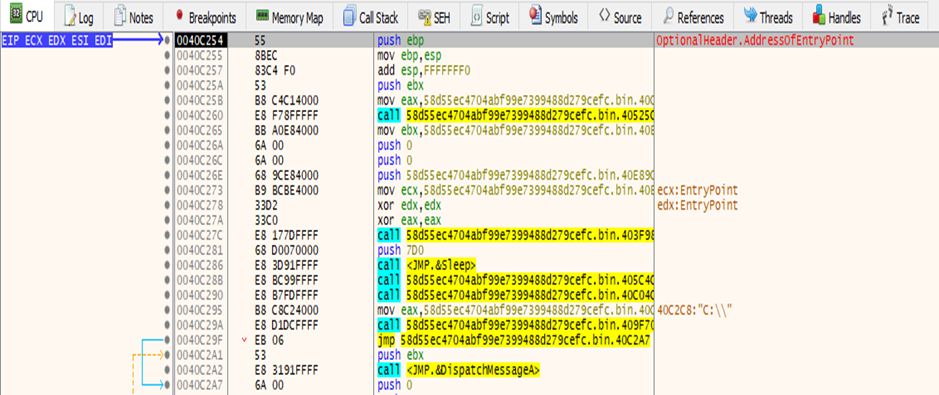
Entry point for the file is at 0x0040C254. So the code execution starts at this address as shown in the figure.
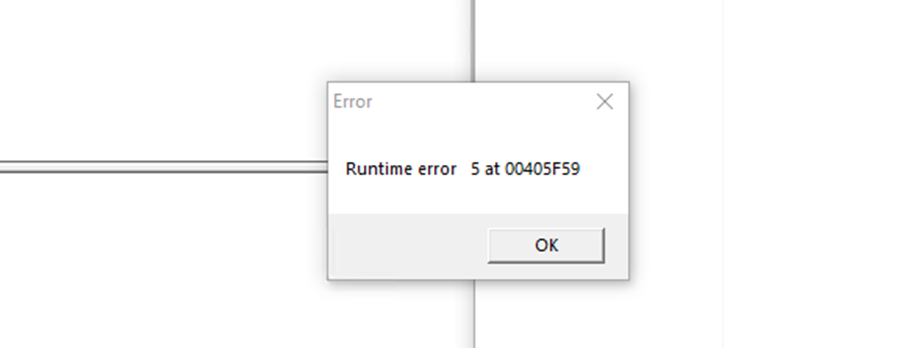
When the sample is run, the above dialog box appears. This could be misleading as the actual infection could still be happening in the background in spite of the error.
What files does the malware drop during infection?
C:\Windows\SysWOW64\shellrun.exe
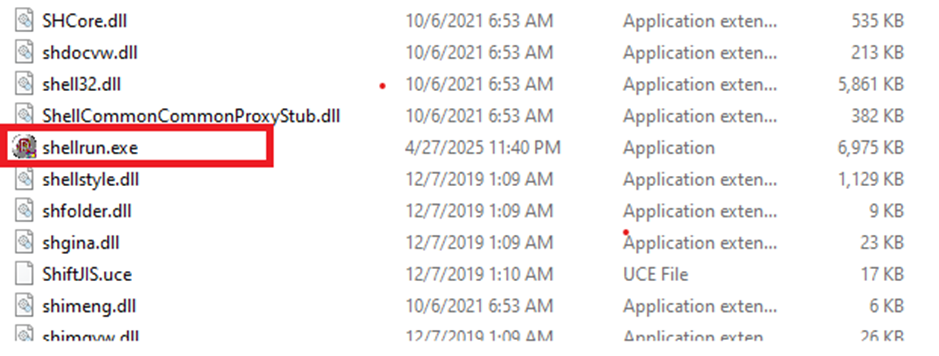
Folder Infected:
Worm is trying to propagate through the machine by infecting as many folders as possible. In the above figure it is clearly seen that the worm has infected exe files in the 7-Zip folder.
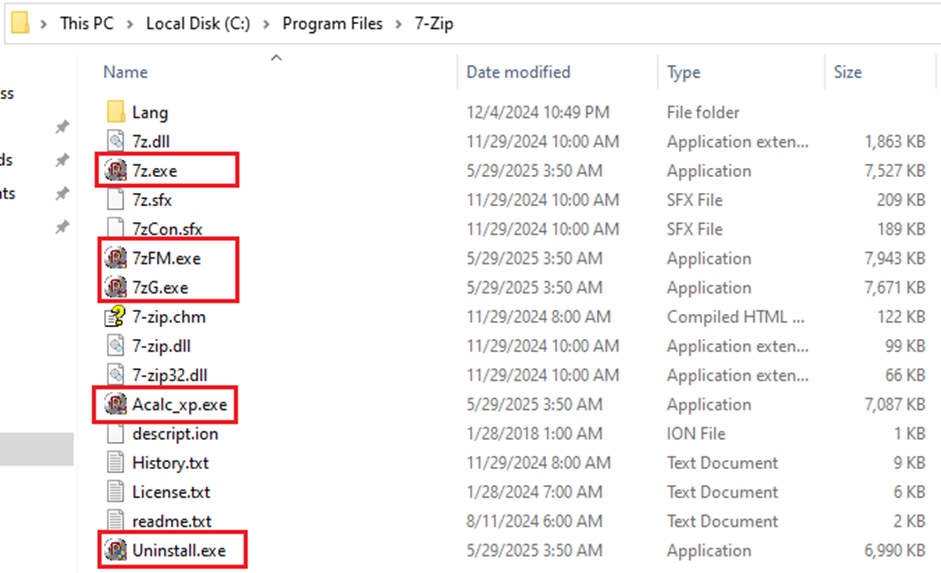
Following is the screenshot of 7-zip folder before infection:
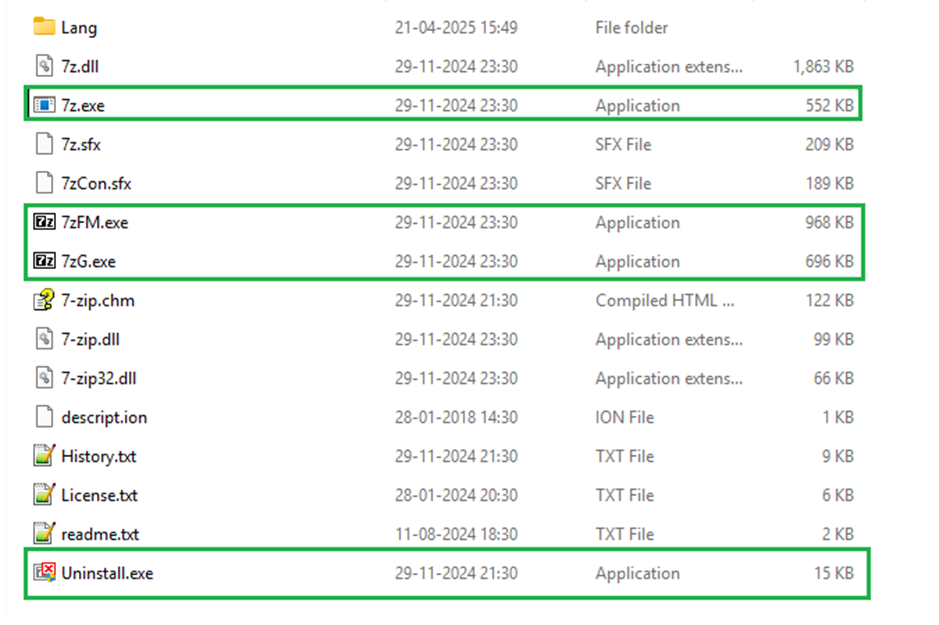
Following is the screenshot of 7-zip folder after the infection:
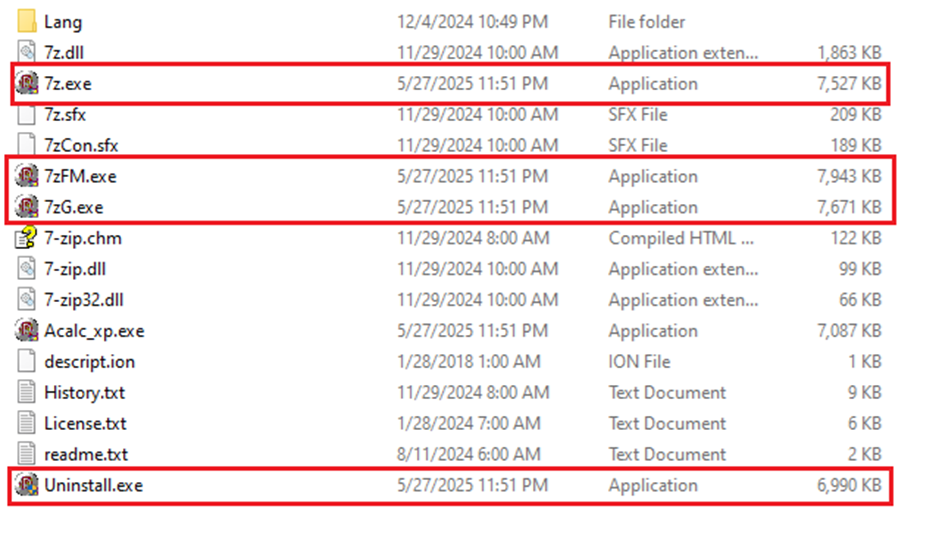
Notice the size change of the files after infection.
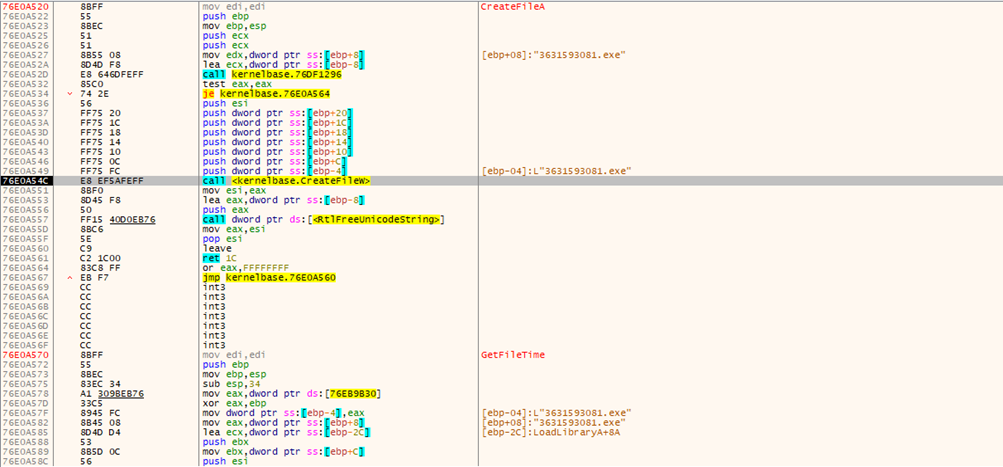
Worm sample is creating a new file. This new file will be dropped at a different path once the creation process is complete.
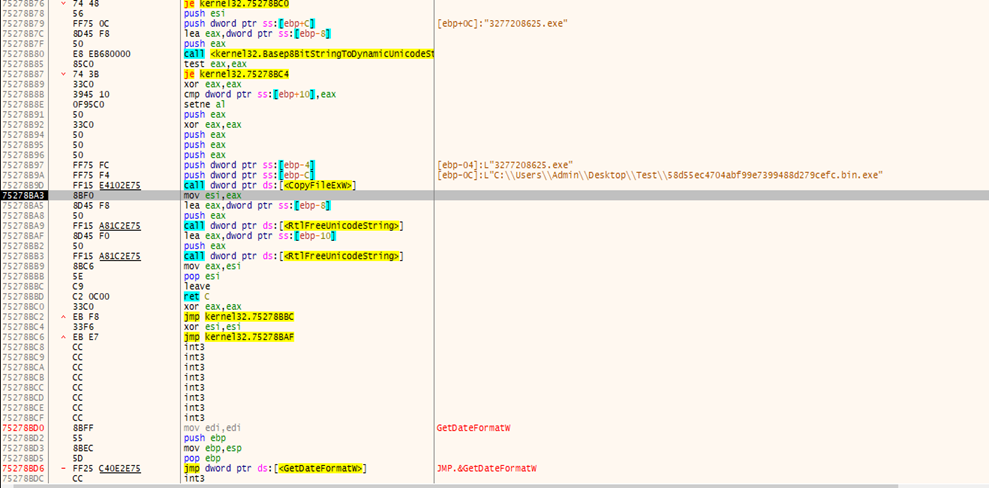
The contents of the original sample are getting copied into the newly created file.
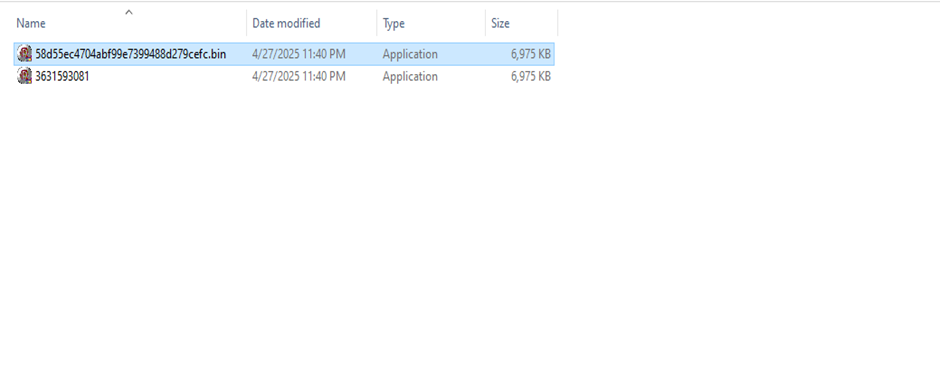
The new file is dropped in the same folder in which the original sample is present.
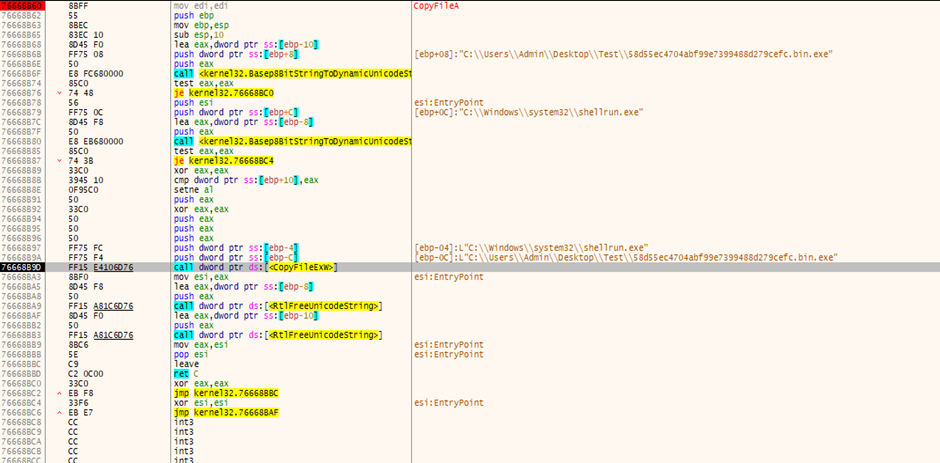
The new file which was created is getting copied to path “C:\Windows\SysWOW64\”
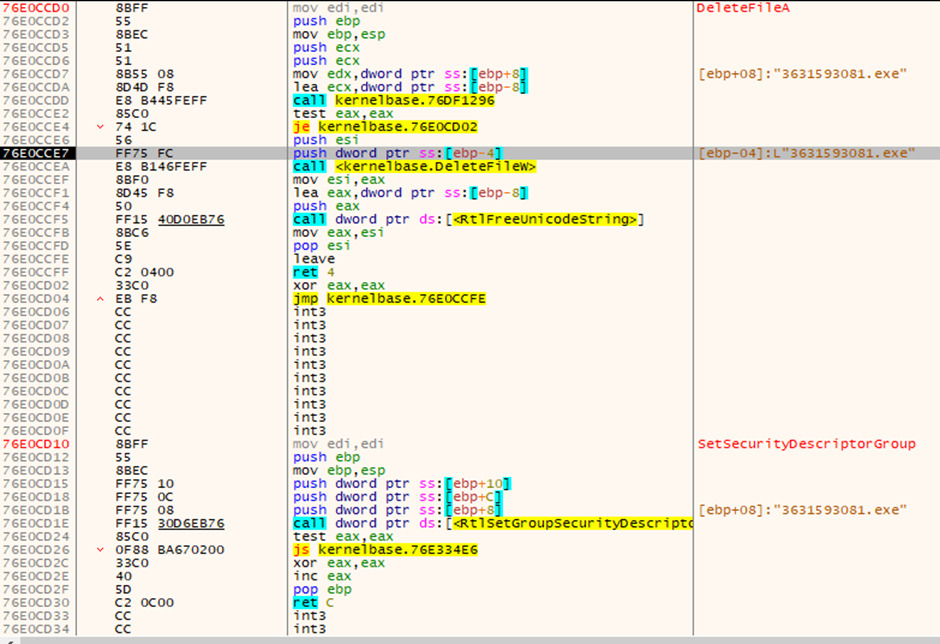
After creating and copying the new file, into the intended directory, the file is being deleted, so that the user does not come to know about infection.
Network activity:
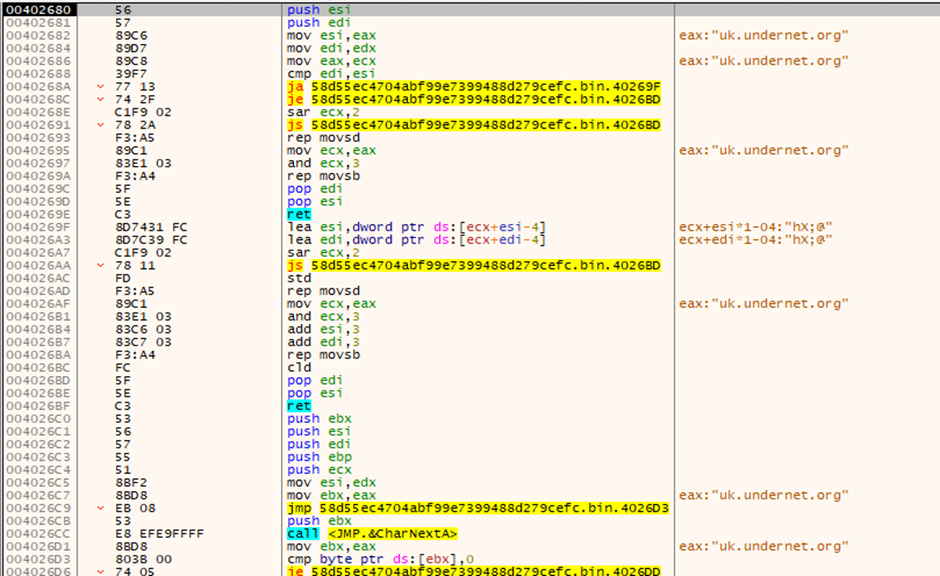
The sample tries to connect with the “uk.undernet.org” URL and tries to download malicious content.
This suggests it may be trying to connect to a Command and Control (C2) server to download additional payloads or receive instructions—raising concerns about potential remote control or data exfiltration.
What are Indicators of Compromise (IoCs)?
Key behavioral indicators
- Displays misleading error dialog upon execution.
- Drops a copy of itself (shellrun.exe) into the Windows system directory.
- Infects .exe files in local folders to propagate.
- Deletes evidence (original infected file) after replication.
- Creates and copies files stealthily to system folders.
- Increases file size of legitimate executables post-infection.
What’s the best way to protect against worms like Canbis?
Avoiding infection requires a combination of strong technical defences and cautious user behavior:
- Use reliable antivirus and anti-malware solutions with real-time protection.
- Be skeptical of suspicious emails, links, and downloads, especially from unknown sources.
- Avoid using untrusted P2P file-sharing networks.
- Keep your operating system and software updated to patch known vulnerabilities.
Conclusion:
Worm.Win32.Canbis is a clear reminder that malware continues to evolve with stealthy infection tactics and self-replication strategies. Its ability to silently drop files, infect folders, and communicate with external servers makes it a serious threat. Understanding its behavior through detailed analysis, as presented in this report, empowers cybersecurity professionals to detect, prevent, and respond more effectively to such threats.
Staying informed, vigilant, and proactive remains the best defence in an increasingly interconnected digital world.