Introduction
A dangerous malware family known as BADBOX 2.0 has been flagged by the FBI as a global cybersecurity threat. This Android-based malware infiltrates cheap IoT devices—such as smart TVs, streaming boxes, tablets, and IoT gadgets—turning them into malicious proxies and part of a residential proxy botnet used for criminal operations. Over 1 million devices are already compromised worldwide.
BADBOX 2.0 is stealthy and highly effective in its infection strategy. Unlike traditional malware, BADBOX is frequently pre-installed in the firmware of low-cost devices. This means users can be compromised right out of the box without taking any direct action.
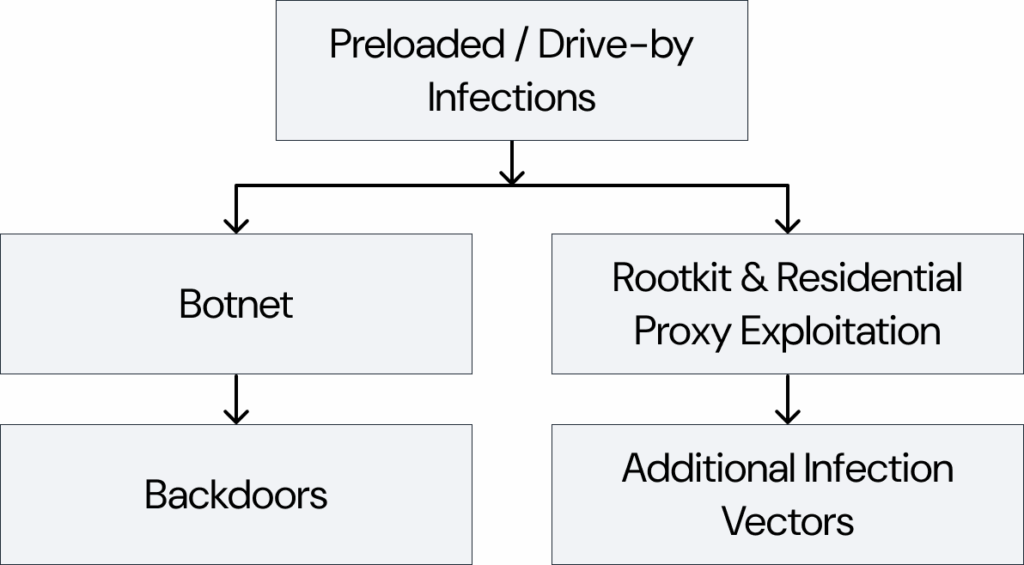
How BADBOX 2.0 Operates
Preloaded & Drive-By Infections
- Many devices are compromised before shipment, with malware embedded in firmware.
- Users unknowingly purchase pre-infected devices already part of the botnet.
- Other infections occur during setup, via third-party app stores or drive-by downloads from malicious websites.
Botnet & Residential Proxy Exploitation
- Infected devices act as proxy nodes, routing attacker traffic through user networks.
- These proxies are rented out for malicious activities such as ad fraud, credential stuffing, and anonymous cyber operations.
Stealthy Ad Click Modules
- BADBOX 2.0 hides ad-click fraud code within system components.
- Illicit traffic is generated silently, draining data and bandwidth while earning revenue for attackers.
Backdoors & Multiple Infection Vectors
- BADBOX 2.0 includes persistent backdoors that survive reboots and resets.
- Fake apps may appear in official app stores, loaded with hidden malicious code.
Deep Dive: IOC Example – libanl.so
libanl.so is a native backdoor library embedded in the firmware of infected devices. It is the core malware component responsible for:
- Boot-time execution of BADBOX modules.
- Enabling persistent access for remote attackers.
- Downloading secondary payloads via encrypted C2 instructions.
Technical Behavior
– On boot, the app com.hs.app loads libanl.so.
– The library decrypts and loads p.jar and q.jar into system memory.
– p.jar handles downloading additional malicious modules.
– q.jar maintains malware persistence even after reboots.
– These components initiate Java classes like com.hs.cld.Main and com.hs.q.Main.
– The system then beacons to C2 servers, e.g., catmore88[.]com.
Key IoCs for Detection
| Component | Indicator |
| Native Library | libanl.so |
| Java Modules | p.jar, q.jar |
| Boot Component | com.hs.app |
| C2 Communication | catmore88[.]com, ipmoyu[.]com |
| Strings in Binary | com.hs.cld.Main, /.p.jar |
Signs of Infection
- High CPU usage, overheating, or slow performance
- Unexpected internet activity during idle periods
- Google Play Protect is disabled or missing
- Suspicious marketplace or unknown apps installed
- Using generic-brand devices with unverified firmware
Global Spread & Impact
BADBOX 2.0 has compromised over 1 million consumer-grade devices worldwide. These infections primarily involve low-cost, uncertified Android-based hardware, including generic tablets, connected TV boxes, digital projectors, and other IoT devices.
Such devices are commonly mass-produced and shipped globally through unregulated supply chains. In many cases, the malware is already embedded in the firmware prior to delivery. Analysis of network telemetry linked to BADBOX 2.0 reveals infection activity across 222 countries and territories, highlighting the widespread and indiscriminate nature of this threat.
Protective Measures for Users
- Stick to Official Sources: Buy IoT devices from reputable brands with verified firmware security.
- Update Firmware Regularly: Apply security patches and updates to remove vulnerabilities.
- Monitor Network Traffic: Use your router’s admin dashboard or third-party apps to track suspicious network activity.
- Isolate Suspicious Devices: Keep IoT devices on a separate VLAN or guest network to prevent malware from spreading to laptops or smartphones.
What To Do If You’re Infected
Immediate Steps:
- Disconnect device from all networks
- Perform a factory reset
- Reflash firmware from official vendor sources
- Change passwords for all linked accounts
- Scan network logs for unusual access patterns
- Report the incident
Reporting BADBOX 2.0 Activity
You should report any BADBOX-related incidents to:
- FBI (USA) – Internet Crime Complaint Center (IC3): https://www.ic3.gov
- National CERT Teams – Search “[Your Country] CERT” for cybersecurity reporting details.
- IoT Manufacturers – Send logs, device details, and observed behaviors to the brand’s support team.
- Ad Networks – Report click fraud to platforms like Google AdSense or programmatic ad providers.
- Save Logs – Keep router logs, timestamps, device brand/model, firmware versions, and IP behavior as evidence.
Conclusion
BADBOX 2.0 marks a significant escalation in IoT-focused cyber threats. By silently converting inexpensive consumer devices into components of a global botnet, it enables large-scale fraud, proxy abuse, and anonymous malicious activity. Its ability to remain hidden—often embedded at the firmware level—makes detection and remediation especially difficult.
To mitigate this growing risk, users should remain cautious when purchasing IoT devices, prioritize products with verified security standards, and consistently apply firmware updates. The threat posed by BADBOX 2.0 extends beyond a single compromised device—it’s a broader risk to home networks, enterprise environments, and the global digital ecosystem.



