Introduction:
Our analysis of DragonForce ransomware—designed to encrypt files on compromised systems and demand ransom payments in cryptocurrency (Bitcoin) in exchange for the decryption key—was inspired by the excellent research conducted by Resecurity and Hybrid Analysis.
DragonForce is distributed via phishing emails, malicious websites, or exploiting vulnerabilities in systems.
DragonForce ransomware represents a Ransomware-as-a-Service (RaaS) attack. This ransomware threat actor, known as DragonForce, surfaced in mid-2023 and is believed to have originated from Malaysia. DragonForce employs a multi-extortion strategy, whereby they not only encrypt the data of their victims but also exfiltrate sensitive information.
In early 2025 DragonForce introduced white-label ransomware services under the brand ‘Ransom Bay’. They also attacked major UK retailers including Marks & Spencer, Harrods in April–May 2025.
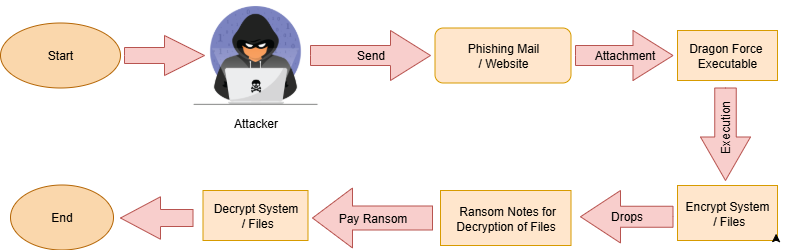
Infection Flowchart:
Technical Analysis:
MD5 : 9db8f7378e2df01c842cfcb617e64475
SHA-1 : eada05f4bfd4876c57c24cd4b41f7a40ea97274c
SHA-256 : c844d02c91d5e6dc293de80085ad2f69b5c44bc46ec9fdaa4e3efbda062c871c
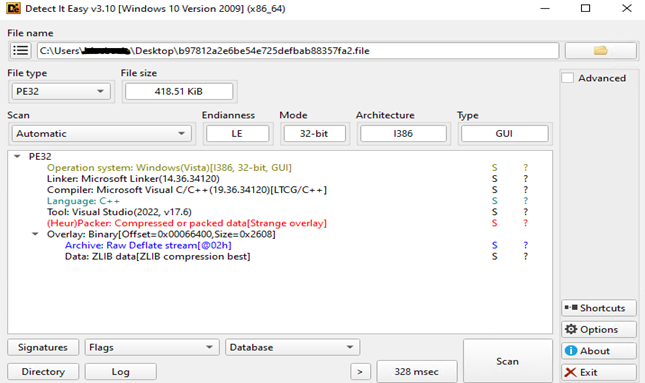
Compiler : 32 bit C++ compiler executable file
Suspicious use of API Call : CreateFileW, CreateMutexA, CopyFileW, Process32NextW, Process32FirstW, FindNextFileW, RegCreateKeyExW, CryptImportKey, CryptEncrypt, CryptGenRandom, RegOpenKeyExW, WriteFile, CreateProcessW.
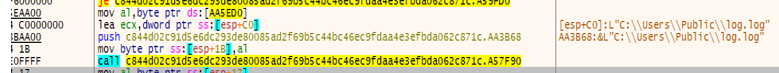
The log file created by ransomware at C:\Users\Public\log.log could potentially serve multiple purposes:
- Tracking Infection Details: It may record details about the victim’s machine, such as the operating system, machine name, IP address, and other identifying features, which help the ransomware operators monitor infected systems.
- Monitoring Encryption Status: The log might track the progress of encryption, including which files or directories were successfully encrypted, any errors encountered, and whether the ransom payment process is proceeding.
- Logging Victim Interactions: If the victim interacts with the ransom note (e.g., trying to communicate with the attackers), the log could capture these actions, which could help guide future communication or attempts to extract payment.
- Debugging and Persistence: For the ransomware operators, this log could provide debugging information, helping them understand if the ransomware successfully encrypted files and if there are issues they need to address in further iterations.
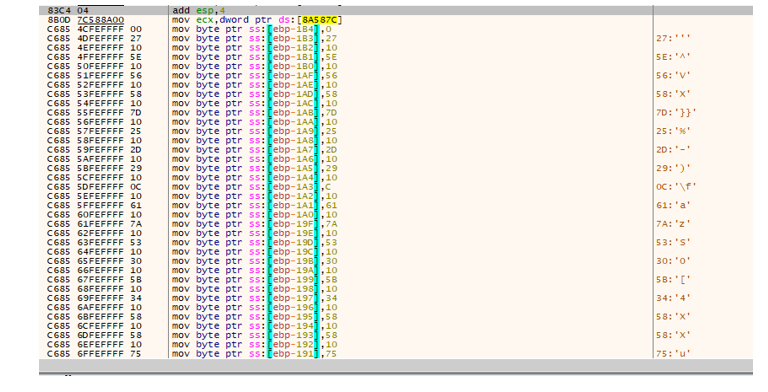
- The DragonForce ransomware binary used stack strings obfuscation technique where encrypted strings are stored on the stack and only decrypted to an array allocated at runtime. This approach helps to evade static analysis and signature-based detection.
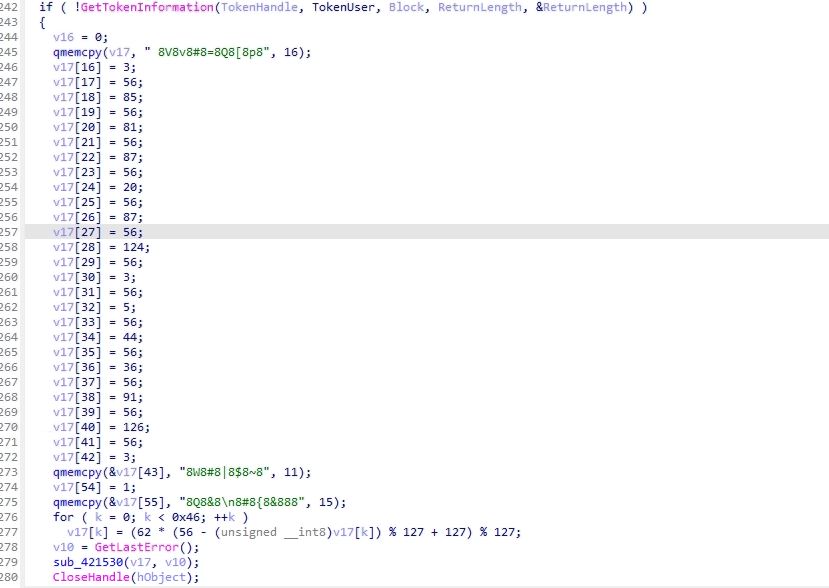
- It generates a unique system ID for the compromised system to store collected information, as shown in the screenshot below. Attacker helps to identify the victim’s machine by unique system ID.
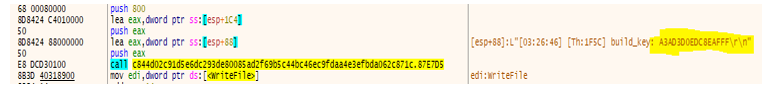
Ransomware often uses the current system time of the victim’s machine for several reasons, which could include:
- System Identification:
The timestamp of the victim’s machine can be used as a unique identifier for that system, especially when combined with other details like IP address or machine name. This helps the attackers track infected systems and may assist in customizing ransom demands based on the time zone or region. - Encryption Time-Stamping:
The current system time might be used to timestamp encrypted files. This could help the attackers keep track of when the encryption took place, making it easier to monitor the victim’s response over time (e.g., how long it takes the victim to pay the ransom). - Time-Based Ransomware Behaviour:
Some ransomware strains use time-based logic, such as delaying certain actions until a specific time or date, or accelerating the encryption process after a certain period. By capturing the system time, the ransomware can act more precisely based on the victim’s clock.
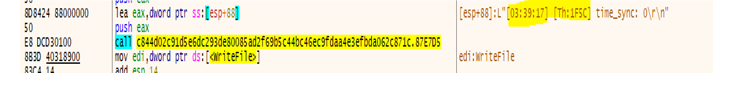
- The ransomware terminates specific processes to prevent file-locking conflicts that would interfere with its encryption routine. The specific list of processes killed is shown in the image below.
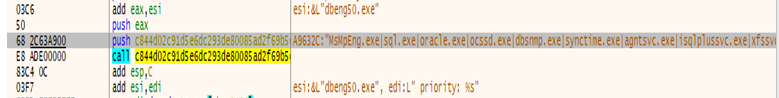
- DragonForce maps multiple DLLs into the address space of the current process using the CreateFileMappingW and MapViewOfFile APIs.
- The DLLs were mapped as kernel32.dll, ws2_32.dll, advapi32.dll, RstrtMgr.dll, ole32.dll, netapi32.dll, IPHLPAPI.dll, shlwapi.dll, shell32.dll, and ntdll.dll. The malware uses the content of those fresh-mapped DLLs as a bypass technique, in order to replace the hooks placed from security vendors in these DLLs.
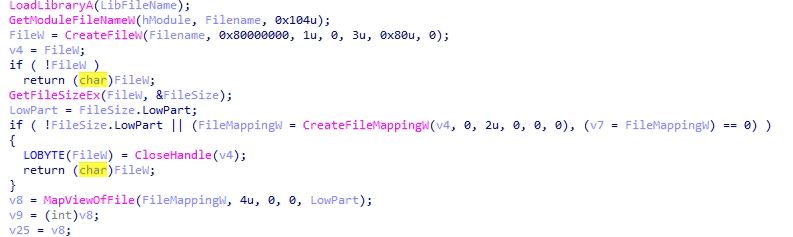
- The Dragonforce verifies if one of the DLLs listed above contains hook functions or not. If present it modifies the protection of the function code to 0x40 (PAGE_EXECUTE_READWRITE) and writes the unhooked code from the fresh-mapped DLLs . It then restores the old memory protection, as below image.
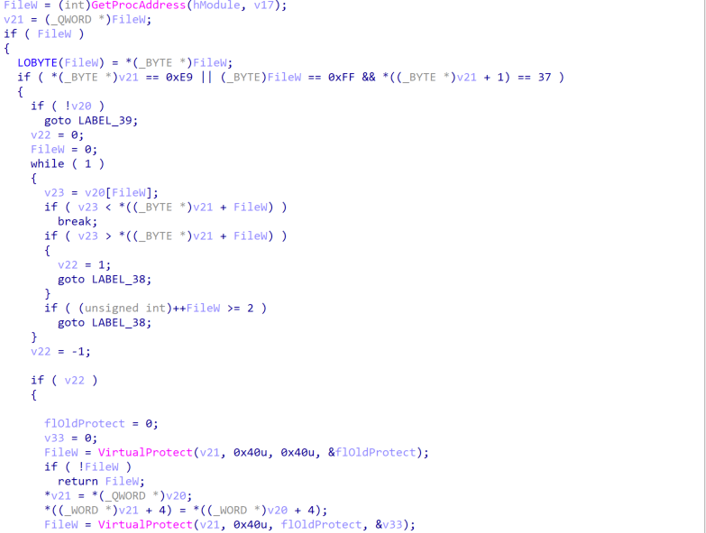
- DragonForce creates a mutex named “hsfjuukjzloqu28oajh727190”T to ensure that only one instance of ransomware is running at a single time.
- When the ransomware starts, it will attempt to create the mutex with the specified name. If the mutex already exists (i.e., another instance of the ransomware is already running), the process will fail or terminate, ensuring that only one copy of the malware is active.
- If the mutex doesn’t exist, the ransomware creates it and continues its execution. This effectively locks the system into only one active ransomware process.
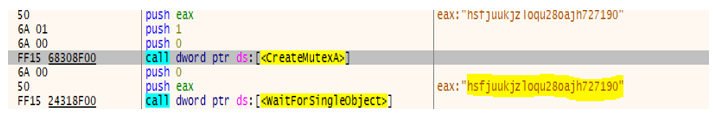
- DragonForce ransomware extracts the command-line parameters and compares them with the parameters list: -p, -m, -log, -size, and -nomutex.
-p :-Encrypt Mode – path
-m :-Encrypt Mode – all, local, net
-log :-Specify log file
-size :-Specify file encryption percentage
-nomutex :-Do not create mutex
- Through GetLogicalDriveStringW API checking each drive in the victim’s machine and taking the handle of files present in drive. The use of the GetLogicalDriveStringsW API to enumerate and access each drive on the victim’s machine is a common tactic for ransomware and other malware types that need to operate across multiple drives, especially when their goal is to encrypt files or collect data.
- It provides a string of drive letters, which represent the different storage devices on the victim’s machine, such as C:\, D:\, E:\, etc.

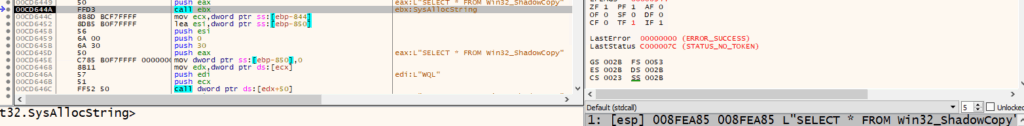
- Using WMI’s query “SELECT * FROM Win32_ShadowCopy” to extract the shadow copies and delete them using the Delete method. SELECT * FROM Win32_ShadowCopy
cmd.exe /c C:\Windows\System32\wbem\WMIC.exe shadowcopy where “ID=’%s'” delete.
Encryption Process:
- DragonForce ransomware uses ChaCha8 encryption algorithms for encrypting files with targeted extensions.
- According to file size and file extension the dragonforce will encrypt files.
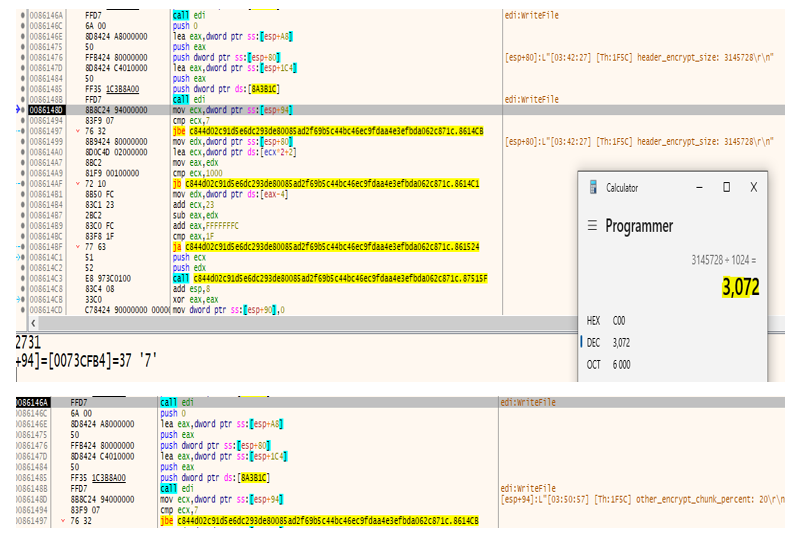
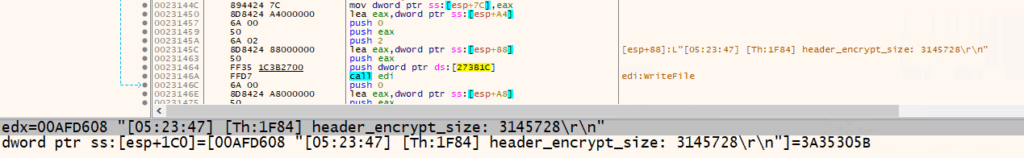
- File size < 3MB: the entire file is encrypted and 0x24 is added to the encrypted file’s footer (Full encryption).
- File size > 3MB the first 3MB are encrypted (0x26 in the footer). In the case of targeted extensions, the entire file is encrypted. (Partly encryption)
- Files with Virtual machine extensions are encrypted by 20%.
- The calculation for the encryption of files with a size of 3 MB is illustrated in the below screenshot.
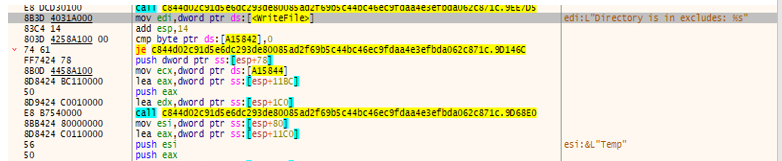
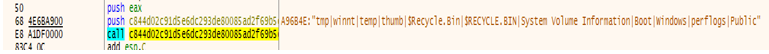
- The specific list of folders ,directory and file extensions that will be excluded from encryption routines. Below screenshot mentioned list of files and folder.
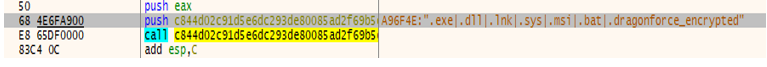
- Excluded folders: “temp, winnt, tmp, thumb, $Recycle.Bin, $RECYCLE.BIN, System Volume Information, Boot, Windows, perflogs, Public”
- Excluded file extensions: “.exe, .dll, .lnk, .sys, .msi, .bat”
- It creates the ransom note called readme.txt in every traversed directory:

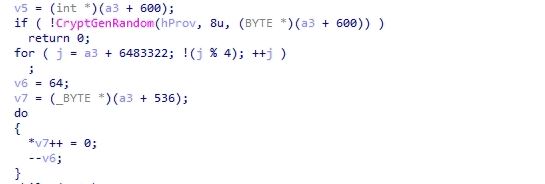
- Ransomware generates 32 random bytes and then 8 random bytes representing the ChaCha8 key and nonce respectively.
- Every file will be encrypted with a different key and nonce.
- By using the API sequence of CryptImportKey,CryptGenRandom and CryptEncrypt encrypting the files on the victim’s machine.
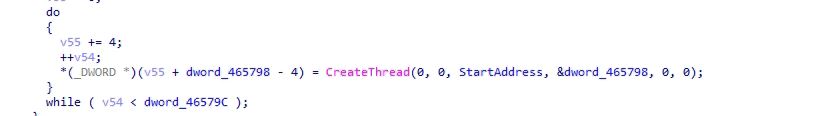
- To speed up the file system encryption operations, the executable creates multiple threads equal to the number of processors.
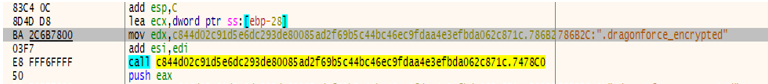
- Ransomware extensions are added to the infected files, as shown in the screenshot below.
- After encryption of each traversed directory files renamed with new names as filename.dragonforce_encrypted extension.
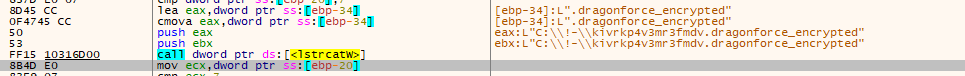
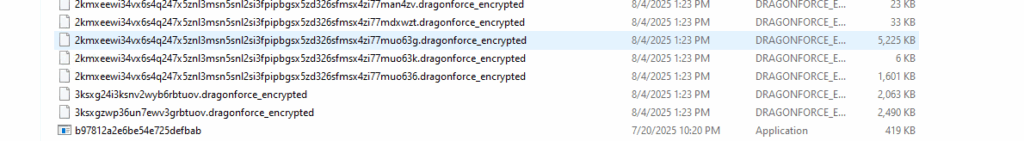
- Renaming infected files with ransomware extension as shown in the below screenshot.
- The ransomware uses Base32 encoding for filenames and appends a specific extension to the encrypted files.
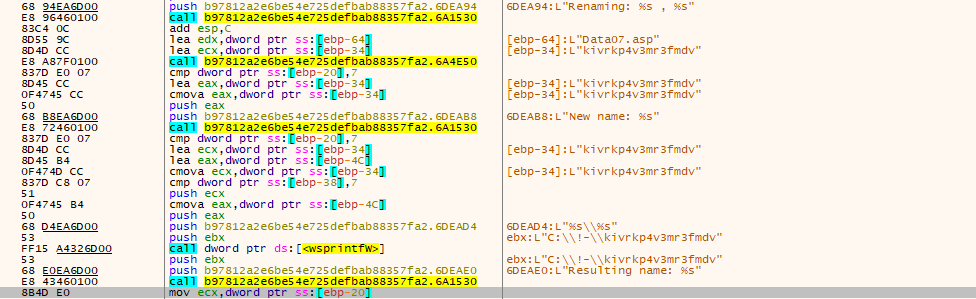
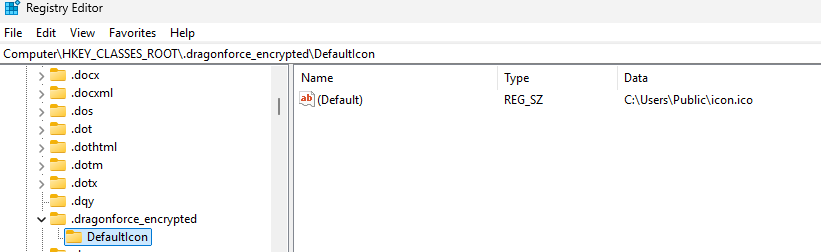
- DragonForce ransomware creates a Persistence through registry key folder name as dragonforce_encrypted under HKEY_CLASSES_ROOT using RegCreateKeyExW.
- File name icon.ico contains default registry key in public directory called as Persistence mechanism of ransomware.
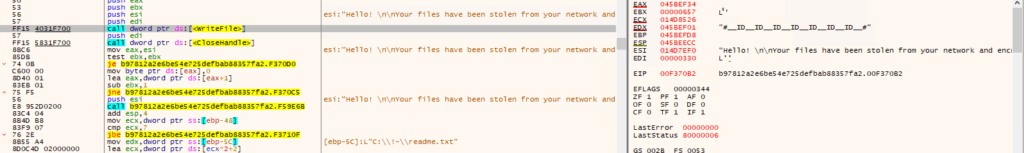
- Dropping and writing ransom note content in text file named as readme.txt for decryption of files or data on victim’s machine. After paying ransom from the user, the attacker will decrypt the victim’s machine files.
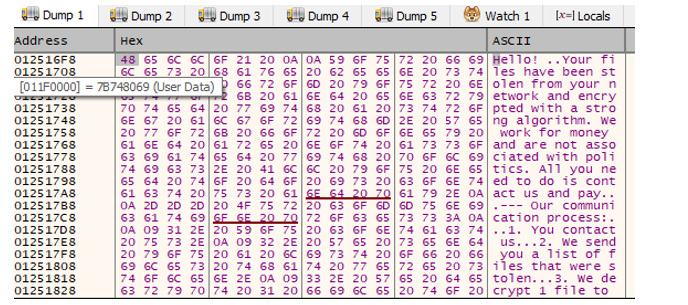
- The ransom note file is shown in the image below.
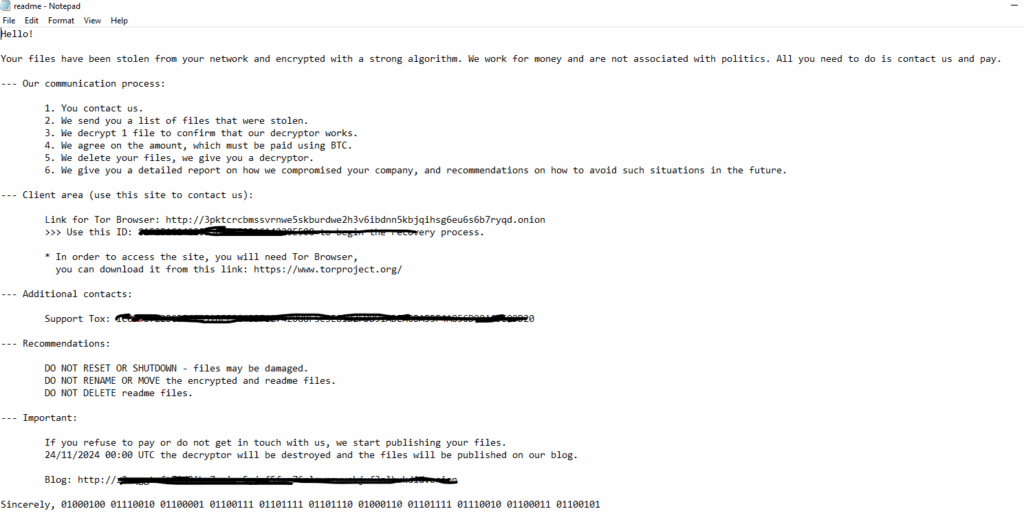
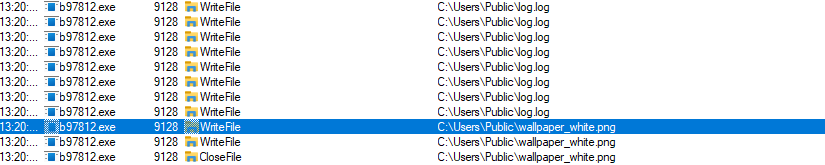
- After infection, the malware changes the screen wallpaper and drops a readme text file, as shown in the image below.
- The following is a list of targeted file extensions:
.accdb, .accdc, .accde, .accdr, .accdt, .accft, .adb, .ade, .adf, .adp, .arc, .ora, .alf, .ask, .btr, .bdf, .cat, .cdb, .ckp, .cma, .cpd, .dacpac, .dad, .dadiagrams, .daschema, .db, .db-shm, .db-wal, .db3, .dbc, .dbf, .dbs, .dbt, .dbv, .dbx, .dcb, .dct, .dcx, .ddl, .dlis, .dp1, .dqy, .dsk, .dsn, .dtsx, .dxl, .eco, .ecx, .edb, .epim, .exb, .fcd, .fdb, .fic, .fmp, .fmp12, .fmpsl, .fol, .fp3, .fp4, .fp5, .fp7, .fpt, .frm, .gdb, .grdb, .gwi, .hdb, .his, .ib, .idb, .ihx, .itdb, .itw, .jet, .jtx, .kdb, .kexi, .kexic, .kexis, .lgc, .lwx, .maf, .maq, .mar, .mas, .mav, .mdb, .mdf, .mpd, .mrg, .mud, .mwb, .myd, .ndf, .nnt, .nrmlib, .ns2, .ns3, .ns4, .nsf, .nv, .nv2, .nwdb, .nyf, .odb, .oqy, .orx, .owc, .p96, .p97, .pan, .pdb, .pdm, .pnz, .qry, .qvd, .rbf, .rctd, .rod, .rodx, .rpd, .rsd, .sas7bdat, .sbf, .scx, .sdb, .sdc, .sdf, .sis, .spq, .sql, .sqlite, .sqlite3, .sqlitedb, .te, .temx, .tmd, .tps, .trc, .trm, .udb, .udl, .usr, .v12, .vis, .vpd, .vvv, .wdb, .wmdb, .wrk, .xdb, .xld, .xmlff, .abcddb, .abs, .abx, .accdw, .adn, .db2, .fm5, .hjt, .icg, .icr, .kdb, .lut, .maw, .mdn, .mdt.
- The following is a list of targeted virtual machine file extensions:
. vdi, .vhd, .vmdk, .pvm,.vmem,.vmsn, .vmsd, .nvram, .vmx, .raw, .qcow2, .subvol, .bin, .vsv, .avhd, .vmrs, .vhdx, .avdx, .vmcx, .iso.
MITRE ATT&CK:
| MITRE Tactic | Technique | Description |
| Initial Access | Phishing | Delivers malware via spear-phishing emails |
| Execution | User Execution | Relies on victims opening malicious file attachments (scripts, or executables) delivered via phishing |
| Persistence | Registry Run Keys | Creates or modifies autorun Registry keys for persistence. |
| Privilege Escalation | Access Token Manipulation | DragonForce may also abuse token impersonation to gain system-level access |
| Defense Evasion | Obfuscated Files or Information | DragonForce obfuscates its payload by packing or encrypting parts of the code to evade detection and hinder static analysis. |
| Discovery | File and Directory Discovery | After gaining access, they recursively enumerate files and directories on compromised systems for encryption. |
| Lateral Movement | Remote Desktop Protocol | DragonForce connects to multiple internal systems over RDP to expand their foothold. RDP is used for lateral movement within the network. |
| Command & Control | Application Layer Protocol: Web Protocols | C2 communication is established using HTTP. |
| Impact | Data /System Encrypted | Deploys ransomware to encrypt files on victim systems, Once encryption is complete, the ransomware drops ransom note files on disk and often changes the desktop wallpaper to a ransom message |
Conclusion:
- DragonForce ransomware is a highly dangerous threat. It demonstrates typical ransomware behavior, such as file encryption, ransom demands, and communication with a C2 server. However, it also exhibits advanced evasion techniques like obfuscation, anti-analysis.
- DragonForce ransomware deploys payloads derived from leaked LockBit3.0 and Conti source code. The encryption percentage of a file is determined by both file size and whether the extension is included in the ransomware’s targeted list.
IOC:
| SHA256 | c844d02c91d5e6dc293de80085ad2f69b5c44bc46ec9fdaa4e3efbda062c871cb9bba02d18bacc4bc8d9e4f70657d381568075590cc9d0e7590327d854224b32 |
| File Created | C:\Users\Public\log.logC:\Users\Public\wallpaper_white.pngC:\Users\Public\icon.icoreadme.txt |
| Registry key | HKCR\.dragonforce_encrypted |
| Mutex | hsfjuukjzloqu28oajh727190 |
Our in-depth analysis of DragonForce ransomware builds on the foundational research contributed by the broader security community, including detailed technical reporting by SentinelOne, Group-IB, BlackPoint Cyber, Hybrid Analysis, and Resecurity. We are grateful to these independent and professional researchers whose insights have significantly advanced collective understanding of this evolving threat.