
Introduction
In the ever-evolving world of cybersecurity, certain tools stand out—not only for their technical prowess but also for the widespread impact they have in the hands of attackers. AsyncRAT is one such tool. Originally developed as a legitimate remote administration tool, AsyncRAT has become one of the most notorious Remote Access Trojans (RATs) due to its misuse by cybercriminals around the globe.
What Is AsyncRAT?
AsyncRAT stands for Asynchronous Remote Access Trojan. It is an open-source tool, developed in C# using the .NET framework, and intended for remote administration and management of Windows machines. AsyncRAT enables a user to control a Windows system remotely and silently—making it extremely useful for legitimate IT tasks such as troubleshooting, file management, and system monitoring. However, its very capabilities and free availability have made it a favourite for cybercriminals, who weaponized it to compromise victims’ machines.
Technical overview:
- Compiler: Written in C# using the .NET framework
- Platform: Windows
- Communication: Asynchronous sockets, encrypted communication
Though it was released as a legitimate remote admin tool on GitHub, it is widely used in malicious campaigns.
What Are Key Features of AsyncRAT?
AsyncRAT comes packed with features that allow attackers extensive control and surveillance capabilities:
- Remote Desktop Viewing: Attackers can watch the victim’s screen in real time, allowing them to interact with the system as if physically present.
- Keylogging: Records keystrokes to steal passwords, credit card numbers, and other sensitive information.
- Process Manager: View and terminate running processes on the infected system, allowing attackers to disable security software.
- File Manager: Upload, download, delete, or execute files remotely, enabling data theft or additional malware deployment.
- Remote Shell/Command Execution: Execute system commands silently to control or manipulate the system remotely.
- Dynamic DNS and Port Forwarding Support: Allows attackers to bypass network restrictions and maintain stable communication channels.
- Encrypted Command & Control (C2) Communication: Uses SSL/TLS encryption to evade network detection tools and intercept attempts.
These robust features make AsyncRAT a powerful and stealthy tool for attackers.
How Does AsyncRAT Work?
The tool follows a client-server model:
- Attacker Setup: The attacker sets up a control server using the AsyncRAT interface.
- Payload Generation: A malicious payload (the AsyncRAT client) is created and disguised as a legitimate file (e.g., PDF, EXE, DOCX).
- Delivery: This payload is delivered to victims via phishing emails, fake installers, or malicious ads.
- Infection: When the victim opens the file, the malware installs silently, establishes persistence, and connects back to the attacker’s server.
- Command & Control: The attacker can now monitor, manipulate, and control the infected system remotely.
Why Is AsyncRAT Dangerous?
While AsyncRAT itself isn’t inherently malicious (being open-source), its capabilities make it ideal for:
- Stealing credentials and sensitive data
- Spying on users
- Controlling infected systems for botnets
- Delivering secondary payloads (like ransomware)
What Are the Advanced Capabilities of AsyncRAT?
Beyond the basic functionalities, AsyncRAT also supports more advanced techniques that enhance its stealth and effectiveness:
- Anti-Analysis Techniques: AsyncRAT can detect virtual machines or debugging tools to avoid analysis by security researchers.
- Process Injection: It can inject its code into legitimate system processes to hide its presence.
- Self-Deletion: Ability to remove its own files after execution to cover tracks.
- Multiple Payload Support: Attackers can deploy several payloads in sequence or simultaneously for complex attacks.
- Customizable Build: Attackers can easily modify source code to change network ports, encryption keys, or features to evade antivirus signatures.
How Does AsyncRAT Spread?
AsyncRAT infection vectors are varied but primarily rely on social engineering and malware delivery techniques:
- Phishing Emails: The most common vector. Emails with malicious attachments (Word, Excel files with macros) or links leading to payload downloads.
- Fake Software and Updates: Attackers disguise AsyncRAT as legitimate software installers or updates.
- Malicious Macros: Embedded in office documents, macros trigger AsyncRAT installation once enabled.
- Exploit Kits: Targeting vulnerabilities in browsers or plugins to deliver AsyncRAT silently.
- Drive-by Downloads: Compromised websites push AsyncRAT payloads when users visit.
- Social Media and Messaging Apps: Malicious payloads are increasingly shared via social media platforms, chat apps, or collaboration tools.
- USB Drives and Physical Media: Attackers may distribute AsyncRAT through infected removable drives for air-gapped or offline targets.
What Are Indicators of Compromise (IOCs)?
Detecting AsyncRAT infections early is critical. Common IOCs include:
- Unexpected outbound encrypted connections on unusual ports.
- Presence of unknown or suspicious processes running on Windows machines.
- Strange entries in the Windows registry related to startup or persistence.
- Unusual file modifications or new files in system folders.
- Keyloggers or unusual CPU/network usage spikes.
- Unexpected popup windows or desktop sharing activity without user consent.
What Are Challenges in Detecting AsyncRAT?
- Encrypted Communications: SSL/TLS encryption masks C2 traffic, making network detection difficult.
- Polymorphism: Frequent changes in the payload code or encryption keys defeat signature-based antivirus detection.
- Fileless Execution: Some variants run entirely in memory, leaving no footprint on disk.
- Legitimate Use Confusion: As AsyncRAT is also a legitimate tool, distinguishing malicious use from authorized admin access is challenging.
Protecting Yourself Against AsyncRAT
AsyncRAT spreads mostly through phishing emails and fake software.
To stay safe:
- Don’t open suspicious email attachments or links.
- Avoid downloading cracked or pirated software.
- Keep your system and software updated.
- Use reputable antivirus with real-time protection.
- Check startup programs for unknown entries.
For businesses:
- Use endpoint detection (EDR) and email filtering.
- Implement application whitelisting to block unauthorized programs.
- Monitor network traffic for unusual connections.
- Train employees to spot phishing and practice good security habits.
Real-World Sightings
AsyncRAT has been discovered in multiple real-world attacks:
- 2023: Targeted phishing campaign impersonating Office365 with malicious invoice attachments.
- 2024: Distributed via Discord links disguised as game cheats.
- 2025: Bundled in fake job application documents sent to HR emails
File Info
File name: 01010101010.exe
File type: Win32 executable for .Net
File size: 66.00 KB
SHA256: d9491200a30cad1086ddae181059ba0b91d58de5cd0ea8eb86a0c77f665cb8b3
SHA1: f8e3733cc054bd6ca7da9527638a13a88d2b2711
MD5: 77f76c3cb2a98abeec8c42e41ba67712
Static Analysis
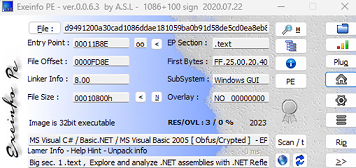
Preliminary analysis using ExeinfoPE indicated that the file is compiled as a .NET application.
Dynamic Analysis
It sets up all the predefined and hardcoded parameters that were configured at the time of payload creation.
What Is AsyncRAT’s Main Function?
The main function in AsyncRAT manages module loading, settings, and code flow. A configurable delay function introduces a sleep interval (e.g., 3–10 seconds) before execution during payload generation.
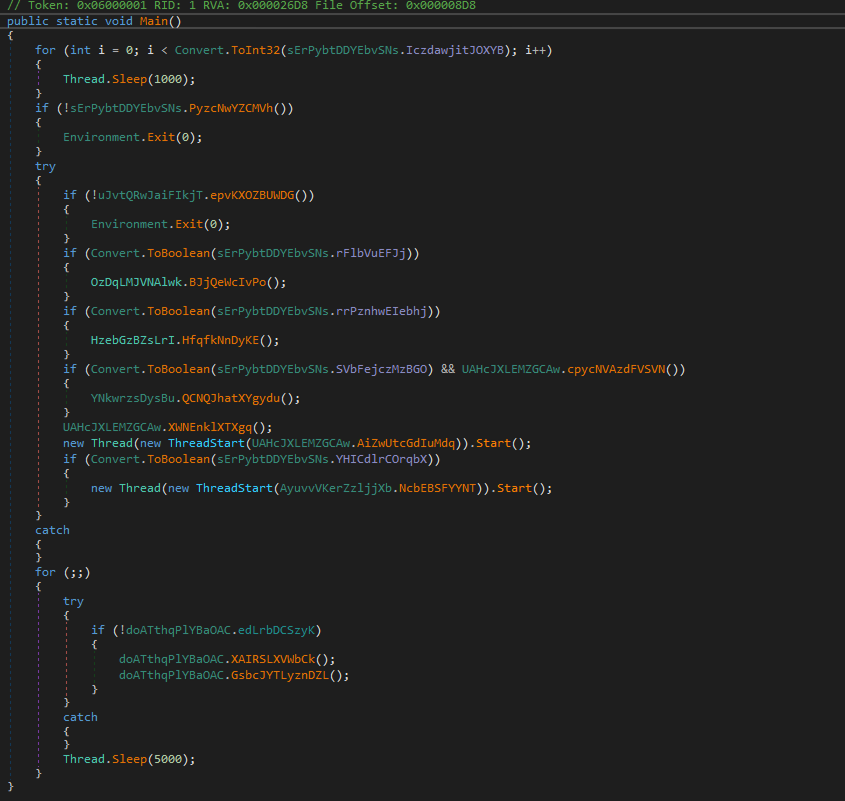
Serving as the entry point, this main function calls a secondary function that sets up the payload’s configuration
Decryption of all configuration settings from the AES256 algorithm:
This function, Initialize Settings, not only sets up configurations but also decrypts them using the AES-256 encryption algorithm
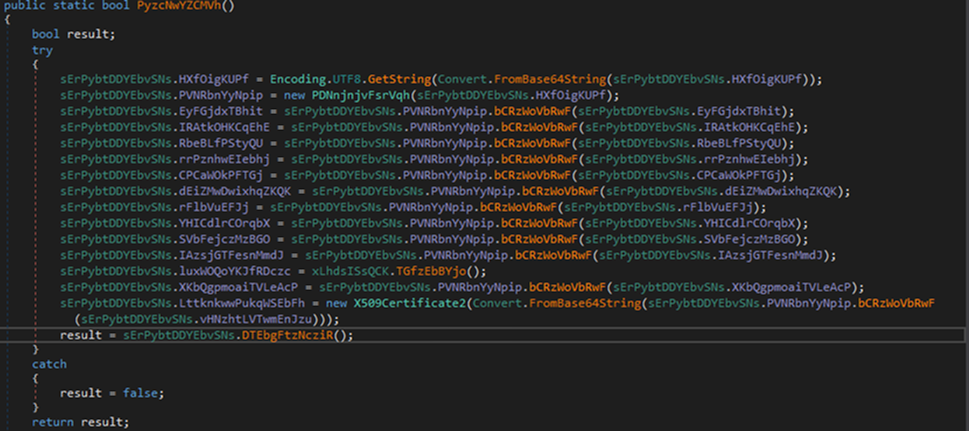
Above Function is in encrypted format here is decrypted version of this
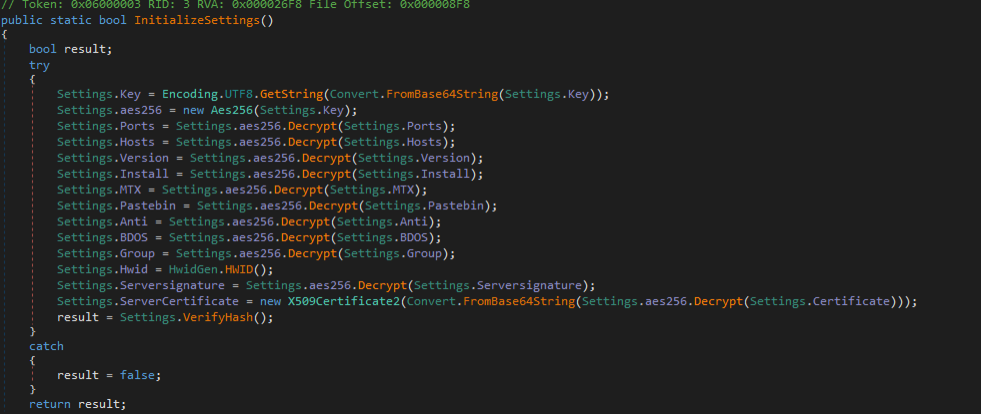
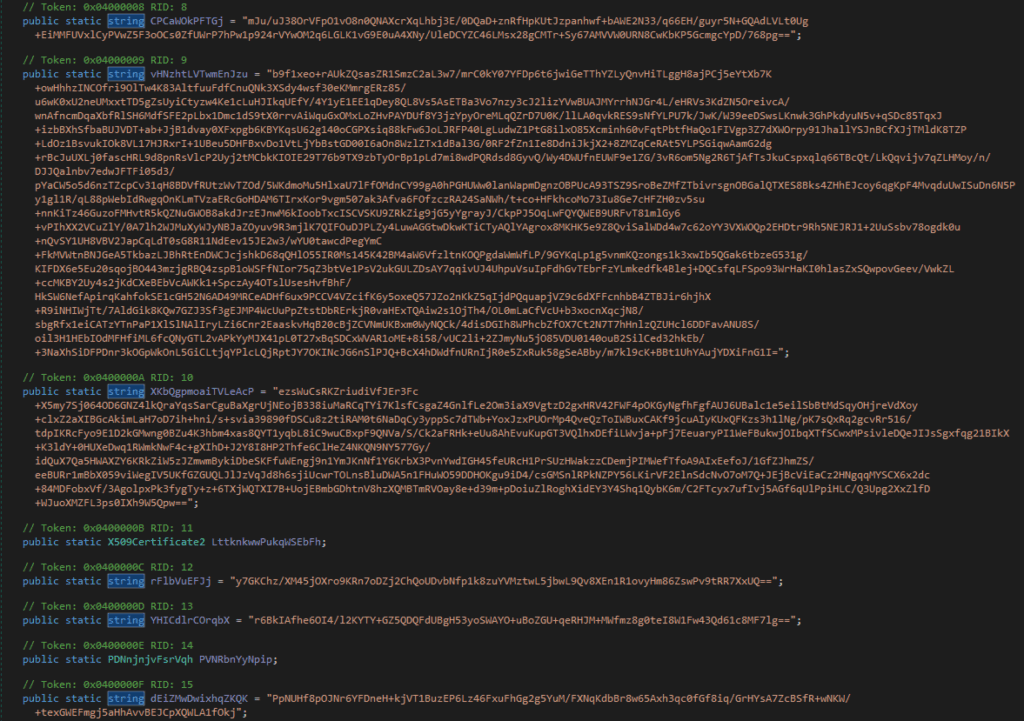
Within the above function, these configuration settings are defined:
| Key | BdPbgcbtbthQvXG8YPFzT7T3vvtatlnx |
| Ports | null |
| Hosts | false |
| Version | “AWS | RxR “ |
| Install | False |
| MTX | “AsyncMutex_2121201201201201201011111101010101010101010101010101010101010000000000000000000000000000101111” |
| Pastebin | “https://pastebin.com/raw/pjUuZwd8” |
| Anti | false |
| BDOS | true |
| Group | false |
| HWid | “Paste.Rs” |
| SeverSignature | “6A73BF4AAA8CBBC3D180” |
Pastebin platforms allow users to share plain text, such as code or logs. These services are sometimes exploited by threat actors to host malicious payloads or stolen data.
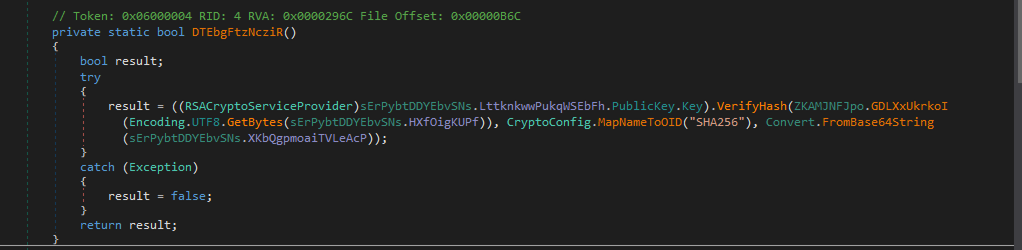
Function to Validate Hash Integrity
Using the server certificate and signature, the Verify Hash function validates whether the configurations are authentic.
Connecting with Client:
By using the WebClient.DownloadString API, AsyncRAT can obtain extra resources and payloads from Pastebin and other domains. Figure displays the corresponding code for connecting to a domain via a given port.
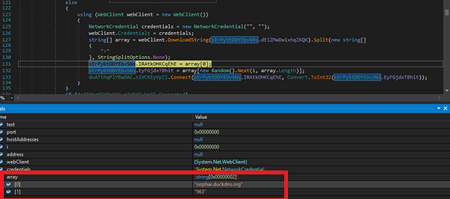
As shown in the figure, the array holds both the Pastebin link and the port value
Conclusion
AsyncRAT exemplifies how legitimate tools can be repurposed for malicious use, posing serious threats to individuals and organizations alike. Awareness, proactive defences, and timely detection are crucial to mitigating its risks.